Phishing in 2022: Wrapping Up a Record-Breaking Year

Phishing scams continue to plague the internet in 2022, more now than ever. This article explores the latest data and current trends and shows you how to avoid a phishing attack today.
Introduction
Records have been broken already in 2022, but not the good kind.
Cybercrime consultants have found over a million discrete phishing attacks perpetrated this year, which is up by 61% in the same time period in 2021.
In a recent sophisticated phishing attack, customers of the Dutch bank MKB were targeted with a fake newsletter that purported to be from MKB. The newsletter asked customers to follow a link to find out more about how the bank was supporting customers through the pandemic. The link took victims to a phony authorization page that stole their Outlook login credentials.
This is the kind of cybercrime that was on the rise in 2022.
Phishing is a type of online scam in which people are tricked into giving up personal information like passwords, banking log-ins, and contact details.
People who have to spend more time online – completing transactions, working, studying, and socializing – appear to be more vulnerable to phishing attacks. This includes younger people, who tend to use digital products more often and are therefore exposed to more potential online scams.
But everybody is using the internet and digital products more often now than ever.
In 2020, the global pandemic of COVID-19 caused a huge surge in people working remotely, using new digital products to collaborate and communicate. This was seen as a golden opportunity for online scammers. The global switch to remote working led to a 12-fold increase in the number of phishing emails sent to work accounts.
But the pandemic really just made an already established trajectory a lot more steep: every year, more people are making more interactions than ever online.
In this context, it’s not really a surprise that the number of phishing attacks detected by security experts keeps creeping up.
This article details the tactics and methods used by scammers in 2022 and shows you how to avoid a phishing attack in the near future.
Giving up personally-identifying information can lead to identity fraud, with scammers able to take out credit in the victim’s name. Company secrets and sensitive business information can be stolen from an organization’s systems if employees fall victim to phishing attacks at work. In the most extreme cases of phishing, people’s entire bank accounts can be emptied and their lives ruined.
Phishing in 2022

Of all the different types of online scams, phishing is by far the most common. More than 80% of reported security incidents are some kind of phishing attack, according to recent research.
Phishing attacks have increased by 61% since 2021, with over a million discrete attacks detected by security experts so in 2022. In 2020, only about 40,000 phishing reports were found in one month, April 2022 saw 100,000 attacks.
A separate report found just over a million total attacks in the first quarter of 2022 alone – the first time over a million phishing attacks had been detected in a 3-month period in that report’s history.
More activities than ever before are now conducted online.
This includes personal and work relationships through email and social media, banking; shopping; accessing social and state services, education, and all aspects of work. And official entities like banks, brands, government services, schools, and colleges now communicate with customers and users through email and SMS as well.
The online nature of everything makes it easier for scammers to make a successful phishing attack. The sheer quantity of communication that people need to sift through makes it harder to spot scams. Attacks also often use personal information that people publish on the internet for anybody to see.
But online scams are as old as the internet itself. That is because they require much less investment to carry out than real-life cons, and they are harder to stamp out.
The infamous Nigerian prince scam is an example of how the internet made it much easier for fraudsters to dupe victims and get their money.
This scam actually existed long before the advent of the internet, when contact was made through letters or faxes. The widespread adoption of email in the 1990s enabled scammers to target far more people at no extra cost.

Now, it is pretty easy to spoof an email address, fake an official website, and target hundreds of thousands of people at once.
All of this can be done behind a nearly impenetrable mask of anonymity, so fraudsters are rarely caught. When online scams are eventually taken down or removed, they can easily be copied and pasted to another website or server, and the scam can continue.
And it’s successful. Phishing was the single greatest cause of data breaches in businesses in the US in 2022.

Tragedies and disasters always come with their share of criminals and hucksters, and experts this year have warned that cybercriminals are using Russia’s war in Ukraine to “hook” phishing attacks onto. Over a tenth of emails about Ukraine detected by cybersecurity experts Vade between January and March 2022 were actually phishing attacks.
With the 2021 high price of Bitcoin falling and cryptocurrencies crashing in 2022, crypto suddenly became a much more popular scam topic for cybercriminals. Researchers noted a 257% increase in cryptocurrency-related phishing attempts from 2021.
Delivery companies became the main target for copycats carrying out phishing scams after the outbreak of COVID-19, but this trend slowed in 2022. Now, the brand that is impersonated in phishing attacks more than any other is the professional social network LinkedIn.
Setting up a phishing scam in 2022 is just like building up a technology stack for an e-commerce business.

Templates and software now exist to make the job of the scammer even more straightforward as well. A recently discovered criminal fraud package, LogoKit, helps scammers set up fake web pages for phishing attacks. Even though it was discovered last year, criminals were still using LogoKit for phishing attacks in 2022.
Kits like this can be bought on the dark web for only a few hundred dollars each. They also follow a broader internet trend: no-code software.
Services like Squarespace and Wix make it easy for anybody to create a professional-looking website, regardless of their level of technical expertise. Similarly, criminals can use specially-made software like LogoKit to make a sophisticated fake phishing page with very little expertise.
Different pieces of software, programming scripts, and databases that are all readily available (on the dark web and through criminal networks) are stacked together to make a sophisticated scam with minimal effort required.
A highly prolific phishing group known as EMOTET was disrupted by international law enforcement in early 2021, but it resurfaced in 2022. The group has already caught the attention of the cybersecurity community and is busy scamming victims again.
And cybercriminals are literally advertising “Phishing as a Service” packages on popular crime websites today.
The package allows criminals to conduct sophisticated phishing attacks on large, important technology companies like GitHub, Microsoft, and Apple. Security analysts believe this indicates criminals are trying to sneak “backdoor” vulnerabilities into official software with millions of users worldwide.
As a result of all this, phishing is more widespread today than ever.
In fact, more than 80% of all reported cybersecurity incidents are phishing attacks. These attacks are working: in the United States, 74% of all organizations have been victims of a successful phishing attack.
How Does Phishing Work?

Today, phishing scammers use a few different ways to make contact with their victims. By far, the most common approach is through email. 94% of all malware (malicious software including viruses) is now delivered by email. It is popular because it is essentially free to send hundreds of thousands of emails at once.
The scammer makes contact using what appears to be an official email address and asks the victim to go to a fake website and input their details. The scammer then has access to these details through the fake website.
Once the scammer has access to personal details, they can cause significant harm to people’s personal finances, organizations, and businesses.
With the advent of smartphones, more phishing attacks are now carried out through SMS messages as well. This exploits a trend in which many services like retail delivery and banking are communicating with their customers through SMS messages.
Voice phishing uses robocall technology to automatically call people on their phones, asking them to give up personal details or go to a spoof website that they’ve been emailed or messaged about.
Shareable content on social media can also be used to deliver phishing attacks to people’s feeds, as well as message and chat features on other digital products like online games.
The deluge of information that we consume online also makes it easier for online scammers to trick us into trusting them.
Online information is consumed quickly; we are scrolling past hundreds of posts from a huge variety of sources all the time. This vast quantity of information is unprecedented, and our brains are ill-equipped to deal with questions of authenticity and trust at such volumes and speed. Online scammers rely on this facet of modern life to sneak illegitimate information past our natural skepticism.
Phishing Tactics Used by Scammers in 2022
As well as using different means to make contact with victims, phishing scammers also use a variety of tactics and techniques to carry out their attacks.
Some of these are technological, relying on the advantages of digital media and the internet (infinite reproducibility and easy anonymity). Others are psychological, employing con-artist tactics that criminals have used for millennia to gain victims’ trust.
Bulk Phishing

This tactic takes advantage of the infinite reproducibility of digital media and methods of communication, with scammers casting the widest net they can.
In a bulk phishing attack, the phishing message is sent to as many people as possible.
Contact email addresses can be obtained from a previous phishing attack or purchased through criminal networks. Bulk phishing attacks are often not that sophisticated: most people would not be fooled by them, and most spam filters will stop them from appearing in people’s primary inboxes.
However, the law of large numbers works in favor of bulk phishing scammers. If you make enough attacks, you will almost certainly find a small number of victims who are ready to give up their personal information.
Digital and anonymous communications should always be treated with a degree of suspicion, considering how easy it is to impersonate pretty much any person or organization.
A company you have a relationship with, such as a utilities supplier or insurer, will use your name when they contact you. You can spot many scams from the first line of the email; “Hello Dear Customer,” and other generic greetings are sure warning signs.
Making sure that your friend or colleague’s message reads like something they would write, or that a brand is communicating in a way you would expect it to, is an excellent way to sniff out potential attackers.
Spear Phishing

In contrast to bulk phishing, spear-phishing attacks are more sophisticated and more likely to succeed. In organized online crime, it is estimated that 65% of cybercriminal organizations use spear-phishing as their main point of attack.
Scammers try to find out as much information about the victim as possible, often gleaned from public social media profiles. They then use this information to try to gain their victim’s trust.
Alternatively, spear-phishing attacks might target an organization, event, or workforce.
Spear phishing was used to gain access to Gmail accounts linked to Hilary Clinton’s 2016 presidential campaign. The hacker group known as Fancy Bear targeted 1,800 Gmail accounts linked to the campaign, using a fake Google website (for example, accounts-google.com) to gain their trust.
A global spear phishing attack targeting the cold chain for COVID-19 vaccines was identified by a special IBM Security X-Force task force set up to combat COVID-19-related cyberattacks. This was a coordinated attack targeting multiple organizations supplying vaccine materials or managing the logistics of the vaccine cold supply chain.
If the information you are receiving is entirely new to you, that is another good sign to take a closer look and check if you are being scammed. If, for example, this is the first time Netflix is contacting you about a missed payment, be more alert for a potential phishing attack.
If you are suspicious about a message from a friend or colleague, you can always contact them through a different mode of communication and check in with them. If they are being impersonated, they would want you to warn them as soon as possible.
Whaling

Whaling is an even more targeted version of spear phishing.
Whaling attackers invest a lot of time and resources into getting information that they can use to convince high-profile figures to hand over their personal information, contacts, and log-in details. Corporate executives, politicians, and other high-profile figures with a lot of responsibility are common targets for whaling attacks.
Scammers will find out about their schedule, personal contacts, and ways of working to make their phishing attacks more convincing. Successful whaling attacks can provide fraudsters with confidential business information, secret political activity and plans, and log-in details for corporate systems and finances.
A couple of years ago, an executive at one of the top 50 companies in the world for innovation was targeted with a sophisticated whaling attack. The executive received an email with what appeared to be a company financial report attached. When they clicked the attachment, a fake Microsoft Office 365 login page with their username already entered appeared. This was enough to dupe the executive, who gave up their password.
Another recent whaling attack targeted the co-founder of Levitas Capital, an Australian hedge fund. The attacker sent an email with a fake Zoom link to the co-founder. When they opened the link, a piece of malware was placed on the hedge fund’s network. This virus created $8.7 million of fraudulent invoices and placed them on the hedge fund’s pay system.
Ultimately, the attackers only managed to defraud the hedge fund of $800,000. However, the damage that the attack caused to the hedge fund’s reputation turned out to be irrevocable. It lost its largest client and was subsequently forced to shut down.
Business Email Compromise (BEC)

Another reward for a successful whaling attack is the email address of a senior figure in a business or organization. Using this, scammers can then contact the entire workforce and automatically gain their trust with what is known as a BEC (business email compromise) attack.
A company-wide email from the CEO instructing staff to deposit money into an offshore bank account, for example, can return significant financial rewards for scammers.
Sometimes, the attackers do not even need to use the executive’s company email address. A convincing email from what purports to be an executive’s personal email address can often be just as effective.
In fact, 82% of BEC messages detected in the first quarter of 2022 were from free webmail accounts, with 60% of these using Gmail.
Austrian aerospace company FACC lost $61 million to a BEC attack. A low-level accountant at the company received an email that appeared to be from FACC’s CEO. The email instructed the accountant to transfer the funds to several foreign accounts in order to fund a new project. Unfortunately, this attack was very successful, and the accountant sent all of the requested money.
Like with personal emails, you should always be on the lookout when receiving emails at work. If someone with more seniority than you asks you to do something outside of your responsibilities or contacts you using a method of communication that you usually don’t (SMS instead of Slack or Teams, for example) — make sure to check with someone before taking any action.
Link Manipulation
Phishing scams that direct victims to a website where they are instructed to input login details need to make their website appear official and trustworthy. One of the ways they do this is with link manipulation.
This is a tactic to make URLs appear official. Sometimes they will replace letters in the URL with letters that look similar (such as lowercase “r” and “n” together that look like a lowercase “m”). This is known as the homograph exploit (homograph means words that look identical). In the attack on Hilary Clinton’s presidential campaign, scammers only had to include the word “google” in the URL to make it look convincing.
Scammers also exploit ignorance about URL conventions to make their links look legitimate. The URL “bankname.scamsite.com” might look like a page on the bank’s website, but it is actually a page on the scam site. A similar tactic is sometimes used to fake an email address in order to carry out a CEO fraud attack.
Scammers also try to blend phishing attacks with the usual workflow in order to bypass victims’ sense of security. Securelist reported on an attack that sent a desktop notification that appeared to be from Microsoft Planner (it was actually a browser notification). The notification suggested that victims review their upcoming tasks by clicking a link. The link took them to a phishing page designed to get hold of their Microsoft login information.
If you feel suspicious about clicking a link, it’s a good idea to type it out manually instead. This will reveal any homograph attacks as you type out each letter individually. You could also head to the organization’s social media and make sure the URL you have been given is the same as their official website.
Page Hijacking

Sometimes, phishers will obtain login information for website administrators and then use the actual website to carry out their scam.
Of course, this is much harder to carry out. It involves a separate scam (or a bribed employee) to get the admin login details in the first place. It is also relatively easy for the organization to quickly shut the scam page down and reset admin log-ins.
However, more sophisticated versions of this attack can go undetected for a little bit longer. If real pages on the website, such as contact forms and payment processing pages, can be faked convincingly, they may also dupe the website owners.
A voluntary humanitarian campaign in Venezuela was targeted with page hacking in a recent phishing attack. The campaign’s official website included space for volunteers to participate in the campaign. In order to partake, volunteers had to enter personal data, including their name, government ID, phone number, and home location.
Scammers soon created a fake site that looked almost identical to the original, had a similar URL, and used the same IP address. Thousands of volunteers lost their personal data to the scammers in this attack.
Filter Evasion

Spam filters are, in general, pretty good at catching most malicious emails and preventing users from opening them.
However, recently scammers have been using images of text to evade these filters. The bulk of spam filtering is done through automated machine-reading and scanning for keywords. There are sophisticated AIs that can read text in an image, but not all email clients use this for spam filtering yet.
Caller ID Spoofing

Most people do not know that it is relatively easy to make cell phones display any caller ID that you wish.
This is a common tactic for phone phishing attackers, who will spoof caller ID to gain their victim’s trust. Scammers can use a spoofed caller ID to make robocalls or send SMS messages.
For example, a popular scam sends victims an SMS that looks like it is from their country’s customs agency. The message instructs them to reply with personal information in order to release a package that is being held.
In Singapore, an SMS phishing campaign was responsible for $800,000 of stolen money from 374 individual cases in just three months. Victims were sent SMS messages that appeared to be from their bank. This impersonation led victims to give the attackers access to their money, which was stolen.
These attacks can also come from people posing as your employer. If you ever get a message from someone claiming to be your employer but asking you to do things that feel odd, for example purchasing gift cards or transferring money — make sure to check in with them personally before doing anything.
Social Engineering

All of these tactics and techniques rely on some kind of psychological manipulation to gain victims’ trust; this is known as social engineering.
The main psychological tactic is simply impersonating a trusted entity such as a senior executive or a well-known digital service.
Alongside this, most phishing scams also invoke a sense of urgency in order to bypass victims’ natural wariness. Targets are told that their account will be suspended, for example, if they do not submit their personal details immediately.
Another social engineering technique sparks an emotional reaction with a fake news story, encouraging victims to click a link to donate or find out more information. Because they are in an emotional state, it is harder for their reasoning and intelligence to spot the fraud. This tactic works by bypassing the victim’s usual analytical skills with an emotional response.
Yet another common way of circumventing a victim’s reasoning by engaging their emotions first is creating a fake profile using a friend or family member’s photos and publicly available information. This spear-phishing method creates trust, making it easier for the scammer to get the victim to do what they want.
Spectrum Health System reported a phone call phishing attack targeting its patients recently. Patients received phone calls from people who were pretending to be Spectrum Health employees. The calls aimed to convince the victims to give up personal information such as their member ID numbers and health data associated with their Spectrum Health accounts.
According to the organization, the scammers used flattery and even threats to put pressure on their targets and ensure they handed over the information asked for. In some cases, they were even able to make victims give up access to their personal devices or directly transfer money to offshore accounts.
When someone calls or texts you to inform you of an emergency, be wary of demands for things immediately. This isn’t normal in most situations. To avoid acting rashly, the best thing to do is tell the person you will call them back and hang up. Then you can call an official number and check if there is something actually wrong. For example, call the number for your health insurance that is listed on the back of your card.
How to Spot a Phishing Attack
Pretty much anybody can fall for a phishing attack.
But if you learn a few tell-tale signs and red flags to look out for, you can be more prepared to spot a phishing attack before you fall victim to it.
Here are some top tips to help you spot a phishing attack in the wild and avoid it!

Learn to trust your spidey senses. If something doesn’t seem right to you, there’s probably a good reason for that!

Do you recognize the email address, phone number, or social media profile? Does it look like your friend’s account might have been hacked?

If your bank or other services contact you, they will use your name if they have it. Be wary of generic greetings like “Hello Dear Customer”.

If this is the first time you’re hearing about a problem with your payments, or you’ve never been asked to log in like this before, then it’s a good sign the message isn’t legit.

If you type the link out in your browser manually you can easily spot a homograph attack. Before you open a link in an SMS, always check the URL – is this the company’s official website?

If you get an email or text message from your boss asking you to transfer money to an unusual account, it’s absolutely fine to send them a quick message on chat or knock on their office door to check if they definitely sent it.

Using the best security protocols and keeping your software and devices updated will also help you to spot and avoid phishing attacks.
Two-factor authentication (or more) will protect your accounts if your password is ever compromised, and regular updates on your cell phone root out security weaknesses.
You can also back up your data to protect yourself from hackers. Some cloud backup services even give you the ability to remotely wipe any device should it be hacked or fall into the wrong hands.
Are Digital Natives More Vulnerable to Phishing Attacks?
Millennials (born between 1980 and 1995) and zoomers (born between 1995 and 2010) fall victim to phishing attacks in greater numbers than any other generation.
People who grew up using digital technology from a very young age – that’s most zoomers and younger millennials – are sometimes called digital natives. But these numbers seem to show digital natives falling victim to phishing scams more often than people who likely adopted digital tools later in life.
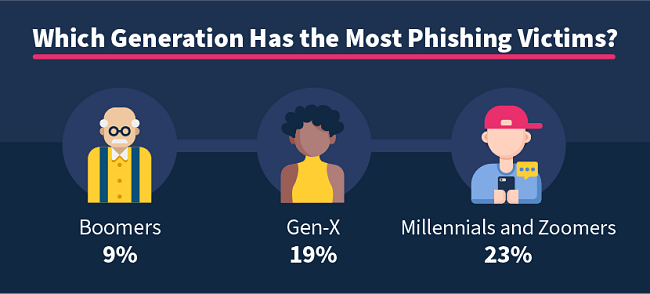
A recent survey of 3,500 US adults found that 23% of millennials and zoomers had been caught out by a phishing scam at some point in their lives. This was compared with 19% of Gen X (born between 1965 and 1980) and only 9% of baby boomers (born between 1950 and 1965).
Some reports cite younger generations’ familiarity with digital technology as the reason that they fall victim to online scams in greater numbers. Microsoft puts the blame on too much confidence in themselves and their ability to spot a fraudulent message or web page.
But we have to look at these (slightly) higher phishing rates alongside the fact that millennials and zoomers spend far more time online than older generations, and their online behaviors are also different.
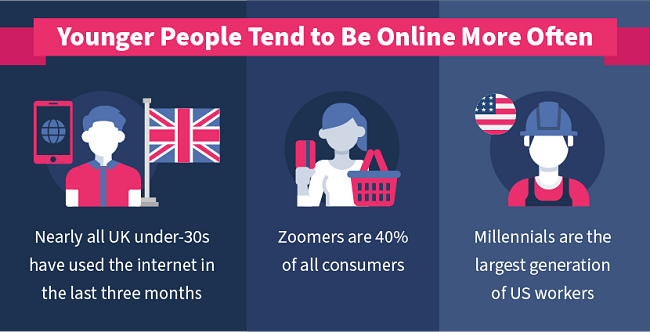
A recent UK report found that almost everybody under the age of 30 had used the internet in the last three months. In contrast, there were more over-50s who had not used the internet in the last three months than there were those who had.
Zoomers are the largest generation in terms of the global population and make up 40% of all consumers worldwide. There are more millennials in US workplaces than any other generation.
Younger generations are more affected by trends in online activity than older generations.
There are more of them in total, and there are relatively more of them making transactions online and in the workplace. So there are more opportunities for them to come into contact with phishing and other online scams.
Millennials and zoomers also behave differently online than older generations.
Younger people consume digital media more quickly than older people and are more used to accepting information from a variety of sources. They use digital services like app-based transportation more often than older people. At work, they use a plethora of digital tools to do business; Slack, company social media, Canva, CRMs, and numerous SaaS products now compete for attention with email on the office worker’s laptop.
Younger generations also feel more comfortable using payment methods like PayPal. Over nine-tenths of millennials use banking apps or make payments using their smartphone. Younger people also engage in riskier online behavior than older people, such as using torrent sites.
Younger generations are online more often, and they conduct more aspects of their daily lives online or with online tools. So they are bound to encounter more phishing attacks and be more vulnerable to cybercrime in general.
They aren’t easier to scam online, just a little easier to find and engage due to their numbers and typical behaviors.
Protecting People Against Phishing Attacks
The police and agencies like CISA in the United States, and international organizations like INTERPOL and UNODC are engaged in a perpetual war against online scammers and phishing attacks. Working with technology companies, ISPs, and domain hosts, they take down as many illegal online scams as they can.
However, the digital nature of these scams means that they are easy to copy and paste onto another domain just as soon as they are taken down.

The regulatory battle against online scams is like a game of whack-a-mole; as soon as one phishing site is taken down, another will pop up in its place.
The best way to protect people of any generation from any kind of fraud is through education. If people are more aware of the threat of scams, then they are better equipped to avoid them.
But to place all of the responsibility for education onto potential victims themselves misses some key opportunities to educate more people and protect them from phishing attacks.
Instead, numerous public and private organizations working together to educate their users and customers will have a more significant impact on protecting people from phishing attacks.

This should start in the school and college system. Learning institutions are already set up to impart useful information to young minds. Ensuring that students leave these institutions with the skills they need to navigate the online world safely should be a key focus for educators.
Skills like critical thinking, evaluating sources, spotting warning signs like being asked to transfer money or give up personal information, and protecting your privacy online could all be fostered throughout the education system.
Employers can also proactively educate their workforce about phishing attacks and other kinds of online scams. They have a vested interest in doing so, as businesses stand to lose significant sums of money or face reputation damage if their systems are compromised.
In the workplace, digital security education should be an ongoing process that involves everybody in the workforce. (Many whaling attacks are successful because senior executives do not attend cybersecurity trainings that are mandated for lower-level staff.)
Libraries and community centers also have a role to play in this kind of practical, everyday digital skills education. As do families, friends, and caregivers – we can all help others learn!
Schools, colleges, and employers alike can also take proactive steps to prevent their students and employees from falling victim to online phishing attacks.
Identity theft protection and other security services can help to reduce the risk of phishing attacks causing harm. Security protocols like two-factor authentication should become the default for all organizations with an online network.
Banks, P2P payment providers like PayPal, Square, and Venmo, as well as technology companies all have a vested interest in ensuring their customers and users are protected from online fraud.
Many banks already work hard to ensure their customers have plenty of information and training available to get informed about online scams. Facebook has recently introduced measures to warn users about suspicious requests on the Messenger app.
Conclusion
The more time people spend online, the more vulnerable they are to online fraud. This is demonstrated by the fact that millennials and zoomers who spend more time online than any other generation also fall victim to more phishing attacks than other generations.
As younger generations make up the majority of the economy, they will be targeted by more phishing attacks and online scams. They should work hard to ensure their confidence in using online services does not leave them vulnerable to phishing attacks. But large organizations also need to bear some responsibility for ensuring that as many people as possible are well-educated when it comes to online fraud.
Cons are as old as history itself, and criminals will always find ways to exploit our natural psychological tendencies for their benefit. But with continual education and vigilance, individuals and organizations can learn to protect themselves.
What To Do If You Fall for a Phishing Scam
Follow these steps if you think you’ve already fallen for a phishing scam.

If you realize you have fallen for a phishing scam, try to disconnect your device from the internet as soon as possible. Put your laptop or phone on airplane mode, and switch the WiFi off as well if possible.
You might be able to stop the hacker from installing malware on your machine or getting remote access to your device if you act quickly.

You also want to try to remember any information you provided and note it down. This will help you later when you are recovering your accounts.

Taking a screenshot of the phishing email, fake website, or SMS message now is also a good idea. The hacker may quickly delete web pages after their scam is complete, and you can help targeted companies or the authorities by saving some evidence.

If you gave the scammer any passwords, make sure you log onto those accounts as soon as possible and reset your passwords and security questions.
If you use the same password for multiple accounts (please don’t do this!), you will need to change the passwords and check for signs of unauthorized access on all of those accounts as well.

As well as looking at your account details, check your recent direct messages, sent emails, or SMS messages to see if the attacker is also targeting your contacts.

Run an antivirus scan of your devices to determine if the hacker installed any malware when they had access to them. Some viruses are designed to evade detection from common antivirus software, so if you are especially concerned, it is a good idea to hire a computer security expert for help.

If you gave up sensitive information like your bank account details or Social Security number, you will need to be vigilant against potential identity theft. Read your bank and credit card statements carefully, and use online banking to monitor all of your spending.
You can ask your bank to alert you about any suspicious activity on your cards and even set up payment notifications to get an alert every time a payment is made from them.

Make sure you alert the organization or company that the successful phishing scammer impersonated. Any screenshots or details you saved from the attack will be helpful for them so that they can protect other customers.

You can also report to the appropriate authorities in your country if you have been attacked. This information can be used to safeguard others from falling victim to similar scams.
Sources
11 Types of Phishing + Real-Life Examples – Panda Security
16-24 year olds most likely to be scammed online – Tech Advisor
2021 Phishing Trends to Watch For – Inky
4 things fintechs need to know about Gen Z – Sifted
COVID-19 Cybercrime Reminder: 5 Examples of Phishing Emails That Killed Companies – Inky
Cybercriminal Service ‘EvilProxy’ Seeks to Hijack Accounts – Data Breach Today
Did your organization experience a successful phishing attack in 2020? – Statistica
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign – Securelist
Generation Influence: results from the 2020 Gen Z report – WP Engine
Generation Z is bigger than millennials — and they’re out to change the world – New York Post
Generation Z, millennials most likely victims of tech support scams: Microsoft – The Hill
Generational Differences in the Workplace – Purdue University
Generational fraud tactics: from millennials to boomers – Mitek
How the Russians hacked the DNC and passed its emails to WikiLeaks – Washington Post
Internet Security Threat Report – Symantec
LogoKit update: The phishing kit leveraging open redirect vulnerabilities – Help Net Security
Millennials, Gen Z and Males Are the Most Vulnerable Groups for Tech Support Scams – Microsoft
New type of phishing scam targets bank customers with spoof SMSes: Police – Channel News Asia
Phishing Attacks Rose 61% in 2022, New Study Finds – Global Newswire
Phishing Trends in 2022 So Far, And What You Can Learn From Them – Phish Protection
Phishing reaches all-time high in early 2022 – Help Net Security
Q1 Data Breach Analysis – Identity Theft Resource Center
Spam and phishing in Q1 2021 – Securelist
Spectrum Health Warns of “Vishing” Scam – Spectrum Health
Top cybersecurity statistics, trends, and facts – CSO Online
Understanding the state of millennial personal finances – TIAA Institute
UK Consumer Digital Index 2021 – Lloyds Bank
US Consumer Security, Privacy & VPN Usage – CouponFollow
Why a Phishing Attack Is Still Profitable — And How To Stop One – Security Intelligence



