7 Best Linux VPNs in 2024 and Which to Avoid
Practically every major VPN has a Windows and macOS release, but Linux is often treated as an afterthought by developers and I had trouble finding VPNs with compatible apps. To remedy this, I’ve personally tested over 15 of the best VPNs to find native CLI or GUI-based clients that won’t require you to configure your Linux VPN settings manually.
For the fastest speeds, most secure servers, easy setup, and superb usability, ExpressVPN is my top VPN for Linux. It supports a wide variety of Linux distros and has secure, superfast servers that can access multiple streaming services. Plus, You can test ExpressVPN out with Linux completely risk-free as it’s backed by a 30-day money-back guarantee — if you don’t like it, you can easily get a full refund.
Editors’ Note: Intego, Private Internet Access, CyberGhost and Expressvpn are owned by Kape Technologies, our parent company.
Quick Guide: The Best VPNs for Linux in 2024
- ExpressVPN — #1 VPN for Linux with high speeds and access to numerous streaming services, plus a GUI-based VPN browser plugin for Chrome and Firefox.
- CyberGhost — Gives you easy access to multiple global streaming libraries with its dedicated streaming service, but doesn’t work in Turkey or China.
- PIA — The only VPN on the list to offer a graphical user interface on Linux, but is based in the US so data surveillance may be a concern.’
- NordVPN — Support for most Debian and RHEL-based systems, but it lacks a visual GUI.
- Surfshark — Works with Debian, Ubuntu, and Mint with a complete GUI, but it has a more limited server network than other options on this list.
- PrivateVPN — Remote setup service for Linux where a customer support agent guides you through installation, but has the smallest server network on this list.
- IPVanish — You can install it on unlimited Linux-based devices, but it isn’t as fast as ExpressVPN or CyberGhost.
Best VPNs for Linux — Tested 2024
1. ExpressVPN — The Fastest, Most Secure Servers With a Browser-Based Linux GUI
Key Features:
- Over 3,000 secure and superfast servers in 105 countries
- Connect safely and privately on Linux with 256-bit military-grade encryption, a kill switch, and a no-logs policy
- Protect up to 8 Linux devices at once
- Subscribe with credit cards, PayPal, or anonymously with Bitcoin
- 24/7 live support chat, online tickets, and an extensive knowledge base
- 30-day money-back guarantee on all plans
ExpressVPN is my top VPN for Linux because it has superfast servers on an intuitive GUI in its Chrome and Firefox extensions. After connecting via the Linux Chrome extension, I tested speeds on servers around the world. ExpressVPN was faster than any other VPN I tried with Linux. With consistent speeds of between 90-100 Mbps or higher, all my online activities like streaming and torrenting were nearly as fast as when I wasn’t using a VPN.
Your online activities on Linux can never be revealed since ExpressVPN’s TrustedServer network runs on RAM rather than a regular hard drive. This ensures it keeps no logs, and all data is completely erased each time servers are rebooted. An independent audit by PWC confirmed ExpressVPN’s TrustedServer technology and no-logs policy were effective. This was also evidenced in 2017 when Turkish authorities seized an ExpressVPN server but couldn’t find anything on it.
The Linux version of ExpressVPN includes the best available security features. To make sure it really hid my data on Linux, I ran numerous tests and found the following on all servers:
- 256-bit military-grade encryption to keep your data protected from hackers
- DNS and IP leak protection so your real identity is never revealed
- A proprietary protocol called Lightway, which has powerful security without compromising on speed.
Better yet, you can use a graphical interface for ExpressVPN on Linux devices by installing the browser extension for Chrome or Firefox. It’s easy to add each browser in just a few seconds. If you want a VPN for non-browser use, you can operate ExpressVPN on Linux through the command line. To quickly call up all of the possible commands, type “man expressvpn” into the terminal. This gives you an instant overview of all functions.
This VPN is also one of the best for streaming on Linux. It’s able to easily bypass tough geo-blocks on platforms including Netflix, Hulu, Disney+, and more. While testing, my team accessed The Mandalorian and Toy Story 4 from Disney+ US, which loaded almost instantly in full HD quality.
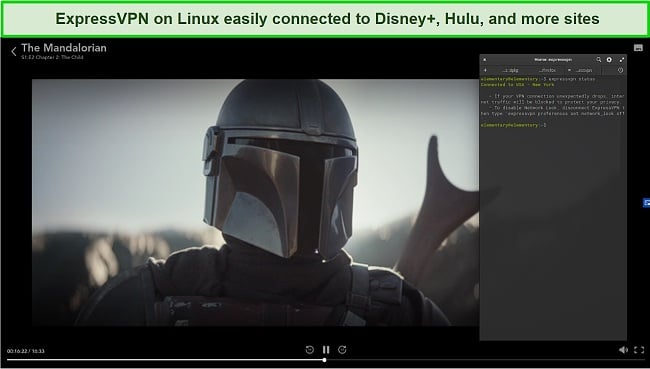
While ExpressVPN plans are a little costlier than the other VPNs on this list, the top-notch performance and features make it worth it. That’s especially true if you take advantage of the 49% discount for the 1-year + 3 months plan, which costs $6.67/month.
You can also try ExpressVPN for Linux with no risk for 30 days with its money-back guarantee. That gives you time to check out its browser extensions, speeds, and security features for yourself. I checked the policy by signing up and testing the service for a couple of weeks, then requested a refund through the 24/7 live chat. The agent immediately processed it and I had the money back in my account just 2 days later.
ExpressVPN unblocks: Netflix, Disney+, HBO Max, YouTube, Amazon Prime Video, BBC iPlayer, Vudu, SkyTV, Sky, Showtime, ESPN, and more
ExpressVPN works on: Ubuntu, Debian, CentOS, Fedora, Elementary OS, Raspbian (32-bit only), Arch, Windows, macOS, Android, iOS, Chromebook, PS4, Xbox, Nintendo Switch, Blackberry, and more
Editors' Note: ExpressVPN and this site are in the same ownership group.
2024 Update! ExpressVPN has dropped prices for a limited time to a crazy $6.67 per month for the 1-year plan + 3 months free (you can save up to 49%)! This is a limited offer so be sure to grab it now before it's gone. See more information on this offer here.
2. CyberGhost — Dedicated Streaming Servers for Quick Media Access
Key Features:
- More than 11,800 secure servers in over 100 countries, including optimized options for streaming on Linux
- Uses 256-bit military-grade encryption and an automatic kill switch on no-logs servers
- Allows up to 7 connections
- Sign up with credit cards, PayPal, Amazon Pay, or privately with Bitcoin
- 24/7 support chat, plus online guides
- 45-day money-back guarantee on the 2-year + 4 months plan
CyberGhost has a special menu of servers optimized for streaming on international TV and movie sites in HD or 4K quality. There are options for Netflix US, UK, Germany, and France, Hulu, BBC iPlayer, Disney+ US and France, and many more. During tests of CyberGhost’s network, my team and I found the connections were made quickly and remained steady for hours.
To easily connect to any of the available servers in Linux, you can type a simple terminal command such as “sudo cyberghostvpn –streaming –country-code”. This opens the list of streaming servers. Just add the service and country code to the command to connect. For example, if you wanted to use Hulu, you’d type: “sudo cyberghostvpn –streaming ‘Hulu’ –country-code US –connect”.
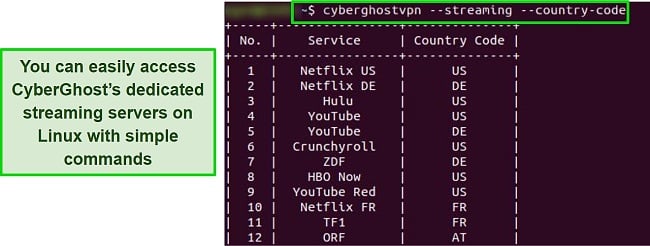
Then open Chrome, log into Hulu, and watch your favorite shows. Firefox is compatible as well, but it requires some extra configuration.
I found that CyberGhost’s security features are just as powerful as its streaming capabilities. You can access a selection of OpenVPN, Wireguard, PPTP, IPSec, and L2TP encryption protocols. Amongst its great features, you’ll find:
- AES-256 bit encryption to hide your data from third parties
- An integrated kill switch to cut your internet in the event the VPN falters, keeping your identity protected.
- No-leak servers as proved in my DNS, IPv6, and WebRTC tests, so your real IP is constantly masked.
My speeds were about 20-30% slower with CyberGhost than ExpressVPN. I had an average of just over 78Mbps on regular servers and around 70 Mbps on streaming servers. However, this is a minor issue since CyberGhost is fast enough for 4K streaming, video chat, gaming, and other bandwidth-intensive online activities.
CyberGhost’s long-term plans are great value, with a $2.03/month option if you get the 2-year + 4 months plan. That’s a 84% discount from its short-term plan option. But if you want to test it before making a decision, you can check out CyberGhost’s optimized streaming servers for free with its 45-day money-back guarantee. I tested the refund policy by contacting 24/7 support chat after a few weeks. The agent immediately processed my request, and I received my money just 3 days later.
CyberGhost unblocks: Netflix, Disney+, HBO Max, Amazon Prime Video, BBC iPlayer, Vudu, SkyTV, Showtime, ESPN, Spotify, and more
CyberGhost works on: Ubuntu, CentOS, Fedora, Linux Mint, Kali, Windows, macOS, Android, iOS, Chromebook, PS4, Xbox One, and Nintendo Switch
Editors' Note: CyberGhost VPN and this site are in the same ownership group.
2024 Update! You can subscribe to CyberGhost for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 84%)! This is a limited offer so grab it now before it's gone. See more information on this offer here.
3. Private Internet Access — Easy-to-Use Full Linux Graphical User Interface
Key Features:
- 35,000+ servers in over 91 countries, available via a graphical Linux interface
- Comes with 256-bit military-grade encryption, an internet kill switch, and no-logs policy
- Use on up to unlimited of your Linux-based devices
- Payment options include credit cards, Amazon Pay, PayPal, and top cryptocurrencies
- Fast support via 24/7 support chat, email, plus extensive online guides and FAQs
- Easy-to-redeem 30-day money-back guarantee
PIA was the only VPN I tested for Linux that had its own easy-to-use graphical user interface (GUI). This was much easier than learning and entering commands in the Terminal or taking the extra steps of installing a browser extension.
The user interface gives you the option to alter many of PIA’s security settings. You can switch between OpenVPN and WireGuard protocols, change encryption strength, and even adjust handshake settings (how the VPN and the server exchange secret keys to establish the connection). This is how PIA lets you find the perfect balance of speed and security.
An additional benefit of a GUI is that it protects your entire connection on all Linux apps and not just your web browser traffic, as is the case with extensions. You still might need to use the terminal to set up PIA initially, but then you’ll be able to use an intuitive VPN interface just like on PCs, Macs, and other desktop-based platforms.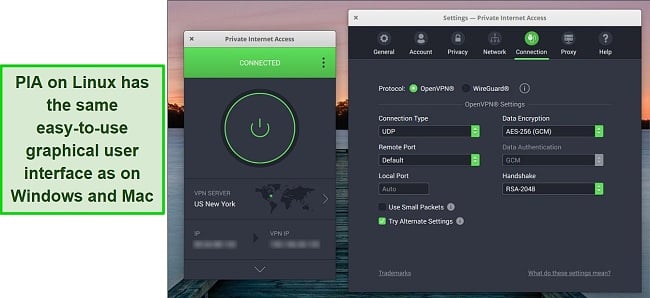
I found this useful when I needed strong encryption for safe torrenting but then wanted faster speeds for watching 4K YouTube. By lowering encryption, my data could travel faster and I could watch YouTube lag-free. With average speeds on PIA’s servers between 40-60Mbps, Ultra HD only resulted in 5-8 seconds of buffering, which was pretty impressive.
A downside is that PIA is based in the US — a member of the 5 Eyes intelligence-sharing agreement. However, PIA’s strict no-logs policy was proven when the Russian government seized its servers and couldn’t recover any user data. With no logs about my activities or identity, I’m not worried about PIA being located in the US.
I also love that PIA open-sourced its Linux apps. Tech experts can review the app’s code for vulnerabilities, and you can know exactly what code is being run on your Linux device. Plus, you don’t have to pay top price for top-notch security — PIA’s super-affordable plans go as low as $2.03 per month.
If you still aren’t sure, you can try out PIA’s graphical Linux interface for free for 30 days with its money-back guarantee. I tested it by contacting a customer support agent via 24/7 live chat, and I had my money back the next week.
PIA unblocks: Netflix, Amazon Prime Video, ESPN, Showtime, and more
PIA works on: Ubuntu, Debian, Linux Mint, Arch, Windows, Mac, Android, iOS, Chrome, Firefox, and Opera
Editors' Note: Private Internet Access and this site are in the same ownership group.
2024 Update! You can subscribe to PIA for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 83%)! This is a limited offer, so grab it now before it's gone! See more information on this offer here!
4. NordVPN — Premium VPN With Cheap Prices on Long-Term Plans
Key Features:
- Short and long-term subscriptions available
- 30-day money-back guarantee
- 6,300+ global servers in 110 countries
- Unlimited bandwidth
- Protect up to 10 devices at once
NordVPN is one of the best VPNs on the market — and you can get super cheap prices when you sign up for a long-term subscription. One thing to note, however, is that when it’s time to renew your subscription, prices do increase quite significantly.
I was particularly impressed with the high performance of every server I tested. Just because a VPN has thousands of servers doesn’t mean they all work. Servers can still struggle to work — and some can even fail to connect completely. However, NordVPN’s servers work with Netflix for smooth, buffer-free streaming.
I did, however, have issues with using NordVPN’s native Fire TV app. Although it mostly worked with Netflix, it sometimes had issues and kept crashing. I also found that NordVPN’s user interface for desktop devices was less user-friendly than ExpressVPN and CyberGhost.
NordVPN has the following security and privacy features:
- AES 256-bit encryption
- kill switch that cuts your internet access if your connection to a VPN server drops suddenly
- built-in ad and malware blocker, so you don’t need a third-party ad blocker
- fully audited no-logs policy (audited by PwC) – NordVPN doesn’t store any personal or identifying data while you’re connected to the VPN
In addition, NordVPN includes Threat Protection that protects you from viruses, infected websites, and trackers – and it works whenever you have the NordVPN app open, even if you’re not connected to a VPN server.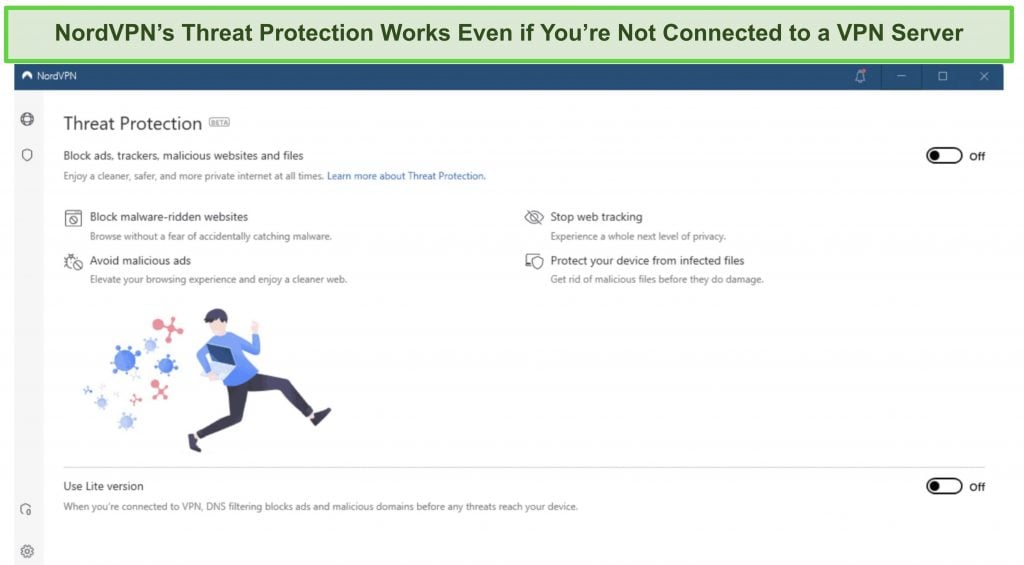
With plans that cost as little as $3.09 per month, it's easy to find a NordVPN subscription plan that suits your needs. You can also stream, torrent, and browse for free for up to 30 days with its money-back guarantee. I tested this to ensure that you’ll really get your money back. At first, the support team tried to give me an extended trial period — but they initiated my refund right away after I told them I wasn’t interested in the extension. I got my money back in 6 business days.
NordVPN works with: Netflix, Amazon Prime Video, BBC iPlayer, Hulu, Disney+, SkyTV, HBO Max, SHOWTIME, DAZN, ESPN, YouTube TV, and more
NordVPN works on: Windows, Mac OS, Android, iOS, Windows Phone, Chromebook, Linux, Chrome, Firefox, Fire Stick, and Android TV
5. Surfshark — Best Value for Money with Unlimited Device Connections and Fast Speeds
Key Features:
- Short and long-term plans available
- 30-day money-back guarantee
- 3,200+ global servers in 100 countries
- No bandwidth restrictions
- Connect unlimited devices at once
Surfshark offers the best value for money out of every premium VPN on the market. You can connect an unlimited number of devices with a single subscription, which means you can use Surfshark on all your devices without getting logged out.
I tested Surfshark’s simultaneous connections on 2 PCs, 2 phones, a Fire Stick 4K, and an iPad. My connection remained reliable on all 6 devices. Even while I was actively streaming on all my devices, my average speed was 112 Mbps — fast enough for UHD quality.
When I saw the price of this service, I thought it couldn’t possibly have top-grade security features for such a low price, but I was pleasantly surprised.
Surfshark has the following security and privacy features:
- AES 256-bit encryption on all devices, with ChaCha encryption available for Android users
- Wireguard VPN protocol enabled by default
- diskless, RAM-only servers to protect your privacy (no data can be physically extracted from any servers)
- kill switch (although this isn’t enabled by default)
- IP and DNS leak protection
Surfshark offers two-factor authentication (2FA) on your account. This feature requires you to enter an extra code before you can log in to ensure that only you can access your account.
While Surfshark does have slightly fewer global servers than rivals such as CyberGhost and PIA, I didn’t experience any issues during my tests. I easily connected fast working servers every time, and I had excellent speeds for streaming, downloading torrents, and browsing the internet.
You can try Surfshark for yourself with the 30-day money-back guarantee. It has plans that cost as little as $2.29. Requesting a refund is easy with Surfshark’s live chat feature. Although the support team asked why I wanted to cancel my subscription, I had no problem getting my money back (and it only took 4 days!).
Surfshark works with: Netflix, Amazon Prime Video, Disney+, BBC iPlayer, Sling TV, Hotstar, HBO Max, DAZN, and more
Surfshark works on: Windows, Mac OS, Android, iOS, Linux, Fire Stick, Samsung Smart TVs, LG Smart TVs, Android TV, Kodi, and selected routers
6. PrivateVPN — Stress-Free Remote Linux Setup With a Live Support Agent
Key Features:
- Over 200 servers in 63+ countries
- Protects Linux devices with 256-bit military-grade encryption, and zero data logs
- Cover up to 10 Linux devices
- Pay via credit cards, PayPay, or privately using Bitcoin
- 24/7 live chat, email support, and FAQs
- Flexible 30-day money-back guarantee policy
PrivateVPN’s remote setup gives you a live support agent to install and connect its Linux app for you. You just have to download some free third-party software that allows a PrivateVPN support technician to do all the work. You can then delete the free software when you’re done.
In my trial, I had a PrivateVPN technician swiftly handle the entire installation process within a few minutes. What’s more, the technician kindly offered a brief tutorial on using the software, including instructions for entering commands in the Linux terminal. This kind of support can prove extremely helpful, especially for individuals who are new to Linux, as it can seem a bit intimidating at first.
If you’d rather install it yourself, PrivateVPN’s online guides take you step-by-step. As an added bonus, PrivateVPN integrates with Linux’s built-in VPN configuration menus, so the VPN can be activated and used from outside the Terminal without a native GUI. This makes up for the main con of PrivateVPN for Linux, which is that it doesn’t have a browser extension for Chrome or Firefox.
For streaming, PrivateVPN works inconsistently. Sometimes it’s necessary to try a few different servers to find one that works. It eventually allowed logins to most of the major TV and movie sites including Netflix, Amazon Prime Video, Hulu, Disney+, HBO Max, and others. Thanks to its solid speeds consistently above 50Mbps, lag was never an issue even in 4K.

There are some very affordable PrivateVPN plans, like the 3-year subscription for $2.00 per month. If you’d rather test it before you commit, you can try PrivateVPN for Linux risk-free with a 30-day money-back guarantee. I tested it myself by asking for a refund via email. I had my money back the following week.
PrivateVPN unblocks: Netflix, Amazon Prime Video, Showtime, and more.
PrivateVPN works on: Ubuntu, Debian, Linux Mint, Arch, Windows, Mac, Android, and iOS.
2024 Update! PrivateVPN has dropped prices for a limited time to a crazy $2.00 per month with the 3-year plan (you can save up to 85%)! This is a limited offer so be sure to grab it now before it’s gone. See more information on this offer here.
7. IPVanish — Protect All Your Linux-Based Devices at Once
Key Features:
- More than 2,400 servers in 55+ countries
- Protects Linux devices with 256-bit military-grade encryption and a no-logs network
- Protect unlimited Linux devices
- Pay via credit cards, PayPal, or privately using Bitcoin
- 24/7 live chat, email support, and FAQs
- Full refunds within 30 days with its money-back guarantee
IPVanish is one of the few VPNs for Linux that lets you protect unlimited devices. Better yet, even while I was connected on more than 10 devices at once I still got solid speeds. Results between 66-85 Mbps were consistent across server locations on 1 device, and on 11 devices I only saw my speeds reduce 20%. That means while it was slower than other VPNs on this list, IPVanish was more than fast enough for HD streaming on multiple devices at once.
During tests of its unblocking capabilities, IPVanish could access Netflix easily in multiple countries. However, unlike ExpressVPN it couldn’t get into Amazon Prime Video, Disney+, HBO Max, Hulu, and other popular streaming sites. If streaming is one of your priorities, I’d recommend using ExpressVPN.
There’s no GUI for Linux, but you can install IPVanish’s Chrome browser extension to avoid having to use the Terminal commands. Just keep in mind that this won’t protect other apps you’re using on Linux, only your web browsing. If you decide to install the VPN natively, guides on IPVanish’s website walk you through the process for different distros.
Amongst other features, you’ll get the following security features when you sign up with IPVanish:
- Military-grade 256-bit encryption to stop hackers from reading your data
- No-logs servers to your browsing history and personal information isn’t stored
- Independent audits, so you can trust its no-log and security policies.
There are reasonably-priced IPVanish plans for only $2.99/month if you subscribe for a unlimited period. But you don’t have to decide immediately — it’s free to try IPVanish for Linux with its money-back guarantee. The policy gives you 30 days to test the VPN and make sure you like it. If you want a refund, you can get one approved instantly with an online ticket system. I got my money back less than a week after I sent my request.
IPVanish unblocks: Netflix, Amazon Prime Video, and more.
IPVanish works on: Ubuntu, Fedora, Linux Mint, Lubuntu, Windows, Mac, and Android.
Editors’ Note: Intego, Private Internet Access, CyberGhost and Expressvpn are owned by Kape Technologies, our parent company.
Why You Need a VPN for Linux
Linux may be safer than Windows, but it still leaves you exposed to many online dangers if you don’t take the right precautions. Here are just a few reasons why using a VPN on Linux is a good idea:
- Increase privacy — If you don’t have a VPN, your IP address allows continuous tracking of your online activities. However, by utilizing one of these Linux VPN providers, you can effectively safeguard your privacy and maintain anonymity while browsing the web.
- Strengthen security — You want all your data to be hidden when you go online, especially if you’re on a public network. Malicious users sharing your connection can intercept sensitive data or hack your device if you’re not using a quality VPN.
- Unblock content — To get access to global libraries from Netflix, HBO, Hulu, and more, it’s necessary to get a new IP address from a different country. A VPN does this in seconds, unblocking previously unwatchable content. It’s even possible to use a VPN in countries with online restrictions to bypass them and browse freely.
- Torrent safely — If you download torrents, having a VPN is essential. Hackers like using these networks to plant malware onto devices, and third parties watch all your file-sharing activities. With a VPN, you’re hidden from hackers and any prying eyes. Just keep in mind that you should never share illegal or copyrighted material on torrent networks just because you’re able to hide your activities.
Research Methodology: How to Get the Best VPN for Linux
To keep you safe online and give you the best VPN experience on Linux, you should look for:
- Proven Linux compatibility — A lot of VPNs say they support Linux, but hardly ever update their apps, or they can only be used through the Linux terminal. After testing the top VPNs in the market, I selected the best ones that have graphical browser extensions, a native GUI, or integrate with a Linux distro’s built-in VPN configuration menu.
- High-end security — All my recommended VPNs for Linux support several modern tunneling protocols (including OpenVPN) with AES-256 bit encryption. This is one of the strongest forms of encryption in the cybersecurity industry.
- Fast servers — High VPN speeds are essential so you can browse, stream, and share files without lag. I tested speeds on servers around the world to find the fastest Linux VPNs.
- Ability to unblock geo-blocked material — From streaming sites like Netflix to overcoming government restrictions such as those in China, a Linux VPN should have servers advanced enough to reliably access all of the information on the web. Just remember that the privacy of a VPN doesn’t give you a license to break the law.
- Safe torrenting — A quality VPN keeps you anonymous while torrenting so hackers can’t see your connection and prying eyes can’t track your download activity.
- Strict privacy policies — Ensure your Linux VPN has a robust no-logs policy and a proven track record for protecting user privacy. An independent audit is a bonus.
- 24/7 customer support — You can get quick answers to any question if your VPN has support agents available 24/7 via live chat. I also looked for the best monthly VPN plans and reliable money-back guarantees.
Comparison Table: 2024’s Best VPNs for Linux
| ExpressVPN | CyberGhost | PIA | NordVPN | Surfshark | PrivateVPN | IPVanish | |
| Compatible With Linux Distros | Ubuntu, Debian, Fedora, Mint, Arch, Raspberry Pi | Ubuntu, Fedora, Mint, CentOS, Pop!OS, Kali | Ubuntu, Mint, Debian, Fedora, Arch | Debian, RHEL, Ubuntu, Fedora, openSUSE, Mint, Elementary OS | Debian, Ubuntu, Mint | Ubuntu, Debian | Ubuntu, Fedora, Kali, Mint, Lubuntu, Pop!OS |
| GUI/ Browser Interface | ✓ | ✘ | ✓ | ✘ | ✓ | ✘ | ✓ |
| Unblocks Netflix | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Allows Torrenting | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Kill Switch | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Device Connections | 8 | 7 | unlimited | 10 | unlimited | 10 | unlimited |
| Money-Back Guarantee | 30 days | 45 days | 30 days | 30 | 30 | 30 days | 30 days |
Editors’ Note: Intego, Private Internet Access, CyberGhost and Expressvpn are owned by Kape Technologies, our parent company.
Linux VPNs to Avoid
HolaVPN
In spite of having millions of users and some glowing online reviews, HolaVPN was caught collecting data on its users and selling it for profit, negating the entire purpose of a VPN. While it might appear to protect your connection and unblock streaming sites, it’s watching everything you do in the background and might even put malware onto your devices.
Opera VPN
Built into the Opera web browser for Linux, the Opera VPN is actually not a VPN at all — it’s an encrypted web proxy. However, weak privacy and security means it can leak your IP address and other private data. It also won’t hide any of your data outside of the browser environment, such as if you want to watch videos using Kodi or share files in uTorrent.
USA IP
This VPN has a sketchy website with broken links and no privacy policy or terms of use, which is a huge red flag. Every VPN should be 100% transparent and detailed in its privacy practices. USA IP’s marketing materials list privacy-related features, but don’t mention its logging policies at all.
FAQs: Linux and VPNs
How do I manually set up a Linux VPN?
It depends on which distro you’ve chosen. The first step is choosing a quality VPN for Linux. Not all VPNs work well with Linux, so stick to a tried-and-tested VPN. Keep in mind that setting up a VPN on Linux manually is a little more complicated than the basic Windows or macOS installation process. It usually involves adding Linux’s installation file onto a thumb drive.
Utilize a boot command to initiate the OS from the thumb drive instead of relying on your device’s default operating system. This allows you to opt for Linux as the sole OS on your device or maintain both platforms concurrently installed, enabling seamless switching between them.
I recommend you visit the website of your chosen VPN and find its Linux installation guide — it will give you simple step-by-step instructions and you should have your VPN of choice ready to go in about 5 minutes.
Can I use a VPN on Linux to safely torrent?
Which Linux distro is best for privacy?
Can I make my own Linux VPN for free with OpenVPN, WireGuard, or another protocol?
What VPN encryption should I use with Linux?
Can I use a free VPN for Linux?
Yes, but I typically don’t recommend using free VPN providers as they aren’t as reliable as premium services.
You should avoid them for several reasons since free VPNs have slow speeds and bandwidth that give you lower-quality streaming, slower downloads, and laggy browsing. They also enforce strict data caps, giving you a limited time to use the connection and even cutting you off in the middle of what you’re doing. A lot of free providers use ads to make money, constantly interrupting your experience.
There are some decent free VPNs, but completely free VPNs have weaker security including poor encryption. They’re also missing key features like a kill switch or leak protection, and some even secretly gather your data for sale or auction off your bandwidth.
Secure Your Linux Installation With a Class-Leading VPN
Linux may be more secure than Windows and Mac, but you can still fall prey to multiple types of cybercrime without a VPN. If you value your privacy and online security and want to avoid the watchful eye of your ISP, hackers, or even the government, having a VPN is essential.
Even if you’re not worried about your security, a VPN gives you enormous online freedom. VPNs also allow for seamless access to streaming services like Netflix, global news sites, censored content, and geo-restricted apps. However, you need to ensure that your VPN has a graphical Linux client or at least a browser extension for ease of use.
After testing multiple VPNs, I recommend ExpressVPN as the #1 choice for Linux. Each subscription offers high-speed servers, support for numerous Linux distros, and a native client with a simple set of commands so you can easily get connected. It comes with a 30-day money-back guarantee so you can try ExpressVPN out with Linux for yourself completely risk-free. If you’re not satisfied, you can always get a full refund.