Top Password Cracking Techniques and How to Get Protected
Passwords aren’t as safe as you think. In fact, they are vulnerable to different types of attacks, generally known as password cracking. This involves getting access to your accounts by leveraging weaknesses in the passwords themselves or by exploiting human nature.
You’ve probably heard about phishing, brute force attacks, and other methods hackers use to get access to user accounts. However, it’s easy to get protection. A password manager is an important tool in your fight against password cracking, as it helps you by generating secure passwords, auditing the strength of your existing ones, and more.
Among all alternatives, I found that Dashlane offers the best password manager to protect against password cracking. It’s the safest and easiest to use thanks to its military-grade AES 256-bit encryption, friendly web vault, and 1GB of secure online storage.
Protect yourself with Dashlane
Quick Guide: How to Protect Yourself From Password Cracking
- Get a top-tier password manager. I recommend you get a reliable password manager like Dashlane, known to protect against most password-cracking techniques.
- Audit your existing passwords. Use the password manager to check if any of your passwords have been leaked in a data breach, and if they are weak, reused, or vulnerable.
- Change all affected passwords. Once you’ve been alerted about vulnerable passwords, proceed to immediately generate strong passwords as replacements for the affected credentials. You can do this easily with Dashlane’s password generator.
What is Password Cracking?
At its core, password cracking is the process of guessing or retrieving a password to gain access to an account or system. While it’s often associated with hacking and other illicit activities, ethical hackers and cybersecurity experts also use these techniques to identify vulnerabilities and beef up security.
For the average user, understanding password-cracking methods is vital for creating stronger passwords and securing your online accounts. Passwords are typically stored in databases, but the manner in which they are stored significantly impacts how secure they are. If it’s easily guessable or compromised, unauthorized individuals could access your personal data.
So, how are passwords stored, and how can they be cracked?
- Plain Text — Some poorly designed systems store passwords in plain text. These are easy targets for attackers and should be avoided at all costs.
- Hashing — More secure systems use hashing algorithms to convert your password into a fixed string of characters. While more secure, these can still be cracked using techniques like rainbow table attacks or brute-force methods.
- Salting — In the most secure systems, a ‘salt’ — a random string of characters — is added to each password before it is hashed. This makes precomputed attacks like rainbow tables ineffective.
The mechanics of password cracking range from simple guesswork (based on personal information) to sophisticated methods like brute-force attacks (trying every combination) and dictionary attacks (using common words/phrases).
Top Password Cracking Techniques Hackers Use
Hackers sometimes employ sophisticated techniques to bypass even the most seemingly secure passwords. To effectively counter these threats, it’s imperative to understand the tactics these bad actors use.
Social Techniques:
1. Social Techniques:
Guessing is one of the simplest forms of password cracking, relying on manual or automated attempts to guess a password. Many individuals use easily predictable passwords, like “password123” or “admin.”
In 2012, a hacker gained access to a politician’s personal email by guessing the answer to his security question, “What is your favorite pet?” This shows how relying on easily guessable information makes you vulnerable to even the most basic forms of attack.
2. Spidering:
In spidering, hackers collect specialized terminology related to a target organization to construct a tailored dictionary for cracking passwords.
In 2014, attackers used spidering against a major healthcare provider, gathering terms from their public documents and websites to create a custom dictionary. Subsequently, they successfully cracked employee passwords, leading to a significant data breach.
3. Phishing
Phishing is a psychological attack that tricks users into willingly handing over their credentials. Typically, the attacker mimics a trusted source, like your bank or social media site, asking you to “verify” your details through a link that leads to a fraudulent website.
A notorious example occurred in 2016 when Gmail users received deceptive emails mimicking Google’s design. Users were directed to a counterfeit site where they unwittingly entered their credentials, handing hackers access to numerous accounts.
5. Shoulder Surfing
A low-tech yet effective method, shoulder surfing involves directly observing victims entering sensitive data. ATM users, for example, have occasionally fallen prey to onlookers noting down their PINs, leading to unauthorized cash withdrawals later.
6. Social Engineering
This involves trickery and manipulation to get confidential information from the victim directly. The attacker may pose as a tech support agent or a trusted authority to gather information. Kevin Mitnick, a renowned hacker, often posed as IT staff to convince company employees to provide him access or data, showcasing the power of human manipulation in cyberattacks.
Technical Techniques:
1. Malware
Malware encompasses various malicious software, including viruses, worms, and trojans, but when it comes to password cracking, keyloggers are the prime suspects. These tools operate stealthily, recording each keystroke on the victim’s device. This includes passwords, credit card numbers, and other sensitive details.
Attackers can spread keyloggers through phishing emails, malicious downloads, infected websites, or even physical devices like USB sticks. Once the data is logged, it is secretly transmitted to the attacker’s server.
One of the most notorious strains is the ‘Zeus’ malware. Introduced in 2007, it primarily targeted banking credentials. Beyond simply logging keystrokes, it modified web pages, conducted transactions invisibly, and then relayed stolen data to remote servers.
2. Brute Force Attack
In a brute force attack, the attacker doesn’t attempt to guess the logic behind the password; instead, they rely on persistence and computational power. Starting with ‘a’, moving to ‘b’, and so forth, they’ll iterate through every possible combination of characters, be it lowercase, uppercase, numbers, or symbols, until they stumble upon the right one.
What makes this method somewhat feasible, especially against weak or short passwords, is the tremendous processing capability of modern computers. Especially with the integration of Graphics Processing Units (GPUs), which are exceptional at parallel processing (handling multiple tasks simultaneously).
A notable occurrence was the 2012 LinkedIn breach. Cybercriminals obtained hashed passwords and then employed brute force methods. Their perseverance resulted in the compromise of nearly 6.5 million user accounts, underscoring the importance of robust password policies.
3. Dictionary Attack
Unlike a brute force attack, which attempts every possible combination of characters, a dictionary attack is more refined. It’s based on the assumption that many users, either out of convenience or ignorance, use simple, easily guessed passwords — like “password”, “123456”, or “letmein”.
The “dictionary” in this context is a list of likely password words. These lists are constructed from various sources: previous data breaches, commonly used passwords, terms from actual dictionaries, and even popular culture references.
Attackers deploy software that systematically tries each word or phrase from the dictionary against a target account. If the victim’s password is in the attacker’s dictionary, the software will eventually find a match, granting unauthorized access.
Adobe’s 2013 security breach serves as a prime example. Attackers accessed encrypted user passwords and then leveraged dictionary attacks, capitalizing on the ubiquity of weak passwords such as “password” or “123456”, thus compromising millions of user accounts.
4. Rainbow Table Attack
When systems store passwords, they typically don’t save the actual password. Instead, they save a hashed version, which is a fixed-size string of bytes generated from the password input through a specific formula. Even a minor change in the password will produce a vastly different hash. Theoretically, it should be impossible to reverse-engineer a password from its hash.
However, this is where rainbow tables come into play. A rainbow table is a precomputed database of hashes for every possible password combination. They are called “rainbow” tables because they apply a chain of reduction functions to generate a sequence of different hashes and intermediate passwords.
So, when an attacker gets hashed passwords from a breach, they can look up these hashes in their rainbow table. If there’s a match, the table will provide the plaintext password corresponding to that hash. Salting — adding a random string to a password before hashing — can thwart rainbow table attacks by ensuring that even if two users have the same password, the hashes will be different due to the unique salts.
Microsoft’s LAN Manager (LM) hashing, prevalent in older Windows iterations, suffered from a rainbow table attack. Its lack of ‘salting’ rendered it susceptible and allowed the rapid decryption of passwords.
5. Man-in-the-Middle Attack (MitM)
Man-in-the-middle attacks are a prime example of eavesdropping in the digital realm. Just as one might listen in on someone else’s conversation, in a MitM attack, unauthorized intermediaries monitor, capture, and can even manipulate data as it travels between two parties, usually between a user and a server.
One popular avenue for this attack is through rogue Wi-Fi hotspots. If a network has been set up by a malicious actor, every piece of information you send or receive could be captured. With the right tools, like packet-sniffing software, this attacker can extract sensitive details, such as passwords, credit card numbers, or personal messages, from the data you transmit.
6. Credential Stuffing
Credential stuffing attacks exploit one of the most common vulnerabilities: human nature. While it’s much easier for individuals to reuse passwords across multiple sites, it presents a significant security risk. Once a hacker has one set of credentials, they bet on the likelihood that the same username-password combination might work on other platforms.
Given the vast number of breaches over the years, there’s a surfeit of leaked usernames and passwords available on the dark web. Cybercriminals leverage these datasets using botnets or other automated tools. These tools can make thousands of login attempts in minutes, cycling through the vast lists of previously breached credentials.
The logic is simple: if you’ve used the same password for your email, banking, and shopping accounts, a breach in one of these services potentially exposes them all. This is why one often hears about old, seemingly inconsequential breaches coming back to haunt users; the ripple effects can be felt for years.
Most Used Password Cracking Tools
There are numerous tools that professionals and attackers alike use for password cracking. Here’s a list of some of the most popular ones, although it’s crucial to note that using these tools maliciously or without proper authorization is illegal and unethical.
John the Ripper
John the Ripper, often simply referred to as ‘John,’ is a legendary password-cracking tool. Initially developed for Unix systems, it’s renowned for its efficiency and versatility. The tool’s open-source nature, combined with its robust capabilities, has ensured that John the Ripper remains a go-to password cracker for both enthusiasts and professionals.
Upon execution, John automatically recognizes the type of password hash it’s dealing with. Using this information, it then adopts the most appropriate cracking strategy, eliminating guesswork and streamlining the cracking process. At its core, John the Ripper employs several of the techniques we’ve covered to crack passwords, such as:
- Dictionary Attack: Uses a predefined list of words and combinations.
- Brute Force: Tries every possible combination of characters until the right one is found.
- Incremental: A mode where John tries all characters in a specific order, starting from the shortest password length.
John was created for Unix-based systems, and it excelled at cracking traditional DES-based Unix passwords. Today, with community-enhanced versions (known as “John the Ripper Pro” or “community-enhanced John”), its capabilities extend to cracking Windows LM hashes, Kerberos, AFS, and more.
Hashcat
Hashcat is designed to utilize the immense processing capacities of GPUs. By parallelizing computations, it can tackle large amounts of data swiftly, making the daunting task of cracking complex hashes feasible in a relatively shorter time.
Its prowess isn’t just limited to speed. Hashcat supports a staggering variety of hash types, over 300, to be precise. This includes but isn’t limited to, widely recognized hashes like MD5, SHA families, and even platform-specific ones like Windows LM. Such vast coverage ensures that Hashcat remains relevant and effective across different platforms and applications.
Whether you’re running Linux, Windows, or macOS, Hashcat seamlessly integrates and delivers its unrivaled cracking abilities. To ensure maximum effectiveness, Hashcat employs multiple cracking techniques such as Brute Force, Combinator Attack, and Dictionary Attack.
Cain & Abel
Cain & Abel is a multifaceted password recovery and cracking tool primarily designed for Windows platforms. Historically, it has been a go-to solution for many security professionals and enthusiasts alike, owing to its wide range of functionalities combined with a user-friendly interface.
The tool isn’t restricted to a single mode of operation; instead, it can decipher encrypted passwords using multiple techniques like Dictionary Attack, Brute Force, and Cryptanalysis Attacks, often relying on the vulnerabilities present in the system or protocol it’s attempting to crack.
The scope of Cain & Abel spans numerous hash types, making it adept at handling everything from widely prevalent hashes, like MD5 and SHA, to proprietary ones associated with certain software or platforms. Its capability isn’t just limited to hashes. The tool is equally proficient at eavesdropping on network protocols to intercept crucial information.
Ophcrack
Ophcrack is a well-known password-cracking tool, especially for its efficiency in decrypting Windows-based passwords. Its primary allure comes from its utilization of rainbow tables — a time-memory trade-off technique that makes the password recovery process exponentially faster than traditional brute force methods.
Ophcrack’s specialty lies in dealing with Windows password hashes, particularly the LM (Lan Manager) and NTLM (NT Lan Manager) hashes, both of which are cryptographic algorithms used historically by Windows systems. When given a hash, Ophcrack consults its rainbow tables to rapidly identify a matching plaintext password.
Hydra (or THC-Hydra)
Hydra’s specialty is its ability to launch concurrent login attempts, vastly speeding up the process of identifying correct credentials. Instead of a serial, one-by-one attempt, it tries multiple combinations in parallel, ensuring a much higher throughput and potentially quicker discovery of the right credentials.
Hydra is engineered to support a plethora of protocols, extending its functionality far beyond mere website logins. From SSH and FTP to HTTP and IMAP, its scope encompasses a myriad of systems where user authentication is essential.
Aircrack-ng
Aircrack-ng offers a suite of tools explicitly designed for the assessment of Wi-Fi network security. It operates by monitoring and capturing data packets that traverse a Wi-Fi network. Once a sufficient number of packets have been gathered, it then employs advanced cryptographic techniques to attempt a decryption of the network’s password.
It is available and functional on Windows, Linux, and OS X. Focusing primarily on Wi-Fi security, Aircrack-ng can penetrate and recover a broad spectrum of passwords. From the older and now largely deprecated WEP (Wired Equivalent Privacy) to the more modern and secure WPA (Wi-Fi Protected Access) and WPA2 standards.
It monitors network traffic, identifying potential vulnerabilities and points of interception. It can deploy de-authentication attacks, forcing devices to reconnect and thus allowing the capture of handshake data. Once data is captured, the tool uses cryptographic techniques to attempt the decryption of passwords, leveraging weaknesses in WEP, WPA, and WPA2 standards.
The Best Password Managers to Protect From Password Cracking (Tested in 2024)
1. Dashlane — #1 Password Manager to Protect From Password Cracking
Key Features:
- Uses AES-256 encryption to protect your passwords from cracking.
- Lets you generate very secure passwords to protect your accounts.
- Alerts you when any of your passwords appear on the dark web.
- Provides a VPN to encrypt your connection when browsing.
- Backed by a 30-day money-back guarantee.
Dashlane stands as a frontline defense against password cracking. It encrypts your passwords using AES-256 encryption, making it virtually impossible for attackers to decipher them. When I tested this, even sophisticated cracking techniques took ages, effectively making it a futile endeavor for hackers.
With Dashlane’s password generator, you’re shielded from making basic password mistakes. I tested the generator, and it consistently created strong, random passwords that defy dictionary and brute-force attacks. This means you get optimal password strength without the headache of crafting it yourself.
The Dark Web is a place where stolen passwords can be traded. Dashlane’s Dark Web Monitoring proactively scans this hidden part of the internet, alerting you if your credentials appear. From my experience, this gives you a critical head start to change compromised passwords before they can be misused.
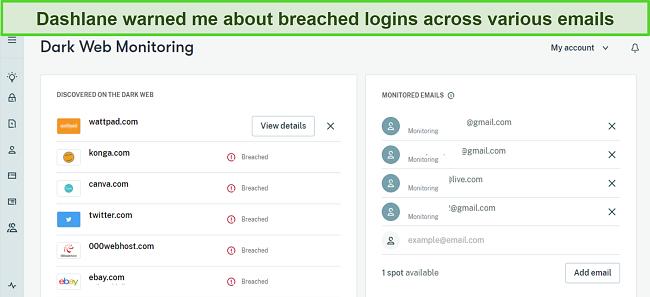
One of the features I appreciate most is the password auditing tool. It scans and assesses the strength of all your stored passwords, flagging the weak ones. This way, you know which passwords need changing, keeping your online presence fortified against potential attacks.
Two other standout features include:
- VPN for Wi-Fi Protection: A VPN adds a layer of security to your online activities to help prevent man-in-the-middle attacks.
- Secure Document Storage: A safe place for your sensitive documents, encrypted and away from prying eyes.
Dashlane offers various plans, but the Premium plan is a popular choice, offering comprehensive features like unlimited password storage and device sync. If you’re looking for optimal protection, this plan is a worthy consideration. Plus, there’s a 30-day money-back guarantee, making your decision to protect yourself even more straightforward.
2. 1Password — Top-Tier Security Features to Keep Your Passwords Safe
Key Features:
- Protects your passwords against cracking using AES-256 encryption.
- Monitors to see if your information has been exposed to security breaches.
- Creates robust and secure passwords to safeguard your accounts from cracking.
- Alerts you about weak, reused, and other vulnerable passwords.
- Provides a 14-day money-back guarantee.
1Password has rightfully gained a reputation for prioritizing password security above all. Leveraging end-to-end encryption, it shields your passwords from prying eyes. When I conducted tests, I found that without the master password, accessing the vault’s contents was practically impossible, adding a robust layer against potential intruders.
The built-in password generator is exceptional. During tests, it consistently produced complex passwords resistant to dictionary and brute-force attempts. It offers a reliable way to fortify your accounts against cracking techniques while alleviating the burden of creating secure passwords yourself.
1Password’s Dark Web Monitoring, known as Watchtower, scans databases for compromised credentials. It alerted me when my information was spotted, providing a crucial window to change the password and fend off unauthorized access.
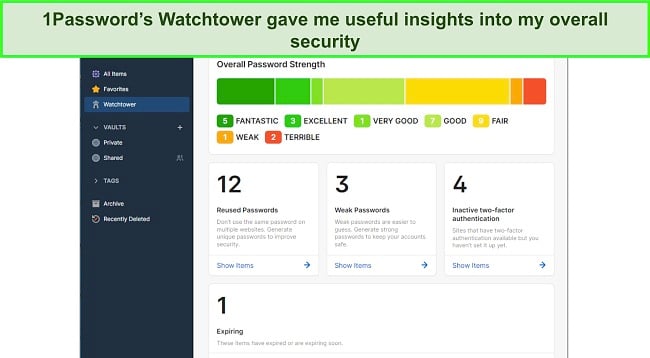
The password auditing function identifies weak links among your saved credentials. In my experience, this feature guided me to reinforce passwords that could be susceptible to cracking attacks, ultimately making my digital life more secure.
A couple of additional standout features are:
- Travel Mode: Shields sensitive information during travel by making it inaccessible.
- Secure Document Storage: Offers encrypted storage for important files.
If you’re considering a subscription, the 1Password Family Plan allows for secure password sharing and comes with 5 licenses, making it a solid choice for households. To top it off, there’s a 14-day money-back guarantee, giving you ample time to assess its efficacy.
3. NordPass — Secures Your Passwords With Top-Grade Encryption
Key Features:
- Uses XChaCha20 encryption to secure the data from password cracking.
- Provides multi-factor authentication for enhanced password security.
- Generates secure passwords to protect all your accounts.
- Check if any of your logins have been compromised in a data breach.
- Comes with a 30-day money-back guarantee.
NordPass employs XChaCha20 encryption, a cutting-edge standard that’s known for its resilience against all current cracking techniques. Through my testing, this encryption mechanism effectively warded off attempts to decipher stored passwords.
In its arsenal, NordPass has a dynamic password generator. It spontaneously crafted intricate passwords, throwing dictionary and brute-force attackers off the trail. These passwords are much better against the usual password-cracking tactics.
Cyber risks are everywhere, but NordPass actively scans the dark web for signs that your credentials are leaked. When I tested this Dark Web Monitoring, I was promptly notified about potential vulnerabilities, allowing swift password changes.
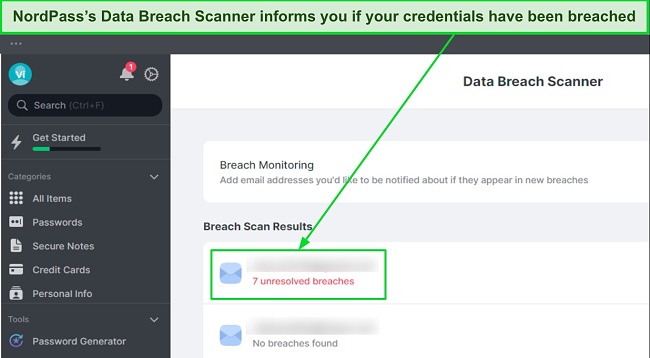
NordPass doesn’t just store passwords, but it also helps to secure your online credentials. Its password auditing tool highlighted any weak or duplicate passwords in my vault. This insight pushed me to make necessary changes, reinforcing my defenses against cracking.
A couple of features that deserve special mention are:
- Biometric Login: Offers quick access using facial recognition or fingerprints.
- Secure Sharing: Safely shares credentials without exposing your actual password.
For holistic protection, the NordPass Premium plan has the added advantage of sharing with trusted people and secure access on multiple devices. It’s my top pick for individual users. To provide more assurance, it’s backed by a 30-day money-back guarantee, letting you evaluate its capabilities risk-free.
Quick Comparison Table: 2024’s Safest Password Managers
| Password Generator | Password Auditing | Dark Web Monitoring | 2FA | Money-Back Guarantee | |
| Dashlane | ✔ | ✔ | ✔ | ✔ | 30 days |
| 1Password | ✔ | ✔ | ✔ | ✔ | 14 days |
| NordPass | ✔ | ✔ | ✔ | ✔ | 30 days |
How I Tested and Ranked the Safest Password Managers in 2024
Picking the right password manager isn’t just about convenience; it’s about security. Throughout this year, I’ve rigorously tested various password managers against a strict set of criteria to determine which truly offers the best protection. Here’s what I focused on:
- Encryption Strength: The backbone of any password manager is its encryption. I delved deep into the encryption algorithms used and their implementation to ensure they meet modern security standards.
- Zero-Knowledge Architecture: I evaluated if the password manager employs a zero-knowledge model, ensuring that only you have access to your data and not even the service provider can view it.
- Password Generation: A vital feature, I tested the strength and uniqueness of passwords generated by the software, ensuring they are complex enough to deter cracking attempts.
- Dark Web Monitoring: Cybersecurity isn’t just about defense but proactive offense. I checked how these tools monitor the dark web for potential data breaches involving your credentials.
- Cross-Platform Compatibility: It’s imperative that a password manager works across all devices you use. I tested compatibility with various operating systems and browsers.
- Pricing & Value: While safety is paramount, value for money remains important. I compared features against subscription prices to determine which tools offer the best bang for your buck.
FAQs on Password Cracking
What is password cracking?
Password cracking is the process of deciphering or guessing a password to gain access to an account or system. It involves techniques like brute force, dictionary attacks, and others, leveraging both software tools and human ingenuity. The goal can be benign, such as password recovery, or malicious, like hacking.
How can I protect my passwords from cracking?
To protect your passwords from cracking, adopt the following measures: First, generate strong, unique, and unguessable passwords—lengthy combinations of letters, numbers, and special characters work best. Avoid using easily accessible personal details. Second, change your passwords regularly.
A reliable password manager is invaluable in this respect. It not only creates robust passwords for you but also stores them securely. Furthermore, premium password managers like Dashlane monitor the dark web for any leaks involving your credentials, promptly alerting you. Lastly, always use two-factor authentication for an added layer of security.
Is cracking passwords legal?
Cracking passwords walks a fine line between legality and illegality, with the determining factor being authorization. If you have explicit permission to access or attempt to decipher a password — for example, in cases where you’re participating in a bug bounty program or helping someone at their request — you’re within legal boundaries.
On the other hand, attempting to crack passwords without such permission or any form of authorization usually constitutes illegal activity. This could lead to severe legal repercussions, depending on the jurisdiction and the severity of the breach.
It’s worth noting that the tools used for password cracking aren’t illegal by nature. Their legality is contingent upon how they’re used. Just as a locksmith’s tools can be employed for legal tasks or misused for break-ins, password-cracking tools can serve both lawful and unlawful ends.
How can I recover a lost password?
If you’ve lost a password, you can often recover it using password recovery options on the respective service, or by using specialized tools like those mentioned above for lawful and authorized purposes. However, a more efficient, long-term solution is to use a password manager.
With a password manager, you only need to remember one master password, and it takes care of the rest. It stores all your passwords securely, generates strong and unique passwords for you, and even monitors for unauthorized access or leaks. A password manager is a comprehensive solution for credential management and security.
Protect Your Passwords From Cracking With the Best Password Managers
Hackers can use password-cracking techniques to get hold of your passwords and take over your accounts or steal your personal information. That’s why you need to be aware of the methods and software they often so you can protect yourself.
The best way to protect yourself is by using secure passwords and best password security practices. And that’s where a password manager comes in. I tested dozens of password managers proven to protect against password cracking and found Dashlane provides the best protection against cracking techniques.