11 Best VPNs Rated in 2024 (150+ VPNs Tested)
Hundreds of VPNs claim to be the best, but they can’t all be the fastest, safest, and cheapest. To get a conclusive (and honest) answer, my team and I rigorously tested 157 VPNs over 3 months and ranked them against the following must-have criteria:
- Advanced security and data privacy features
- Fast speeds with a global network of servers
- Accesses popular sites (like Netflix and Disney+) and P2P support
- Dedicated, easy-to-use apps for Windows, Mac, Android, iOS, and more
- Good value for money, plus 24/7 customer support
Overall, ExpressVPN is the #1 VPN in 2024, with top-tier security and privacy, fast speeds on its global network, and more. Plus, you can try ExpressVPN completely risk-free!
Try ExpressVPN risk-free today
Quick Guide: The Best VPNs in 2024
- ExpressVPN — #1 VPN in 2024 with excellent speeds, advanced privacy and security features, and 3,000+ servers for streaming and torrenting. You can try ExpressVPN risk-free today!
- CyberGhost — Premium VPN for fast streaming and secure torrenting for desktop users, but mobile apps for Android and iOS are more limited.
- Private Internet Access — Best for advanced users due to customizable network, privacy, and security settings, but headquartered in the United States.
- NordVPN — Unique security features plus proprietary NordLynx protocol provides top security and speeds, but apps aren’t as intuitive for beginner users.
- Surfshark — Detailed interface makes it easy to choose a reliable, secure server, but causes slowdowns and high ping over long-distance connections.
Plus 7 more great VPNs made it onto the list! Jump here to read more.
The Best VPNs in 2024 — Tested and Reviewed
1. ExpressVPN — #1 VPN for Speed, Security, and Privacy on All Devices
Quick Look: ExpressVPN Results
| Speed | Excellent — Fast streaming, torrenting, and gaming speeds with unlimited bandwidth |
| Security | Advanced — AES 256-bit encryption, TrustedServer technology, automatic kill switch, split tunneling, no IP address leaks, and auditing |
| Servers | Extensive — A network of 3,000+ servers in 105 countries |
| Privacy | Strict — Located in the British Virgin Islands outside of 5/9/14 Eyes with proven no-logs policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, Chromebook, Amazon Fire TV, Amazon Fire Stick, Kindle Fire, Roku, BlackBerry (Priv and DTEK50), Nook, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, Spotify, HBO Max, Kodi, Sky Go, Sling TV, FuboTV, YouTube TV, DAZN, ESPN+, Showtime, and more |
| Torrenting | Supported — Global network of 3,000+ servers all allow P2P |
| Customer Support | Quick response 24/7 via live chat, online form, and email |
| Device Connections | 8 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ No kill switch on the iOS app |
| Best Price | $6.67/month for a 1-year + 3 months plan |
2024 Update! ExpressVPN has dropped prices for a limited time to a crazy $6.67 per month for the 1-year plan + 3 months free (you can save up to 49%)! This is a limited offer so be sure to grab it now before it's gone. See more information on this offer here.
ExpressVPN is the #1 choice in 2024, with highly secure encryption and privacy protection features. You can browse the internet anonymously, overcome firewalls, and avoid online restrictions.
Plus, ExpressVPN is one of the few VPNs that work consistently in China, thanks to obfuscation on every server. This works by hiding your VPN use, so you can access the uncensored web without triggering government firewalls.
I found ExpressVPN supports a range of quality encryption protocols. The default choice is its proprietary Lightway protocol, and for good reason — it’s a lightweight, secure, and speedy choice that provides the fastest connections. You can also choose from OpenVPN, IKEv2, and L2TP/IPsec.
ExpressVPN has the following security and privacy features:
- AES 256-bit encryption and 4096-RSA key — set up and authenticate the encrypted tunnel with military-grade protection.
- Kill switch — automatically blocks your internet until you safely reconnect to a server.
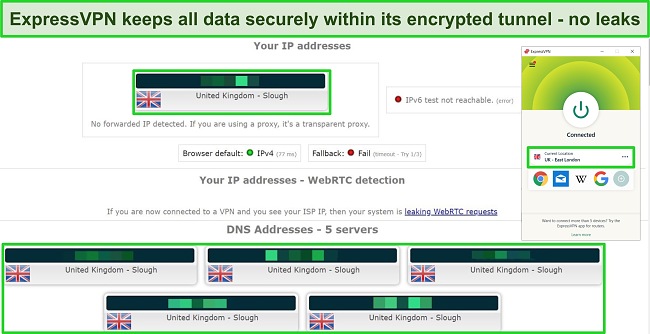
- Leak protection — stops IP, DNS, and WebRTC leaks to secure your personal data.
- TrustedServer Technology — uses RAM-based servers that automatically wipe all data with every scheduled reboot.
- A third-party audited no-log policy — proven when Turkish authorities attempted to retrieve user data from ExpressVPN by physically seizing servers and found nothing.
I like that all 3,000+ ExpressVPN servers support torrenting and streaming, and I had fast speeds no matter which ExpressVPN server I used. I ran speed tests on multiple servers in the US, UK, Germany, and Australia. Download speeds were consistently high, dropping only 16%-25% from baseline speeds in all locations.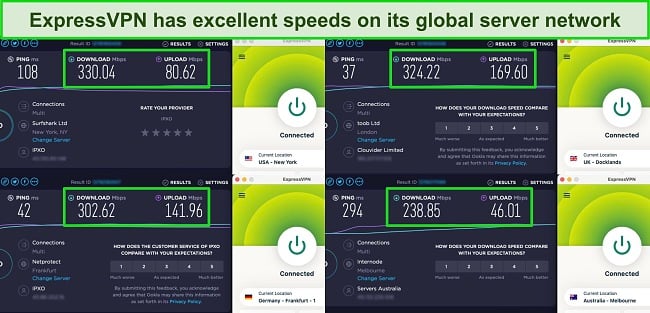
I didn’t have any issues torrenting large files, playing online games, or streaming shows and movies in UHD. On multiple different servers, ExpressVPN can easily access:
| Netflix (US, UK, Japan, and more) | Disney+ | Hulu | Amazon Prime Video | HBO Max | BBC iPlayer |
| CBS All Access | Hotstar | Showtime | DAZN | ESPN | Paramount+ |
| Peacock | Discovery+ | fuboTV | Sling TV | YouTube TV | …and more! |
You can’t install ExpressVPN directly on all devices, but you can use ExpressVPN’s MediaStreamer function. It’s a DNS service that lets the VPN run on almost all devices where you can manually input network settings. I found the setup very simple, testing it on my PlayStation and successfully streaming Netflix without issue.
In terms of usability, ExpressVPN is ideal for both beginners and advanced VPN users. The interface is simple and easy to navigate, with identical native apps for multiple platforms. Installation and setup take less than a minute. Plus, ExpressVPN’s browser extensions give you full control of the VPN app from your browser — no other VPN app offers this.
ExpressVPN starts its plans at $6.67 a month for a 1-year + 3 months plan. You can use standard payment options like debit and credit cards or PayPal, but if you prefer an anonymous option, you can also choose Bitcoin.
All plans are backed by a 30-day money-back guarantee, so you can try ExpressVPN risk-free. The VPN has a “no questions asked” policy, so you won’t need to give a reason if you change your mind. I tested this myself and it was easy. I wasn’t pressured to stay, and my request was processed quickly; I got a full refund in 5 days.
You can find full testing results in the ExpressVPN review for a detailed analysis of speed, security, user experience, and more.
2. CyberGhost — Best for Fast Streaming and Secure Torrenting on Specialty Servers
Quick Look: CyberGhost Results
| Speed | Good — Optimized servers offer HD streaming and speedy torrenting |
| Security | Advanced — 256-bit AES encryption, kill switch, no data leaks, and in-built ad blocker |
| Servers | Large — A network of 11,800+ servers in 100 countries |
| Privacy | Strict — Based in Romania (outside of 5/9/14 Eyes) with an audited no-logs policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, Android TV, Amazon Fire TV, Amazon Fire Stick, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, HBO Max, Kodi, Sling TV, FuboTV, YouTube TV, Vudu, Spotify, Showtime, and more |
| Torrenting | Supported — Optimized servers for secure P2P activity |
| Customer Support | Quick response 24/7 via live chat, online form, and email |
| Device Connections | 7 |
| Money-Back Guarantee | 45 days |
| Minor Cons | ✘ iOS app has no ad blocker ✘ No optimized P2P servers available on iOS or Android apps |
| Best Price | $2.03/month for a 2-year + 4 months plan |
2024 Update! You can subscribe to CyberGhost for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 84%)! This is a limited offer so grab it now before it's gone. See more information on this offer here.
CyberGhost makes streaming and torrenting easy by offering a range of optimized servers. All optimized servers are automatically configured for the best speeds and performance, so you don’t need to set up anything manually to connect.
You can find CyberGhost’s streaming servers in the “For streaming” tab. Each server is optimized for a specific streaming platform, guaranteeing a working connection.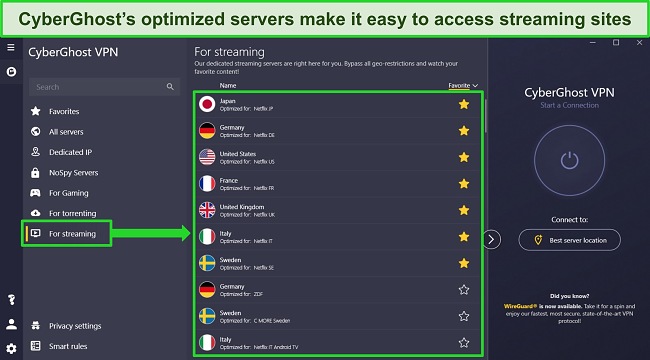
Rigorous testing confirms CyberGhost’s optimized streaming servers work with:
| Netflix (US, UK, Germany, and more) | Disney+ | Hulu | Amazon Prime Video | BBC iPlayer |
| CBS All Access | Hotstar | Showtime | ESPN | Peacock |
| Discovery+ | fuboTV | Crunchyroll | Globo | …and more! |
During tests, CyberGhost’s servers successfully connected every time, with average speeds between 65Mbps to 70Mbps — around 40% slower than without a VPN. With these speeds, streaming was buffer-free and UHD quality.
The optimized servers for torrenting have a similar setup. I chose a nearby server in the UK for the best speeds, and my 2GB file finished downloading in less than 4 minutes.
CyberGhost also has the following powerful security and privacy features:
- 256-bit AES encryption — which keeps all data secure within the encrypted tunnel, maintaining top-tier protection at all times.
- A kill switch — is available on all apps in case the VPN connection is interrupted.
- A strict zero-logs policy — that has been independently audited to confirm CyberGhost never logs or stores your data.
- Ultra-private “NoSpy” servers — are located in Romania, which doesn’t have any electronic surveillance laws.
- Secure protocols — including WireGuard, OpenVPN, and IKEv2.
Additionally, CyberGhost offers dedicated IP addresses for an extra monthly fee. This reduces the chance you’ll experience IP bans due to other users or issues connecting to networks with IP restrictions — ideal for business owners, online banking and trading, securely working from home, and more.
You’ll find settings to enable blocking for ads, trackers, and malware in CyberGhost’s app. However, I found CyberGhost will only block ads with malicious code rather than all ads, so you’ll still see ads on sites like YouTube.
I was impressed by CyberGhost’s Smart Rules feature, which automates the VPN to run based on your preferences. I configured CyberGhost to connect to a specific server and start my torrent client automatically, connect to a server anytime I use public WiFi, and exclude apps from the VPN tunnel.
CyberGhost is a top VPN for Windows, Mac, and Linux desktop devices, and it’s a bargain price at only $2.03 a month for the 2-year + 4 months plan. However, if you travel to China or other countries with restrictive internet laws, you may want to consider ExpressVPN — CyberGhost often struggles to bypass internet censorship in these countries.
You can test CyberGhost risk-free for up to 45 days with its money-back guarantee. If you change your mind about subscribing, you can request a full refund from customer support. I tested this myself by contacting support via the 24/7 live chat and was impressed by the no-questions-asked confirmation. I had the money back within a week.
Read the full CyberGhost review for a deep dive into speed, privacy, security, and more features.
3. Private Internet Access — Best for Advanced Users With Customizable Security Settings
Quick Look: PIA Results
| Speed | Average — Inconsistent speeds depending on server location |
| Security | Advanced — Military-grade encryption, kill switch, leak protection, and blocker for ads, trackers and malware |
| Servers | The largest selection — A network of 35,000+ servers in 91 countries |
| Privacy | Strict — Audited no-logs policy |
| Native Apps For: | Most main devices — Android, iPhone, Windows, Mac, Linux, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, BBC iPlayer, Crunchyroll, SkyTV, Sling TV, fuboTV, CBS All Access, and more |
| Torrenting | Supported — All 35,000+ servers in the network support P2P |
| Customer Support | Quick response 24/7 via live chat, online form, and email |
| Device Connections | unlimited |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ Not every server unblocks Netflix US or Hulu ✘ Headquartered in the US, part of the 5 Eyes Alliance |
| Best Price | $2.03 a month on a 2-year + 4 months plan |
2024 Update! You can subscribe to PIA for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 83%)! This is a limited offer, so grab it now before it's gone! See more information on this offer here!
Private Internet Access (PIA) offers advanced privacy and security features you can tailor to your needs. The VPN has customization options on Android, iOS, Windows, and Mac apps, including encryption, protocols, split tunneling, and more.
To provide top-tier security and privacy, PIA has the following features:
- SOCKS5 and Shadowsocks proxies — accessible through a multi-hop connection to obfuscate your connection, helping avoid network restrictions.
- Data leak protection — protects your activity from prying eyes by stopping accidental DNS and IP leaks.
- Kill switch — automatically cuts access to the internet to ensure data privacy if the connection is interrupted.
- Strict no-log policy — independently audited to prove PIA’s claim it doesn’t keep any logs or data.
You can choose which data encryption you want: AES-128, AES-256, or no encryption at all (although your login details will still be encrypted and your IP address remains hidden). Both 128- and 256-bit encryption are unbreakable, so it’s nice to have the option between faster speeds or stronger encryption.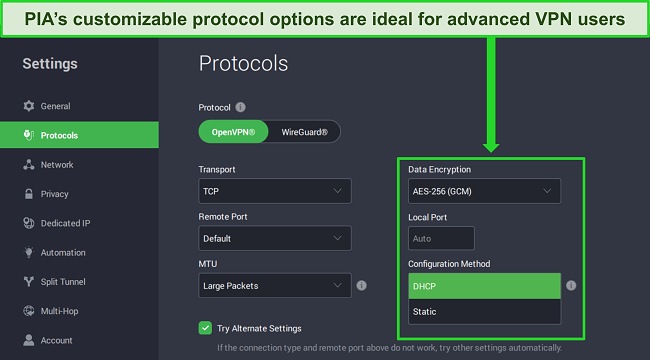
PIA offers OpenVPN and WireGuard on all its devices. WireGuard is a fast, lightweight alternative to OpenVPN, although OpenVPN is more well-established. These are good choices to have, but a few more protocol options would be nice.
Its MACE ad and malware blocker surprised me with how effective it is. I connected to several websites known to host tons of ads (like Forbes) and was pleasantly surprised to see no ads had loaded on the page.
You may be concerned about PIA’s headquarters in the US, a founding member of the Eyes Alliance intelligence-sharing network. Fortunately, PIA’s independent audit and real-life proof show that there’s no need to worry about your data — the Russian government previously seized PIA’s servers but was unable to recover any data.
PIA’s commitment to privacy makes it a good option for anonymous browsing (it’s compatible with Tor) and safe torrenting. Every server allows P2P file-sharing, which is convenient as you don’t have to limit yourself. Plus, PIA’s built-in SOCKS5 and Shadowsocks multi-hop features add extra protection to your torrenting activity.
During tests, PIA’s optimized streaming servers easily accessed:
| Netflix | Disney+ | Amazon Prime Video | Hulu | CBS All Access |
| Hotstar | Showtime | ESPN | HBO Max | …and more! |
PIA’s speeds were reliably fast, and I could stream in HD quality after a few seconds of buffering. However, PIA couldn’t access BBC iPlayer.
If you want a VPN that offers full control over privacy and security settings, I highly recommend PIA. It’s an affordable option, too, with subscriptions starting at just $2.03 a month for its 2-year + 4 months subscriptions. You can even pay with cryptocurrency for total anonymity.
I suggest you try PIA risk-free, as you can get a full refund within 30 days if you change your mind. I found the refund process easy, simply contacting customer service online to request my money back. I had my refund in less than a week.
You can read more about PIA in the full-length review here and find out more about its privacy policy, security features, and subscription plans.
4. NordVPN — Unique Features Provide Top-Tier Security and Network Accessibility
Quick Look: NordVPN Results
| Speed | Fast — Impressive speeds on local and long-distance connections |
| Security | Advanced — AES-256-bit encryption, kill switch, Threat Protection, and leak protection |
| Servers | Large selection — A network of 6,300+ servers in 110 countries |
| Privacy | Strict — Based in Panama (outside the 5/9/14 Eyes) with an audited no-logs policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, and more |
| Torrenting | Supported — Dedicated P2P servers allow torrenting |
| Customer Support | Quick response 24/7 via live chat and email |
| Device Connections | 10 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ Very few obfuscated servers ✘ Willing to share personally-identifiable data if requested by law |
| Best Price | $3.09/mo (2-year + 3 months plan) |
NordVPN’s unique features heighten your online security and network accessibility. These include:
- Threat Protection — is advanced malware protection and ad and tracker blocking which secures your devices, even when the VPN isn’t connected.
- Meshnet — lets you access your devices or home network when abroad by creating a secure encrypted tunnel between devices — for example, you can connect to your home PC with your smartphone when traveling to stream on your local accounts, share files, play games, or work remotely.
- Dark Web Monitor — sends you alerts and prompts security changes if your personal data is exposed online, checking for email addresses, passwords, contact details, and more.
All of NordVPN’s subscription plans come with these features, and getting them up and running is a straightforward process. To activate Threat Protection and Dark Web Monitor, you simply need to switch them on. As for Meshnet, I was able to connect various devices and create my own network in less than 5 minutes.
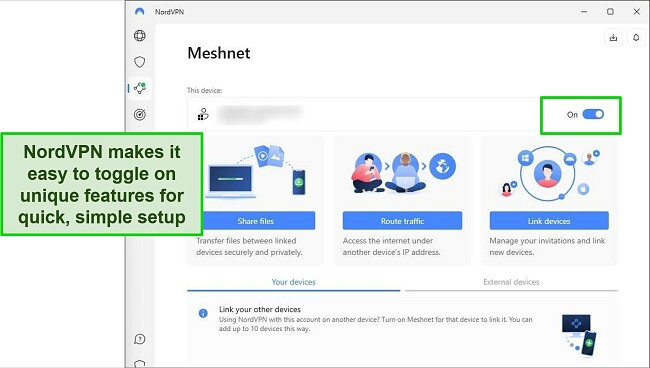
To further enhance your online security and privacy, NordVPN provides the following features for its server connections:
- AES-256-bit encryption — all servers are protected by military-grade encryption to ensure your data is secure and anonymous.
- Kill switch — blocks access to the internet to prevent unprotected connections that could expose your data.
- Auto-connect — detects when you’re using an unsecured network and connects to a server to maintain security.
- Audited zero-log policy — independently verified that NordVPN does not log or store your data.
I was impressed with NordVPN’s protocol selection, which includes its proprietary NordLynx protocol. NordLynx uses a WireGuard template plus a double NAT (Network Address Translation) system for top speeds and impenetrable security.
Using NordLynx, my speeds with NordVPN were consistently fast across its global server network. During tests, my speeds reduced by just 20% on average, even when using long-distance connections. This made it easy to download torrents, play online games, browse the web, and stream on the following services in UHD quality:
| Netflix | Amazon Prime Video | Disney+ | Hulu | BBC iPlayer |
| Showtime | ESPN | DAZN | HBO Max | …and more! |
You’ll find NordVPN also has optimized servers for torrenting, Onion Over VPN, and multi-hop connections. I found this made it simple to choose exactly the right server for my online activities.
However, I was disappointed to find NordVPN has very few obfuscated servers in its network. This is a premium feature other VPNs have as standard on all server connections, making it easy to avoid proxy detection that blocks access to websites and services. With a limited number, you may not always be able to connect to an obfuscated option.
Fortunately, NordVPN is a reasonably priced option (plans start at $3.09/month) and all plans are backed by a 30-day money-back guarantee. If you change your mind, you can contact the 24/7 live chat for a refund. I did and had my money back within 7 days.

5. Surfshark — Feature-Packed Budget VPN Ideal for Fine-Tuning Your Connection
Quick Look: Surfshark Results
| Speed | Average — Fast global speeds but unexpectedly high ping |
| Security | Advanced — AES-256-bit encryption, kill switch, leak protection, and more |
| Servers | Good — A network of 3,200+ servers in 100 countries |
| Privacy | Strict — Based in the Netherlands (part of the 9 Eyes Alliance) with an audited zero-log policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, and more |
| Torrenting | Supported — Optimized P2P connections in torrent-friendly locations |
| Customer Support | Quick response 24/7 via live chat and email |
| Device Connections | unlimited |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ Headquartered in a 9 Eyes Alliance location ✘ The expensive choice for short-term plans |
| Best Price | $2.29/mo (2-year + 2 months plan) |
Surfshark’s apps are packed with customizable features, ideal for fine-tuning your connections. These features include personalized multi-hop connections, a rotating IP address, split tunneling, and customizable auto-connect. Configuring Surfshark to my needs makes me feel confident my VPN connection is suitable for my online activities.
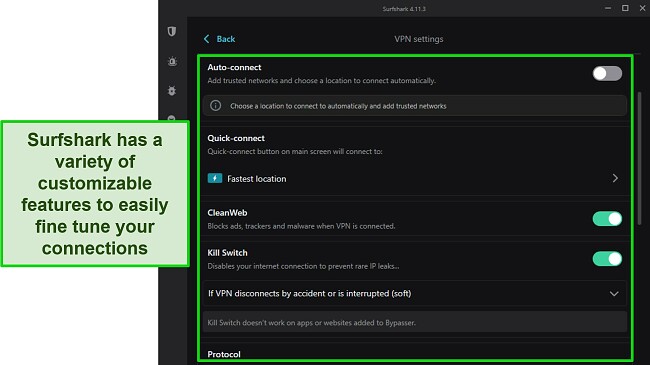
Better still, Surfshark is a low-cost option, especially considering its rich feature set. You can subscribe to the VPN for as little as $2.29/month for a 2-year + 2 months plan, saving a huge 85% from its regular prices.
For beginner users, Surfshark’s apps clearly describe what each feature does, and most can be switched on and off with a single click. This makes configuring the apps simple, taking just a few minutes to create a personalized connection.
Alongside the high level of customizability, Surfshark ensures your connections are always secure and private with the following high-quality features:
- AES-256-bit encryption — protects your data and online activity with military-grade security on all server connections.
- Leak protection — stops accidental DNS, IP, and WebRTC leaks from exposing your true location and personal data.
- CleanWeb — blocks ads, trackers, and malicious websites from collecting your online movements or infecting your devices with malware.
- Audited zero-log policy — proves Surfshark’s claims that your data is never logged or stored when connected to the VPN’s server network.
I was pleased to find Surfshark supports fast and secure connection protocols, including WireGuard, OpenVPN, and IKEv2 for mobile devices. These protocols are all designed to ensure smooth, lag-free connections that keep your data protected. During tests, I found WireGuard provided the most reliable and fastest connections.
Using WireGuard ensured my speeds with Surfshark were consistently fast across its global network. On average, Surfshark reduced my connection speed by just 20%, making it fast enough for quick torrenting, UHD streaming, and secure browsing on all servers. I didn’t experience any slowdown due to congestion, and my connection remained steady.
With reliably fast speeds, Surfshark is a solid choice for accessing your favorite streaming services when you’re traveling. During tests, Surfshark could connect to the following services with ease:
| Netflix | Disney+ | Amazon Prime Video | Hulu | BBC iPlayer |
| Showtime | ESPN | DAZN | HBO Max | …and more! |
The only issue with Surfshark is that ping on some servers is unexpectedly high. My ping occasionally increased by more than 300%, making it near impossible to play online games or video chat with friends and family. I recommend only using Surfshark’s local servers for gaming and video calls, as these have a lower ping rate overall.
All of Surfshark’s plans are backed by a 30-day money-back guarantee, making it easy to test the VPN risk-free. If you’re not fully satisfied, simply contact customer service for a refund within 30 days. I requested my money back using the 24/7 live chat and had my full refund in 7 days.
6. PrivateVPN — Simple VPN With Reliable Servers for Unblocking Global Content (Even in China)
Quick Look: PrivateVPN Results
| Speed | Good — Smooth browsing, streaming, and torrenting speeds |
| Security | Advanced — Military-grade encryption, kill switch, and leak protection |
| Servers | Small — A network of 200+ servers in 63 countries |
| Privacy | Strict — Based in Sweden (inside the 5/9/14 Eyes) with a no-logs policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, Amazon Fire Stick, Amazon Fire TV, Android TV, and routers |
| Proven to Unblock: | All major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, HBO Max, Sling TV, CBS All Access, Fox Go, and more |
| Torrenting | Supported — Entire server network supports P2P activity |
| Customer Support | Slow response via live chat, online form, and email |
| Device Connections | 10 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ No kill switch on iOS ✘ No browser extensions are available ✘ Live chat isn’t always available |
| Best Price | $2.00 per month for a 3-year term |
PrivateVPN is a high-performing VPN, although I was skeptical about its small network of 200+ servers, anticipating overcrowding and slower speeds. However, after thoroughly testing PrivateVPN, I found my initial assumptions were wrong.
You can access over 7,000 individual IP addresses with PrivateVPN’s reliable server network, so you don’t need to worry about IP availability. Plus, PrivateVPN supports torrenting on the entire network, so there’s no need to look for specific servers.
I learned that PrivateVPN’s Toronto and Hong Kong servers work in China, thanks to the Stealth VPN feature. This obfuscates your VPN connection, making it look like regular internet traffic. Stealth VPN helps you avoid VPN detection technology, even in countries with strict internet regulations.
Despite the smaller network, I didn’t experience speed or connection problems in my tests. In fact, I was impressed with PrivateVPN’s performance — my network slowed by about 60%, but my speeds were fast enough for uninterrupted streaming and torrenting.
To keep your online activity anonymous and secure, PrivateVPN has:
- Military-grade encryption — protects your data with AES-256-bit encryption on every server connection.
- A kill switch on all apps except iOS — and Connection Guard settings on Windows let you customize which apps are protected by the kill switch.
- IP, DNS, and WebRTC leak protection — keep all data within the encrypted tunnel to avoid compromising your security.
- Strict zero-log policy — ensures your data is never stored while you’re connected to PrivateVPN’s network.
I was impressed by PrivateVPN’s protocols, with OpenVPN with UDP/TCP, L2TP/IPsec, PPTP, and IKEv2 available. Each of these offers a trade-off between security, speed, supported devices, and other benefits, depending on your VPN use.
PrivateVPN’s servers can access Netflix libraries in 19 countries, including the US, UK, Canada, Australia, France, Brazil, and Sweden.

During tests, PrivateVPN’s optimized servers could also connect to the following services:
| Disney+ | Amazon Prime Video | BBC iPlayer | CBS All Access | BBC iPlayer |
| Hotstar | Showtime | ESPN | HBO Max | …and more! |
Unfortunately, PrivateVPN’s customer support team is slow. It took 5 minutes to speak to an agent despite being first in the queue. I tried to ask another question a few minutes later, but the live chat option had disappeared. I could only fill in an online form and wait for an email reply. Fortunately, I received a detailed response 8 minutes later.
Subscriptions for PrivateVPN start at $2.00 a month for its 3-year plans, making it one of the most affordable monthly VPNs. You can even subscribe using Bitcoin.
You can use the 30-day money-back guarantee to try PrivateVPN without risk. It’s easy to get a refund if you change your mind. I sent an email to support@privatevpn.com and stated I no longer needed the service. I had my money back in 5 business days.
Check out the PrivateVPN review for an in-depth look into security and privacy features, servers, user experience, and more.
7. IPVanish — Powerful Security Features and Good for Torrenting With Free SOCKS5 Proxy
Quick Look: IPVanish Results
| Speed | Good — Fast speeds for torrenting and casual browsing |
| Security | Advanced — 256-bit AES encryption, kill switch, and leak protection |
| Servers | Moderate — A network of 2,400+ servers in 55 countries |
| Privacy | Strict — Based in the US (inside the 5/9/14 Eyes) with a no-logs policy |
| Native Apps For: | Most main devices — Android, iPhone, Windows, Mac, Linux, Amazon Fire TV, Amazon Fire Stick, and select routers |
| Proven to Unblock: | Most major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, Kodi, and more |
| Torrenting | Supported — Every server supports torrenting and a SOCKS5 proxy is available for free |
| Customer Support | Fast response 24/7 via live chat, phone, email, and online form |
| Device Connections | unlimited |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ No cryptocurrency payment options ✘ Can’t reliably unblock Netflix ✘ No ad, malware, or tracker blocker |
| Best Price | $2.99/mo (2-year plan) |
IPVanish is a solid option if you need a VPN for torrenting or want greater privacy online. You get unlimited bandwidth and fast speeds, and the VPN protects your browsing activities with its strict no-logs policy.
Plus, it’s easy to find the best server connections with IPVanish’s simple-to-navigate interface. IPVanish will automatically connect you to the fastest option in your chosen city or country, or just the best server overall.
During tests, I downloaded torrent files using servers in Switzerland, Sweden, and Spain. My torrenting speeds were excellent, with a minimal 20% slowdown from my base speed. My connection remained steady with zero interruptions.
I also tested the free SOCKS5 proxy that offers additional speed and anonymity, although it leaves your traffic unencrypted. I found it simple to set up with my torrent client, as IPVanish has step-by-step guides available on its help site. I strongly recommend using the proxy in combination with the VPN to lower the risk of online threats.
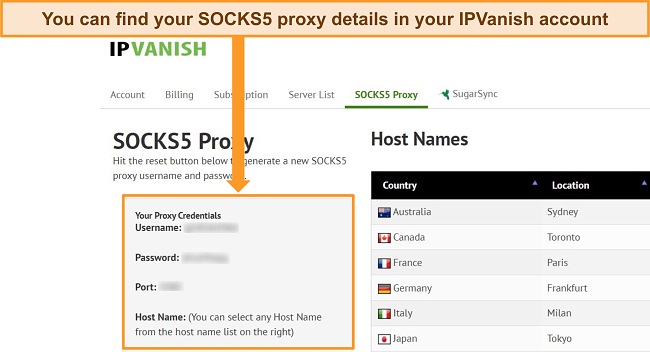
IPVanish protects your online activity using:
- AES 256-bit encryption — keeps your data protected within the secure tunnel, away from hackers and trackers.
- Data leak protection — stops IP, DNS, and WebRTC leaks from compromising your online security.
- Secure connection protocols — including OpenVPN, IKEv2, L2TP, and IPSec.
- A kill switch — protects your privacy if your connection is interrupted.
IPVanish is based in the US, which may concern you if you’re cautious about government overreach. However, recent independent audits confirm IPVanish’s zero-log policy is accurate, so you can rest assured your data is secure and anonymous.
Despite the fast speeds and strong security measures, IPVanish isn’t the best VPN for streaming. During tests, it took several server connections to access Netflix US (New York and Chicago failed, but Boston worked). IPVanish can successfully connect to:
| Disney+ | Amazon Prime Video | BBC iPlayer | CBS All Access |
| fuboTV | Showtime | ESPN | …and more! |
It’s worth noting that IPVanish fails to work in China and the UAE. If you’re looking for a VPN that offers this functionality, you’re better off choosing ExpressVPN, which consistently bypasses the Great Firewall.
IPVanish is well-priced for its strong security and impressive server speeds, with subscriptions starting at $2.99 a month for a 2-year plan. You can pay with a credit card or PayPal, but there are no anonymous options like cryptocurrency.
You can test IPVanish risk-free as it’s backed by a 30-day money-back guarantee, and canceling is easy — just log in to your account on the website, cancel your subscription and your refund will be automatically processed.
Read the in-depth IPVanish review for more information on its speed, servers, security, and more.
8. PureVPN — Quantum-Resistant Encryption Keys Fully Protect Your Data
Quick Look: PureVPN Results
| Speed | Average — Solid speeds but high ping on distant servers |
| Security | Advanced — AES 256-bit encryption, kill switch, and leak protection |
| Servers | Large — A network of 6,000+ servers in 65 countries |
| Privacy | Excellent — Based in the British Virgin Islands (outside the 5/9/14 Eyes) and independent privacy audit |
| Native Apps For: | Most major devices — Android, iPhone, Windows, Mac, and Linux |
| Proven to Unblock: | Most major streaming platforms — Netflix, Disney+, Amazon Prime Video, and more |
| Torrenting | Supported but lacking — Less than half of PureVPN’s servers support torrenting, and noticeable gaps in coverage |
| Customer Support | Quick response 24/7 via 24/7 live chat, online form, and email |
| Device Connections | 10 |
| Money-Back Guarantee | 31 days |
| Minor Cons | ✘ High ping and slow speeds on virtual servers ✘ DDoS protection and port forwarding only available at an extra cost ✘ Email ticketing is unreliable |
| Best Price | $2.03/mo (2-year + 3 months) |
PureVPN’s Quantum-Resistant Encryption protects you from the latest threats. As quantum computing becomes more popular, so do quantum cyber threats. By implementing Quantum-Resistant Encryption, PureVPN is future-proofing your protection. This reassures me that I can continue to use PureVPN and maintain a high level of security.
All of PureVPN’s 6,000+ servers are supported by:
- Military-grade encryption — protects your data against hackers, spies, and third-party trackers.
- Kill switch — automatically available on every supported platform app, preventing data leaks if the VPN connection is interrupted.
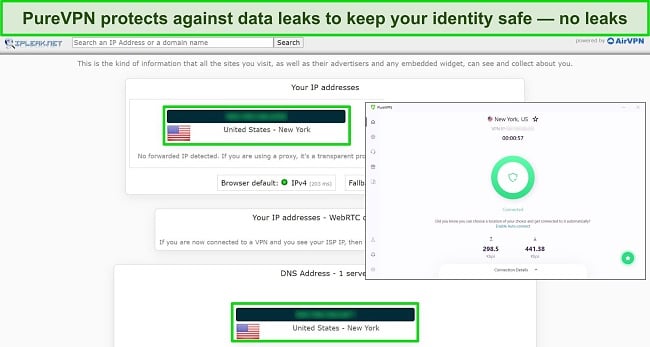
- Data leak protection — stops IPv4, IPv6, DNS, and WebRTC leaks to ensure your data is never exposed.
- Strict zero-log policy — verified by an independent audit, PureVPN never logs or stores your personally identifiable data.
PureVPN also offers split tunneling and port forwarding, extra features that allow greater control over your VPN connection. I found split tunneling particularly useful for encrypting my online banking while streaming on my local accounts, while port forwarding helped improve torrenting speeds.
In terms of overall speeds, PureVPN doesn’t significantly impact speeds, even on distant server connections. My speeds dropped around 20% on average, which is surprisingly low for a budget VPN (subscriptions start at $2.03 a month for a 2-year + 3 months plan). I recommend using the WireGuard to keep speeds reliably fast when you access:
| Netflix | Hulu | BBC iPlayer |
| Amazon Prime Video | HBO Max | …and more! |
PureVPN has an excellent 24/7 live chat feature, which can be accessed through the website and the app. This made it very easy to connect to a customer service agent who always responded promptly and thoroughly to my questions. However, I never got a response to my email ticket, so I can’t recommend using email to contact customer support.
I was disappointed to find PureVPN allows torrenting on less than half of its 6,000+ servers. There are noticeable gaps in coverage (regions like Africa, Asia, and Oceania have very limited P2P connections), and some locations with zero torrenting servers. This can cause user congestion and slow downloads if there are no P2P servers near your location.
You can try PureVPN risk-free on all your devices, as it has native apps for Windows, Mac, Android, iOS, and more. Plus, PureVPN is backed by a 31-day money-back guarantee, so you can get a full refund if you change your mind. However, it can take several days to get confirmation, so make sure you leave plenty of time if you want a refund.
You can read the full PureVPN review here to find more details about its security and privacy features, customer service, payment methods, and more.
9. Proton VPN — Built-In Tor Support to Keep Your Activities Private
Quick Look: Proton VPN Results
| Speed | Good — Reliably fast for streaming, torrenting, and browsing |
| Security | Advanced — 256-bit AES encryption, kill switch, and leak protection |
| Servers | Small — A network of 4,690+ servers in 71 countries |
| Privacy | Strict — Based in Switzerland (outside the 5/9/14 Eyes) with an audited no-logs policy |
| Native Apps For: | Most main devices — Android, iPhone, Windows, Mac, Linux, and select routers (DD-WRT, AsusWRT, and Tomato) |
| Proven to Unblock: | Most major streaming platforms — Netflix, Disney+, HBO Max, and more |
| Torrenting | Supported — Every server supports torrenting |
| Customer Support | Fast response via live chat, email ticketing, and online form |
| Device Connections | 10 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ Live chat isn’t 24/7 ✘ Doesn’t work in China ✘ The money-back-guarantee doesn’t provide a full refund |
| Best Price | $4.49/mo (2-year + 6 months plan) |
Proton VPN ensures your online activity is anonymous with its optimized server connections and infrastructure. Unique to Proton VPN is the option to connect to the Tor network without downloading the browser. You get the anonymity of Tor plus the encryption of a VPN. I found using Proton VPN with Tor didn’t slow my speeds as much as using Tor by itself.
Alongside Tor, Proton VPN offers Secure Core servers that act like a multi-hop feature. This route your connection through 2 servers, with the first in a privacy-friendly country, ensuring your data is private even if a subsequent server is compromised. While this slowed my speeds significantly (by almost 95%), these servers are ideal if you highly value privacy.
When using its regular servers, Proton VPN provides speeds fast enough for lag-free activity. My speeds didn’t drop by more than 40%, even when connected to distant servers, so I could watch my favorite shows without issue. Proton VPN is supported by a 10Gbps server network to keep speeds as fast as possible.
Proton VPN accessed the following streaming services:
| Netflix | Disney+ | Hulu | Amazon Prime Video |
| BBC iPlayer | ESPN | HBO Max | …and more! |
Proton VPN also supports P2P file-sharing on multiple optimized servers, which I tested by downloading a 2GB file; the download finished in just under 5 minutes. However, Proton VPN doesn’t offer port forwarding, so you may find uploading is a slower process.
To keep you secure, Proton VPN has:
- AES-256-bit encryption — every connection features military-grade encryption for top-tier data security.
- Kill switch — keeps your online activity anonymous at all times, even if the VPN connection is interrupted.
- Strict no-logs policy — independently audited to prove Proton VPN never logs your data.
- Headquarters in Switzerland — outside of Eyes Alliance countries, with strong data privacy laws.
Unfortunately, Proton VPN doesn’t offer 24/7 live chat, which is frustrating if you have an urgent query. However, 24/7 email ticketing is available and responses are faster than I expected. I had replies to my emails within 24 hours.
If you’d like to test Proton VPN, subscriptions start at $4.49/month for a 2-year + 6 months plan. Proton VPN also has a free plan — it’s very limited, but a good way to try the service. Despite having a 30-day money-back guarantee, you won’t necessarily get a full refund. Rather, you’ll get a refund for the remaining time on your subscription.
Check out the in-depth Proton VPN review for further details on its servers, speeds, security, and more.
10. VyprVPN — Verified No-Logs VPN With Strong Commitment to Privacy
Quick Look: VyprVPN Results
| Speed | Average — Slow speeds when connected to servers far away |
| Security | Advanced — AES-256-bit encryption, kill switch, leak protection, and auditing |
| Servers | Small — A network of 700+ servers in 63 countries |
| Privacy | Strict — Based in Switzerland (outside of 5/9/14 Eyes) with an audited no-logs policy |
| Native Apps For: | All major devices — Android, iPhone, Windows, Mac, Blackphone, Amazon Fire Stick, Amazon Fire TV, Android TV, Blackberry 10, QNAP, OpenWRT, and Boxee Box |
| Proven to Unblock: | Most major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, BBC iPlayer, Sling TV, Vudu, and more |
| Torrenting | Supported — Torrenting is supported on all servers |
| Customer Support | Quick response 24/7 via live chat and email |
| Device Connections | 10 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ No native Linux app ✘ Doesn’t accept cryptocurrency payments ✘ No kill switch on iOS, router, Amazon Fire Stick, Amazon Fire TV, and smart TV apps |
| Best Price | $3.00/mo (2-year plan) |
VyprVPN will keep your personal data private and secure when you connect to its servers. It offers the following features that make VyprVPN a safe option for browsing, torrenting (P2P activity is supported on every server), and unblocking streaming sites from abroad:
- Military-grade encryption — keeps data hidden and anonymous on every connection.
- Data leak protection — stops IP, DNS, and WebRTC data from accidentally leaking and exposing your information.
- Kill switch — automatically blocks internet access if the VPN connection is interrupted (not available on iOS)
- Independently verified no-logs policy — proves VyprVPN does not log VPN activity or collect your data without your consent.
Impressively, VyprVPN is one of the few VPNs that responded to the Center for Democracy and Technology’s survey on VPN business models and privacy practices. Leviathan Security performed an independent audit and confirmed that VyprVPN doesn’t track any identifying data. I appreciate this high level of transparency with the public.
The most unique feature is VyprVPN’s proprietary Chameleon protocol, designed to bypass censorship using obfuscation. This makes your VPN traffic look like regular traffic, letting you perform tasks your ISP might otherwise restrict. You can also choose from other protocols, including PPTP, L2TP/IPsec, IKEv2, OpenVPN, and WireGuard.
When connected using the Chameleon protocol, I could stream Stranger Things in UHD quality with less than 5 seconds of loading time.
During tests, VyprVPN could also connect to these streaming services:
| Netflix | Disney+ | Amazon Prime Video |
| Hulu | HBO Max | …and more! |
When I ran speed tests using Ookla, I found my speeds dropped on distant servers in the US. The UK server slowed my network by 20%, but my speeds dropped 76% on US servers. While this wasn’t an issue for me because my broadband speeds are fast, VyprVPN might not be the best choice if you have slower internet.
Although I find ExpressVPN is a better all-around option, VyprVPN keeps you safe online for a much lower price of $3.00 a month. You can even make use of the 30-day money-back guarantee, which lets you try VyprVPN completely without risk. I had my money back in just 3 days after requesting a refund using the 24/7 live chat.
To learn more about VyprVPN, read the full review for comprehensive testing results on speed, servers, user experience, and more.
11. Ivacy VPN — Strong Security but Inconsistent Speeds and Streaming Access
Quick Look: Ivacy Results
| Speed | Inconsistent — Fast locally but slower on distant connections, with slow upload speeds |
| Security | Advanced — AES-256-bit encryption, kill switch, and leak protection |
| Servers | Moderate — A network of 5,700+ servers in 56 countries |
| Privacy | Strict — Based in Singapore (outside the 5/9/14 Eyes) with a no-logs policy |
| Native Apps For: | All main devices — Android, iPhone, Windows, Mac, Linux, and routers |
| Proven to Unblock: | Most major streaming platforms — Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, and more |
| Torrenting | Supported — Torrenting is supported on all servers |
| Customer Support | Quick response 24/7 via live chat and email |
| Device Connections | 10 |
| Money-Back Guarantee | 30 days |
| Minor Cons | ✘ No kill switch for iOS or Mac ✘ No independent privacy audit ✘ Singapore potentially co-operates with Eyes Alliance agencies |
| Best Price | $1.17/mo (5-year plan) |
Ivacy VPN offers top-tier security that effectively protects your data. As standard, every server features:
- AES-256-bit encryption — protects all data within a secure tunnel, ensuring your activity is anonymous.
- Full leak protection — keeps your personal data secure by blocking DNS and IP leaks.
- A kill switch — cuts access to the internet if Ivacy VPN is interrupted (not available on Mac or iOS).
- A zero-log policy — states that Ivacy VPN doesn’t monitor your connection or track your activity, but is not independently audited.
Ivacy VPN also has a useful split tunneling feature that I configured with my browser. I could bank online securely with the VPN while streaming on my local Netflix account.
I was impressed by Ivacy VPN’s Secure Download feature, which blocks downloads containing malware and other threats. I tried downloading malicious test files, and Ivacy VPN blocked them all. Secure Download was particularly useful while torrenting, and Ivacy VPN supports torrenting on every server.
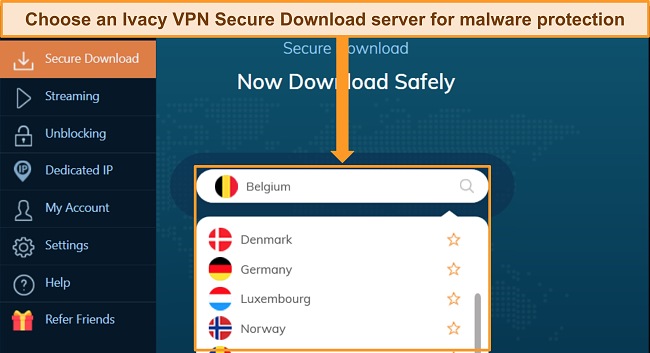
You can choose between multiple protocols, including WireGuard, OpenVPN, L2TP/IPSec, and IKEv2. I used the WireGuard protocol as this gave me reliable connections and fast speeds.
When testing speeds, I had reasonably fast download speeds, but uploads were often very slow. This made it difficult to share P2P files, have video calls, and play games online without lag.
I also had issues connecting to streaming services. It took multiple tries to access streaming accounts, even when using optimized servers. However, when I did make a connection, I could stream with minimal buffering and in UHD quality. Ivacy VPN works with:
| Netflix | Disney+ | Amazon Prime Video |
| Hulu | HBO Max | …and more! |
Ivacy VPN has broad platform compatibility, so you can download it to the most popular devices. However, Ivacy VPN is missing key features from its iOS and Mac apps, like split tunneling and a kill switch.
If you’d like to test Ivacy VPN for yourself, plans start at $1.17/month for a 5-year plan. You can test the service risk-free as Ivacy VPN has a 30-day money-back guarantee. However, you can’t claim a refund if you pay with cryptocurrency.
You can read the full Ivacy VPN review here to learn about its servers, speeds, customer service, and more.
Comparison Table: 2024’s Best VPNs
| ExpressVPN | CyberGhost | PIA | NordVPN | Surfshark | |
| Speed | Excellent | Good | Good | Good | Good |
| Security & Privacy | Excellent | Excellent | Excellent | Good | Good |
| Best Price (Monthly) |
$6.67 | $2.03 | $2.03 | $3.09 | $2.29 |
| Servers | 3,000+ servers in 105 countries | 11,800+ servers in 100 countries | 35,000+ servers in 91 countries | 6,300+ servers in 110 countries | 3,200+ servers in 100 countries |
| Supports Torrenting | ✔ | ✔ | ✔ | ✔ | ✔ |
| Split Tunneling | ✔ | ✔ | ✔ | ✔ | ✔ |
Why You Need a VPN
It’s more important than ever to protect yourself online, as new threats are emerging every day. When you connect to the internet without a VPN, you put your personal data at risk from hackers, advertising trackers, and even your ISP spying on your activity.
With a VPN, you can mitigate risks to your data security by encrypting your connection and masking your IP address. This ensures no one can see your online activity or where your device is located, protecting your privacy.
A VPN connection will help you to:
- Secure your personal data — High-level encryption stops others from seeing your online activity, IP address, and other data that can be used to hack, exploit, or restrict your connection. This is especially important when using public WiFi, which is notoriously unsafe.
- Remain anonymous when online — A VPN masks your IP address, making it very difficult to trace your true location or identity. This helps prevent online attacks (like DDoS attacks) and avoid location-based content blocks.
- Access the internet freely — By connecting to servers in other locations, you can avoid content restrictions imposed by the government or specific services. You can access your online accounts from anywhere, which is convenient when traveling.
- Torrent files without risk — P2P file-sharing puts your data at risk, as other users can see your IP address when you’re torrenting. Dedicated P2P servers secure your information and keep download speeds fast to complete your torrents quickly.
- Avoid ISP restrictions — Your ISP can throttle your connection for various reasons. A VPN hides your online activity, so your ISP can’t see what you’re doing, avoiding throttling in some instances.
The best defense against threats is using caution and connecting to a VPN as an extra layer of protection. Keep in mind that many VPNs won’t protect you from malware or intrusive ads, securely store your passwords, or make you completely anonymous. That’s why I always recommend the best VPNs to keep you as safe as possible.
How to Choose the Best VPN for You
Here are some points to consider when you’re choosing the best VPN for your needs:
- Comprehensive Security — your VPN should use AES-256-bit encryption and have comprehensive leak protection against WebRTC, IPv4, IPv6, and DNS leaks. Plus, your VPN needs a kill switch in case your connection is interrupted.
- Strict Privacy Policy — look for a VPN with a strict no-logs policy that won’t keep connection data. Ideally, the VPN should use RAM-based server technology and have been independently audited.
- Global Server Network — a higher number of available servers means less user congestion, faster speeds, and quicker connection times. Plus, a global network ensures you’ll have nearby servers to connect to, no matter where you’re located.
- Fast Connection Speeds — your VPN needs to mitigate speed loss to ensure you won’t experience lags or buffering when browsing, streaming, torrenting, gaming, online banking, and more.
- Optimized Servers — if you want a VPN for streaming, torrenting, or gaming, you can opt for a service with dedicated servers for these activities. Some VPNs offer obfuscated servers that hide your VPN traffic to avoid proxy detection.
- Device Compatibility — choose a VPN that offers native app support for your devices. Most VPNs have apps for popular platforms like Windows, Mac, iOS, and Android, and are compatible with smart TVs, game consoles, routers, and more.
- Top-Tier Customer Service — your VPN should have 24/7 customer support for urgent questions or issues and, at minimum, provide email ticketing (with prompt responses), in-depth FAQs, troubleshooting, and setup guides on its help site.
- Money-Back Guarantee — most premium VPNs have a money-back guarantee period that lets you test the service risk-free. You can make sure you pick the right VPN for your needs, and if you change your mind, you can easily get a full refund.
How to use a VPN?
Using a VPN is easy, and you can get started in just 3 simple steps. I tested the recommended VPNs to ensure they are all easy to set up so you can get connected and secure quickly.
After you’ve chosen the VPN you want, it’s as easy as signing up for a plan and downloading the software to your device.
- Get a VPN. For its excellent speeds and advanced security measures, ExpressVPN is the overall #1 VPN in 2024.
- Connect to a server. For the best speeds, choose a server location close to you.
- Start browsing the internet! Now you’ve got complete privacy and anonymity online.
How I Tested and Ranked 2024’s Best VPNs
1. Security and Privacy Features
Every VPN on this list has to pass a number of tests even to be considered for selection. These include DNS, IP (IPv4 and IPv6), and WebRTC leak tests, which my team and I carry out on ipleak.net.
The best VPNs should offer the following:
- Military-grade encryption — secures your internet traffic when browsing, banking, shopping, streaming, torrenting, and more.
- Secure protocols — including OpenVPN, WireGuard, and IKEv2.
- Additional security features — like a kill switch, split tunneling, server obfuscation, and compatibility with Tor.
- The ability to tunnel through tough internet restrictions — such as government firewalls in countries like China and Turkey.
- A strict no-logs policy — ideally independently verified by a third-party audit.
- Company headquarters in a country with strong data privacy regulations — especially outside of Eyes Alliance jurisdiction.
- A proven track record of reliability — showing the VPN is trustworthy and well-established.
2. Network of Global Servers
When a VPN has a large number of servers across the globe, the result is less congestion and overcrowding. You can connect to a server quickly and enjoy fast speeds without competing with hundreds of other users.
I recommend choosing a VPN with at least 1,000 global servers, although PrivateVPN would be one exception to this rule. I was initially skeptical of its low server number, but its performance over years of testing has made up for it.
I also make sure servers are distributed evenly worldwide to ensure local connections. A shorter physical distance between your device and the VPN server ensures a fast connection speed — especially important if you enjoy data-intensive internet activities, like HD streaming, online gaming, and torrenting.
At the same time, it’s important that VPN providers recognize which regions will be particularly popular and add more servers there to meet the demand.
Another feature I look for is server obfuscation. This masks your VPN traffic, making it look like regular traffic, which helps you avoid detection by VPN blockers. Some VPNs have obfuscation on all servers automatically, while others have an obfuscation feature that can be toggled on and off depending on your needs.
3. High-Speed, Low-Latency Servers
The best VPNs provide reliably fast connection speeds across the entire network, with low latency (or ping) for quick server responses. For each VPN, multiple speed tests are performed on various servers using Ookla. I then determine the average speed based on the results and look at the difference the VPN connection makes in comparison to base speeds.
Ideally, your VPN should minimize the speed loss that occurs on an encrypted connection. Local server connections should be very close to your base internet speed (no more than a 20% slowdown), while distant servers should have a 50% loss at most. A ping rate (latency) of less than 100ms is perfect — higher than 100ms may cause noticeable lag.
4. Unblocks Streaming Services Like Netflix, Disney+, and More
I check that each VPN can access US Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, HBO Max, ESPN+, DAZN, and more. Once connected, I make sure that buffering times are acceptable and stream quality remains at a high resolution.
I test global servers to ensure I can access content when I’m traveling in locations like the US, UK, Germany, Japan, Australia, and the Netherlands.
I also look for compatibility with streaming devices like smart TVs, tablet devices, smartphones, and desktop computers. This ensures you can stream your favorite content at home and on the go.
Important Note: Due to copyright laws and regulations, many streaming services prohibit the use of VPNs or proxies to access content that isn’t available in your location. Make sure you’re aware of the Terms of Service before using a VPN, as breaking your agreement could result in an account ban.
5. Supports Torrenting and P2P File-Sharing
Every VPN on this list allows torrenting and offers unlimited bandwidth, so you can upload and download as many files as you like. Torrenting without the protection of a VPN can leave you vulnerable to DDoS attacks, hackers, and malware.
With top-tier encryption and privacy, these VPNs will secure your data when P2P file-sharing. Some VPNs even have customizable settings that ensure you connect to a secure server before torrenting as an extra layer of protection.
I also look for torrenting-friendly features, including optimized servers for P2P activity, SOCKS5 proxies for faster downloading speeds, and malware protection. Plus, it’s a bonus if the VPN supports port forwarding as this allows faster downloads with greater security.
6. Works on all Major Devices and Operating Systems
If you’re like me, you connect to the internet on several devices at the same time. All VPNs on this list are compatible with multiple devices and operating systems. These include popular platforms like Android, iOS, Windows, Mac, iPad, and Linux, as well as the ability to configure a VPN with a smart TV, Amazon Fire devices, game consoles, routers, and more.
During tests, I checked the overall impact of the VPN on my devices, making sure they didn’t significantly drain my battery life or slow my system during connection. I tested the VPN protocols on different devices to ensure reliability when connected, which is especially important for mobile devices that often switch networks.
I also look for easy-to-use VPN apps. An intuitive interface, fast download time, and speedy setup mean you can connect quickly. A VPN should be simple for beginners and customizable for advanced users. It’s even better if the VPN offers the same features across all its apps. As a bonus, the top VPNs have detailed setup guides on their support websites.
7. Payment Options and Customer Support Availability
The best VPNs offer multiple secure payment options for convenience when setting up your subscription. Most will have typical methods like PayPal and debit or credit cards, while some also provide anonymous payments through cryptocurrency.
Pricing should be competitive, so I ranked each VPN based on the price compared to what it offers. Some services are more expensive but offer more security and privacy features — these often have discounts and coupon codes for a better deal. Budget VPNs usually have fewer servers and features, but maintain top encryption and no-logs policies.
A VPN must-have top-tier customer support, ideally with 24/7 live chat to answer any urgent questions or issues. Other key customer service includes email ticketing for less urgent queries (but still with prompt responses), in-depth FAQs, setup guides, and troubleshooting on the VPN’s support site.
FAQs on VPNs
What’s the best VPN for streaming Netflix?
I tested every VPN on this list with Netflix, and they can all connect to the service. However, the best choice for Netflix overall is ExpressVPN. With obfuscated servers, ExpressVPN can connect to more than 10 Netflix libraries worldwide by avoiding Netflix’s proxy detection. If Netflix can see you’re using a VPN, you can only watch Original content.
Plus, ExpressVPN’s fast speeds and reliable connections ensure you can stream your favorite content in UHD, even when you’re traveling to distant countries.
Are VPNs safe for torrenting?
Yes, VPNs are safe and recommended for torrenting. You should always connect to a high-quality VPN service to protect your data and activity before you start torrenting.
Without a VPN, your IP address and torrent activity are exposed to unwanted third parties while file-sharing. This can expose you to potential DDoS attacks or legal issues if you accidentally download copyrighted content. Your ISP can even throttle your connection if you download many large files in a short time.
By using a VPN, you hide your IP address and encrypt your internet traffic, so you can torrent as much as you want. I never start torrenting without first launching a VPN. My top choice is ExpressVPN as every server supports secure P2P file-sharing. CyberGhost is also a good option, with optimized P2P servers for dedicated torrenting activity.
Note that torrent websites are often loaded with malware. It’s crucial to block these threats before they can get near your device. Fortunately, several VPNs on this list are equipped with both ad and malware blockers for well-rounded protection.
What’s the best VPN for gaming?
ExpressVPN is the best VPN for gaming. During tests, I could play fast-paced games like Call of Duty: Warzone without lag or interruptions, and with ping as low as 12ms. This is the time it takes for your control input to be sent to the game server and back to you — the lower the number, the better, but anything below 100ms is perfectly adequate for online gaming.
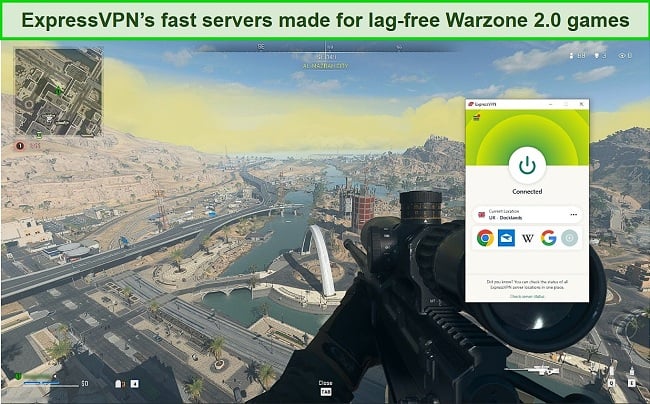
It’s important to remember that using a VPN to gain an in-game advantage or access region-restricted content could go against the game’s Terms and Conditions. Make sure you’re aware of the regulations before using a VPN, as you could face suspension or even a ban.
What is the best VPN for privacy?
All of the top VPNs in 2024 have high-quality privacy features, so you can rest assured your online activity and data is secure and anonymous. However, ExpressVPN’s privacy policy and company jurisdiction make it the top choice for privacy-focused VPN users.
ExpressVPN was one of the first VPNs to undergo an independent audit, proving its no-logs policy and demonstrating confidence in its server infrastructure. In recent years, other top VPNs have been independently audited, including CyberGhost, PIA, NordVPN, Surfshark, and more.
Crucially, ExpressVPN passed a real-world test when servers were seized by Turkish authorities as part of a criminal investigation into a user. The authorities were unable to obtain any data as ExpressVPN’s servers are physically unable to store user information.
What’s the fastest VPN?
On a server much closer to me, I reached just over 320Mbps (just 17% under my speed when disconnected from the VPN). These speeds are more than fast enough for streaming in UHD while browsing, downloading, and even gaming without interruption.
What’s the best VPN for China?
Based on real-life tests conducted in China, the top VPN is ExpressVPN. It’s one of the few VPNs that can reliably overcome the Great Firewall of China and access restricted sites like Facebook, Google, Gmail, YouTube, Wikipedia, and more.
ExpressVPN uses server obfuscation to avoid China’s proxy detection, letting you connect to your local accounts when you’re in the country. Plus, ExpressVPN’s superfast speeds ensure you can browse, stream, shop, and more without lag or buffering. Just make sure you download your VPN before arriving in China, as most VPN websites are blocked there.
Important! You should exercise basic caution while using a VPN in China — it doesn’t give you a license to commit illegal acts. Also, while non-government-approved VPNs are illegal in China, there haven’t been any public cases of tourists being penalized for their use by the government.
What’s the best VPN with dedicated IPs?
CyberGhost is the best VPN with a dedicated IP. This paid add-on can reduce the side effects of using shared IP addresses on a VPN and let you access your accounts without having to worry about 2FA or CAPTCHAs.
An important issue CyberGhost resolves are the “bad neighbor effect.” Other users with the same IP may abuse services like search engines, financial institutions, or streaming sites. When you use the same IP address with these services, you find you’re blocked or can’t pass the CAPTCHA verification. With your own dedicated IP, this stops being an issue.
CyberGhost also skillfully avoids linking you to your static IP by letting you buy an anonymous token you can redeem in your account. This way, you can even buy and gift a static IP to family or friends. The downside is that if you lose the token, you’ll lose access to the IP.
What’s the best VPN with port forwarding?
The best VPN for port forwarding is Private Internet Access. You can easily turn on the feature in its settings, and when you connect to a server you’ll be shown a randomly selected port that you can use.
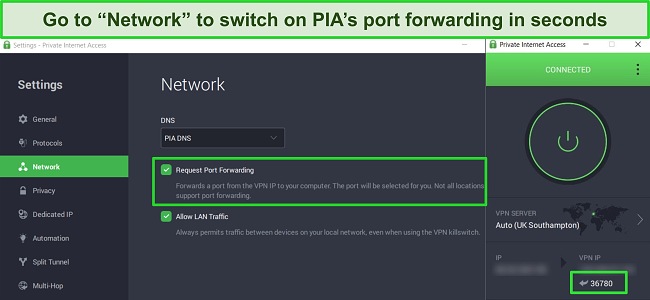
Port forwarding essentially opens up a port through the NAT firewall on your local network to speed up and allow more direct network connections. Normally, the NAT firewall hides the IP addresses of the devices connected to your router. However, this can lead to issues like specific servers being unable to connect to your device or slower speeds.
Note: Port forwarding can expose your local network to threats, as data transmitted via the forwarded port won’t be protected by the VPN.
Will a VPN stop ISP throttling?
A top-tier VPN service can help stop ISP throttling, but it depends on why your connection is being throttled. ISP throttling often happens when your ISP detects high bandwidth use and wants to regulate traffic for the entire network. In this case, a VPN can help as it routes your traffic through less crowded servers to reach your destination.
Your ISP may use techniques like “peering” to spy on your activity — some ISPs have been known to automatically throttle speeds when streaming video is detected. By connecting through a VPN server, your ISP can’t detect your website visits, P2P file-sharing, or any other activity, which can help you avoid throttling.
However, if your speeds are throttled because you’ve hit your data cap, a VPN can’t help. Despite a VPN encrypting your connection and hiding your activity, your ISP can still see how much data you’re using and can slow your connection when you’ve passed certain thresholds.
What is the best VPN for Android and iOS?
For high-quality security and privacy on your Android and iOS devices, I recommend ExpressVPN. The VPN has native app support for Android and iOS, blazing-fast connection speeds, and an intuitive interface that makes it simple to navigate for beginner and advanced VPN users.
Whether you’re using ExpressVPN on Android or iOS, you’ll have full access to its 3,000+ servers in 105 countries. Plus, you can choose between connection protocols (including ExpressVPN’s proprietary Lightway protocol) and protect your data with a built-in kill switch.
As a bonus, ExpressVPN is a lightweight app that won’t drain your battery or excessively use data — making it ideal for keeping your data and activity secure when you’re on the go with your mobile devices.
How do VPNs work?
A quality VPN hides your real IP address and encrypts your activity by routing your traffic through a server controlled by the VPN provider. When you connect to a VPN server, the traffic routed between your device and your online destination is securely encrypted — no one can see what you’re doing.
By using a VPN, your online activity cannot be traced back to you, and you can get around censorship, firewalls, and location-specific restrictions. A VPN can make your device appear to be in a different location by masking your true IP address and replacing it with one from its server.
For example, if I have a Netflix subscription but travel overseas, I lose access to the content library that I’ve paid for. By connecting to a VPN server in my home country, I can continue watching my original content library without issue. You can check that your VPN is properly masking your IP address by using an IP address checker tool.
At the same time, VPN encryption hides your activity from anyone who might be watching (such as advertisers and hackers). You can browse the internet, access your bank account, download torrents, and more without being spied on by third parties. This boosts your online safety, reducing the risk of malware, trackers, and identity theft.
Can I get a good cheap VPN?
You don’t have to pay premium prices to get a high-performance VPN. While costs can vary between VPN providers, you’ll always get the best prices if you choose a long-term subscription. It often works out at just a few dollars every month, and most often you can find VPN coupons and hidden deals for extra savings.
All of the top VPNs are backed by a money-back guarantee, so you can make your purchase with confidence. If you find your VPN isn’t right for you, you can get a full refund.
Will a VPN slow down my device?
The top VPNs in 2024 won’t slow down a modern device too much, but will likely impact your internet speeds. This happens because VPNs encrypt and reroute your traffic through their servers in a different location, so the data takes longer to reach its destination.
To ensure you don’t experience a significant slowdown, it’s important to use a VPN that can easily mitigate speed loss caused by encryption. Look for fast connection protocols, like WireGuard, ExpressVPN’s Lightway, or NordVPN’s NordLynx. A large server network also helps keep speeds fast by reducing user congestion, especially at peak traffic times.
If you have more than 1 device connected to the VPN, this can also cause your speed to drop, but this reduction tends to be minimal. With the top VPNs, even when I connected 4 devices (my Windows laptop, iPhone, Fire Stick, and iPad) the decrease in speed was barely noticeable.
Are VPNs legal?
It’s completely legal to use a quality VPN to protect your privacy in most parts of the world, including the US, UK, most of Europe, Australia, New Zealand, and Canada.
However, countries with internet surveillance or censorship heavily regulate or ban VPNs. VPNs are regulated in countries like China, the UAE, Turkey, Belarus, Iran, Russia, and Uganda, and banned in locations like Belarus, North Korea, Oman, Turkmenistan, and Iraq.
For example, in China, it’s only legal to use government-approved VPN services. These VPNs log your data and activities and share those details with the government. Another example is the UAE, where you can’t use a VPN to access content in other countries. If caught, you could face a fine or even prison time.
To be safe, you should check the local laws regarding VPNs and only use a VPN for legal activities.
How can I get a VPN with no logs?
All of the top VPNs on this list have a strict no-logs policy, meaning none of your online activity is ever stored by the service. Ideally, the VPN you choose will use RAM-based servers that cannot physically store logs, or it will have voluntarily undertaken a third-party audit to verify that it doesn’t keep any user data.
With a verified no-log VPN, none of your connection times, session information, bandwidth usage, browsing history, IP addresses, or other personal data is stored. Plus, some of the top VPNs accept cryptocurrency as a payment option — if you create an account with a dummy email address, you can ensure total anonymity.
Can I use a proxy or Tor instead of a VPN?
You can, but you won’t get the same high level of security or anonymity as you do with one of the best VPNs on the market. Both Tor and proxies send your internet traffic through a “middleman” server or node. While this hides your original IP address, neither Tor nor proxy servers encrypt your internet traffic, leaving your data vulnerable.
Proxies have one advantage over a VPN — superfast connection speeds. However, with no encryption or other security features, you can’t trust a proxy to keep your data private or your activity anonymous. Some proxies even keep logs of your online browsing activity.
Tor is much more secure than a proxy as it passes your traffic through multiple nodes, reducing the chance anything is traced back to you. However, this long journey means Tor is incredibly slow, sometimes so slow that the connection simply fails.
If you value your online privacy, I strongly suggest you use a top-grade VPN or combine Tor with a VPN. With a VPN, your IP address remains hidden, and all your internet traffic is encrypted.
What’s the best free VPN?
The best free VPNs are “freemium” services like Proton VPN, but you’ll still face serious limitations. Rather than deal with slow speeds, server restrictions, and bans on streaming, I suggest investing in a premium VPN with fast server speeds and 1000s of servers that work with dozens of international streaming platforms, including Netflix.
While there are some safe free VPNs, most free providers are known to sell your private data and browsing history to earn revenue. Worse still, many untrustworthy free VPNs often contain malware that infects your device to steal sensitive information, such as passwords, banking history, and private photos.
If you only need a VPN for a short time, the best free VPN is actually a premium VPN with a money-back guarantee. For instance, you can use CyberGhost risk-free for 45 days with its money-back guarantee. As soon as you’re finished with the service, you can easily get a refund by speaking to the customer support team.
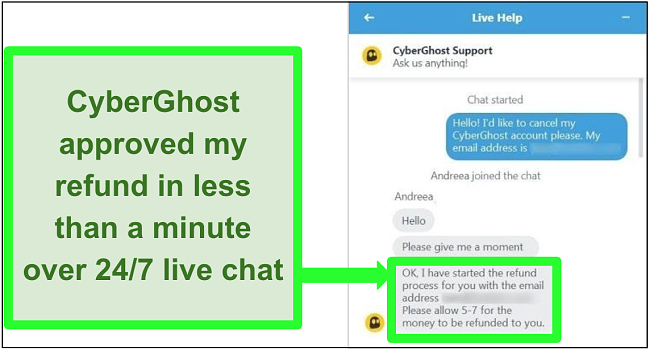
Getting my money back was simple — I just spoke to customer service over 24/7 live chat, and my refund was processed immediately. Best of all, I got my money back in 5 business days.
Protect Your Device With the Best VPN in 2024
To save you time and frustration, my team and I have rigorously tested more than 150 services to find the top VPNs in 2024. All of the above VPNs have strong security and privacy, solid server networks, and good speeds for browsing, streaming, gaming, and more.
Overall, ExpressVPN is the #1 VPN due to its proven ability to secure your online traffic, bypass geo-blocks, and function in even highly-censored countries like China. It does all this while offering some of the fastest speeds I’ve seen a VPN achieve, on top of an audited server infrastructure that maintains user privacy.
But you don’t have to take my word for it — you can try ExpressVPN risk-free as it’s backed by a 30-day money-back guarantee. I think you’ll be happy with the service, but if you’re not satisfied for any reason, you can get a full refund, no questions asked.