Data Breach: Thousands Exposed as Dating App Leaks Private Data
WizCase has recently found an open Elasticsearch database on the Turkish based online dating app, Heyyo. The leak contained private information, including messages, photos, sexual preferences, occupation, and more for over 70,000 registered users worldwide. It was closed on September 25th, after Turkey’s CERT (Computer Emergency Response Team) was alerted.
What’s Going On?
Avishai Efrat, Wizcase leading hacktivist, discovered a severe data leak on Heyyo, a relatively new mobile dating app. Our team was able to access a database of over 70,000 users from around the world through an unsecured Elasticsearch engine. The majority of affected users are based in Turkey, but there’s also a significant number from the US and Brazil, which is over ⅕ of their user base.
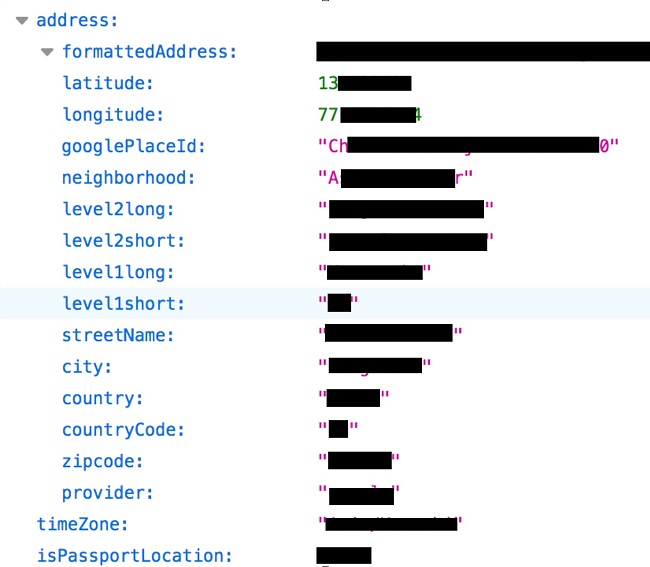
The leaked data included personal information and user activity. Here’s a full list below:
- User names (mainly first names)
- Email address
- Country
- GPS location (latitude and longitude)
- Type of mobile device the app was downloaded on
- Gender
- Date of birth
- Dating history (likes, dislikes, super likes, message count, blocks)
- Sexual preferences (based on user searches)
- Links to social media profiles (Facebook, Instagram)
- Profile pictures
- Phone number
- Occupation (when entered by the user)
Whose Data is Available and What are the Consequences of such a leak?
We found an unsecured database which contained over 600MB of data and approximately 77,000 total records. The number of users has increased by 7.7% while we’ve been working on this research . We found records from users from many different countries.
Below is a list of the main affected countries from most users to the least.
- Turkey
- Brazil
- USA
- Africa
- Germany
- Portugal
- Spain
For Heyyo users, public access to this data is a massive breach of their privacy.
A scammer who accesses the database will be able to find the answers to the following questions about a user.
- Which type of partner you’re seeking? (age, location, gender)
- How do you describe yourself and the relationships you’re seeking?
- Who you are (name, email, etc) and what do you look like?
- What’s your location?
- What’s your address?
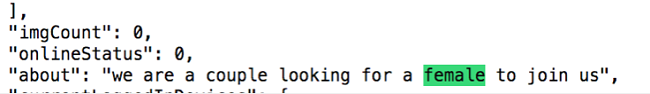
Not only is the user’s personal information compromised, but their user activity is also widely available. The data shows a users likes, profiles they’ve blocks, message counts, kinks, and which profiles they have viewed.
On top of this privacy breach, users now face several other security threats that leave them vulnerable to a multitude of scams.
These threats include:
- Identity Theft: Scammers can use people’s full names, email addresses, physical addresses, phone numbers, and pictures to steal their identity.
- Catfishing: Having access to user data would make it easier for a scammer to trick someone into revealing private information using an existing user’s profile.
- Blackmail: People could have their personal information used against them in a variety of blackmail schemes, especially individuals with an undisclosed sexual orientation, cheating spouses, or couples looking for a third partner.
- Sexual Discrimination: Dating profiles are filled with private information, including images and sexual orientation. This could easily lead to targeting of LGBT users, especially in a country like Turkey, which still allows for discriminating against members of the LGBT community.
- Sexual Harassment: The user data that the scammer or hacker can collect includes pictures, email addresses, phone numbers, and even a physical address.
- Phishing: With the available data, a scammer can gain the trust of the user and try and get additional valuable information from them.
How Did This Happen and What to Do Now?
Heyyo used an Elasticsearch engine, which is installed on a Digital Ocean cloud hosted server. The Elasticsearch default setting requires no authentication or password to gain entry.
Servers should never be exposed like this to the open world. Password authentication, IP whitelisting, and additional monitoring would have greatly reduced the chances of such a data breach.
Unfortunately, companies using default or misconfigured security settings for their databases (which often includes sensitive data) is an all too common scenario these days.
If you have an active profile on Heyyo, you should be careful with the personal data that you add to your profile.
You should also stay alert and report any suspicious online activity. Potential scammers could have used your personal details, or anyone else’s from the database, that was exposed in the breach.
In general, when talking with people on dating apps one should always be careful with what information and picture you share. Once you send text messages or pictures, it can be used for blackmail, catfishing, or other fraudulent crimes.
Who is WizCase?
WizCase is a leading source for cybersecurity news. Our team of web security experts have uncovered several glaring leaks, including one in the hospitality industry and another that exposed vulnerabilities in the world’s most popular webcams.
We always inform the companies of the leaks before publishing the information, so they have an opportunity to fix their issues and secure their user’s data.



