How to Access the Dark Web Safely: A 2024 Beginner’s Guide
Accessing the Dark Web isn’t 100% safe, even if you use Tor. Your ISP can still see your activity and may report it. It’s monitored because the Dark Web is linked to illegal activities like drug trafficking, weapons sales, and data breaches. Plus, it’s a favorite haunt for cybercriminals who want to steal sensitive data and jeopardize your device’s security.
A VPN helps to protect you on the Dark Web. I tested 20+ VPNs that work with Tor to find 3 with the best security features to protect your online privacy, whether you’re on the Dark Web or not.
I suggest you get ExpressVPN for fast and safe browsing on the Dark Web. It has RAM-based servers, 256-bit encryption, a verified no-logs policy, leak protection, and more to keep your Dark Web activity private. There is a 30-day money-back guarantee, so you can get a full refund if you don’t like it. I tested this policy and got my refund in 4 days.
Safely access the Dark Web with ExpressVPN
Quick Guide: How to Access the Dark Web Safely in 3 Easy Steps
- Get a VPN. Due to its superfast speeds and top-class security features, I recommend ExpressVPN for the Dark Web.
- Get Tor. Visit the Tor download page and select your device. You’ll have the option to configure it or connect immediately.
- Explore the Dark Web! First, connect to your VPN and then open Tor to ensure maximum security on the Dark Web.
What Is the Dark Web?
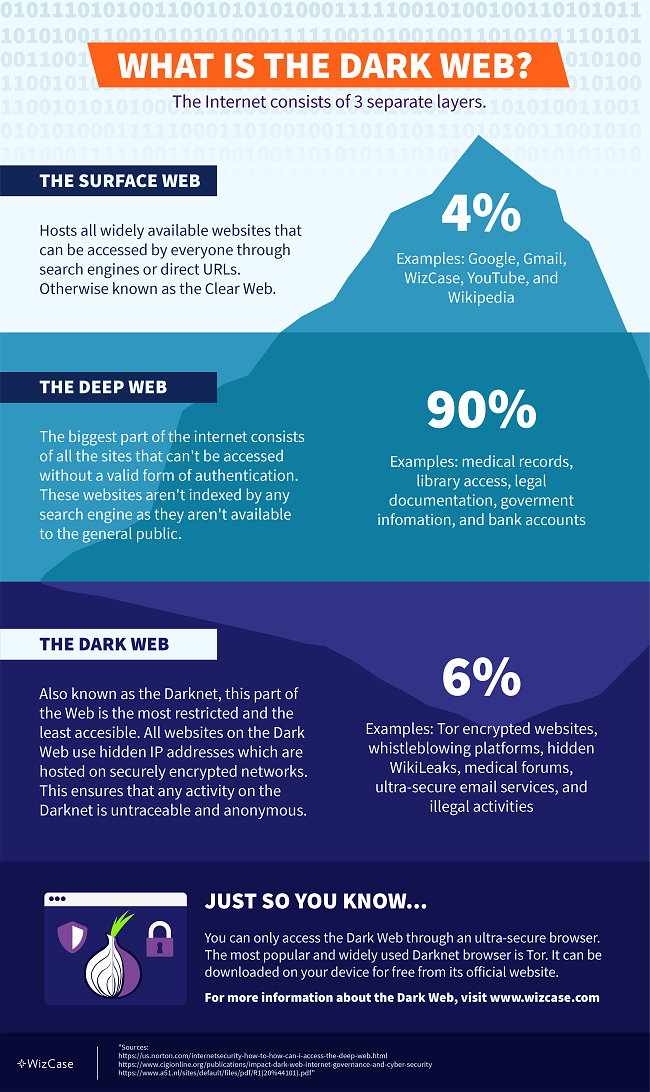
The internet consists of 3 layers: the Surface Web (or the Clear Web), the Deep Web, and the Dark Web, otherwise known as the Darknet.
The Surface Web
The Surface Web, or Clear Web, is part of the internet that we use every day. It includes news websites, social media, online shops like Amazon, and more sites that we can browse directly. When you enter these sites without logging in, you are on the Surface Web. But when you log in to access more information, you enter the Deep Web.
The Deep Web
The Deep Web is much larger than the Surface Web and includes websites that are not open to the public. You need a special link or password to access these sites— search engines like Google can’t find them.
The Deep Web stores private content, such as emails, subscription services, and company websites with medical information and other sensitive data.
The Dark Web
The Dark Web is a part of the Deep Web that isn’t easily accessible. You won’t be able to browse it just by logging in since these websites use hidden IP addresses hosted on encrypted networks. That’s why any online activity on the Dark Web is fully anonymous and untraceable.
To reach any Darknet website, you require an extremely secure browser like Tor. It functions similarly to conventional web browsers like Chrome or Firefox, with a notable distinction: it channels data through a series of connections to ensure its security. This approach leads to a reduction in internet speed, but significantly enhances security.
All websites on the Dark Web come with randomly created URLs that change frequently. The most recognizable feature of Tor links is their suffix: instead of the well-known .com or .net, all Darknet websites end in .onion. The URLs consist of up to 56 letters and numbers to keep all the content on the Dark Web confidential and anonymous.
Tor and other Dark Web browsers offer some protection, but they are not completely safe. Your ISP can still see when you browse the Dark Web through these. A VPN can mask your real IP and keep your identity and activity safe on the Dark Web.
Note: The Dark Web has both legal and illegal websites, and it is unregulated. While some uses are legitimate, it can also host illegal activities. Always be cautious and follow the law when using any part of the internet.
Is the Dark Web Illegal?
While it is legal to access the Dark Web in most countries, people use it for various illegal purposes like hacking, selling and buying drugs, and child pornography. Governments and special services all over the world work extremely hard to locate and punish anyone involved in such activities, but it often takes months or years to catch cybercriminals.
Some of the most popular crime stories from the Dark Web include:
- Silk Road — Silk Road was the first digital black market platform selling illegal goods and services including guns, forged paperwork, and drugs. The website enabled users to make purchases using Bitcoin to protect their online identities. Silk Road’s founder, Ross Ulbricht, was arrested in 2013 after the FBI discovered he had used his real name and email to set up the website. He was sentenced to life in prison after detectives seized $48 million earned in commissions.
- Hieu Minh Ngo — This hacker stole the bank details, names, and Social Security numbers of over 200 million US citizens. He then sold the information on the Dark Web. Minh Ngo earned up to $2 million through online transactions before he was arrested and sentenced to 13 years in federal prison.
- Shannon Grant McCoole — McCoole was a care worker for the Department for Child Protection in Australia when he launched a child pornography website. He uploaded explicit interactions with children as young as 18 months old. Almost 1,000 regular users tuned in to watch McCoole’s abuse until he was thankfully arrested in 2014. The police discovered over 100,000 images and 600 videos of exploitation on his personal computer, and he was sentenced to 35 years in prison.
- Ashley Madison — Ashley Madison is a popular dating site for extramarital affairs. Although the platform is available on the Clear Web, it fell victim to a Dark Web hacker attack in 2015. The so-called “Impact Team” successfully stole over 60GB of user data and threatened to publish it on the Dark Web if Ashley Madison wasn’t shut down within a month. The site ignored their demands, so the hackers published personal information, including user emails and home addresses. Unlike the other cases on this list, the hackers’ identities remain unknown.
Though extremely unsettling, these are only a few out of hundreds of illegal activities taking place on the Dark Web every day. However, the Dark Web isn’t all bad and you can use it to engage in many useful and legal digital practices.
What You Can Use the Dark Web For

Despite the Dark Web’s bad reputation, it provides a way for many people to bypass local digital restrictions and access content unavailable in certain countries. Users also view the Dark Web as a platform to exercise their right to freedom of speech and privacy. Though not exhaustive, these are the most popular positive uses of the Dark Web:
1. Stay Anonymous Online
The Dark Web has many social media platforms, gaming websites, and ultra-secure email services. Plus, your online activity is anonymous and can’t easily be traced by hackers and government authorities. It also allows you to bypass censorship and access websites otherwise restricted in many Middle Eastern and Asian countries.
Warning! Don’t log into personal accounts (e.g., online banking or email) on the Dark Web. Your activity becomes linked to your profile, even if you use Tor. Instead, use a dummy email address.
2. Exposing Corruption
Multiple online magazines and news channels like CNN, FOX, and NBC have open sites on the Dark Web to receive anonymous tips from online users.
Journalists and whistleblowers regularly turn to the dark net to share controversial information about government representatives, celebrities, or money scandals, like tax evasion. This ensures that activists exposing illegal practices can avoid prosecution.
3. Sharing Personal Stories
Due to the anonymity it provides, many people use the Dark Web to share their personal stories. This ranges from websites with advice on a variety of topics to online support forums where people discuss traumatic experiences like physical or sexual abuse. It’s a way to connect with other victims and seek help without revealing your identity.
4. Buying Things Anonymously
While I don’t condone purchasing any illegal items, there are many legitimate reasons to buy products and services on the Dark Web. This includes buying specific security software, discounted electronic devices, or medication like sleeping pills, painkillers, and antidepressants.
Warning! Be careful when buying on the Dark Web. Due to the lack of regulations and the fact that many illegal and stolen items are sold daily on the digital market, you can never be sure what you’re getting. Before making any transactions, check buyer reviews and seller ratings. Also, remember to only use cryptocurrencies as a payment method.
5. Getting Medical Advice
Some doctors who offer advice to patients on the Dark Web. Practitioners can be found on various medical forums as well as their own websites. This is a great way to get assistance and advice for those who want to keep their conditions private.
The most popular “Drug Counselor,” who goes by the nickname DoctorX, has answered hundreds of questions regarding drug addiction, self-harm, and more.
6. Joining Online Communities
By browsing Tor, you can find similar sites and online communities that you’d find on the Clear Web, including clubs and social networks.
Always avoid engaging in any forums involving illegal activities (like sharing copyrighted material), as you could face prosecution.
7. Research
The Dark Web can be a valuable resource for academic research and data gathering, providing access to information that may be difficult to find on the Surface Web. This includes unpublished works, controversial articles, and unique primary sources across a range of topics.
Researchers can also use the anonymous communication features on the Dark Web to interact with experts, insiders, and fellow researchers while protecting their privacy. However, it is essential to verify sources, cross-check data, and avoid accessing or engaging in illegal content to avoid serious legal repercussions.
The Risks & Dangers of the Dark Web
The Dark Web offers many amazing benefits to those who use it for legitimate purposes. Unfortunately, it’s also a place where many cybercriminals abuse the privilege of anonymity to avoid getting caught. While you can choose not to partake in any criminal activity, it’s important to be aware of the dangers of accessing the Darknet:
Malware
Hackers create fraudulent Dark Web sites containing malware that can infect your computer. These malicious programs can record keystrokes, steal documents and financial data, record audio and video from your computer, or even hijack your personal device for blackmail.
As it’s often difficult to tell whether sites on the Dark Web are legitimate, it’s easy to download malware without knowing. To stay safe, use the Darknet with a specific aim in mind and do research beforehand to get a list of trustworthy links.
Criminal Activity
The Dark Web is used by criminals to sell stolen goods, weapons, drugs, and fake documents (i.e., passports). Criminals also use the Dark Web to hire hackers and assassins. Some sites have disturbing and illegal content like child pornography or live-streamed murders.
I strongly advise against browsing random sites to avoid accessing unsettling content.
Surveillance
Law enforcement agencies and governments monitor the Dark Web to catch criminals. As it’s incredibly difficult to identify users on the Darknet, governments usually set up fake illegal websites to catch cybercriminals. In some countries, you can attract the attention of the authorities simply by using a browser like Tor.
Fraudulent Sites
Fraudulent sites may impersonate popular online marketplaces, financial services, or charitable organizations to deceive users into providing sensitive information. This can include login credentials, credit card numbers, and personal details.
Always verify the authenticity of a site before providing any personal information or making transactions.
Step-by-Step Guide: Access the Dark Web Safely on Any Device
Download and Connect to a VPN
- Get a VPN with strong encryption, a strict no-logs policy, and leak protection. ExpressVPN is compatible with Tor. Plus, it’s highly secure and fast.
- Create an account using your email address and choose a subscription plan.
- Connect to a server. You can choose any server based on the content you want to access and its availability.
Download and Install Tor
Download Tor from its website at torproject.org, as it’s the only official website. Avoid fraudulent Tor-like browsers that compromise your online security. The browser is free to download and works on multiple operating systems.
Instructions vary depending on your operating system:
- Go to the Tor Project Website. Click Download for Windows.
![Screenshot of Tor Projecy's official website showing download option selected for Windows]()
- Open the folder where you downloaded the browser and double-click the installer.
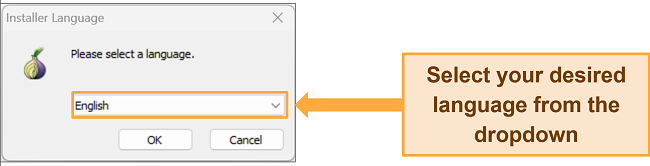
![Screenshot of language options while installing Tor on Windows]()
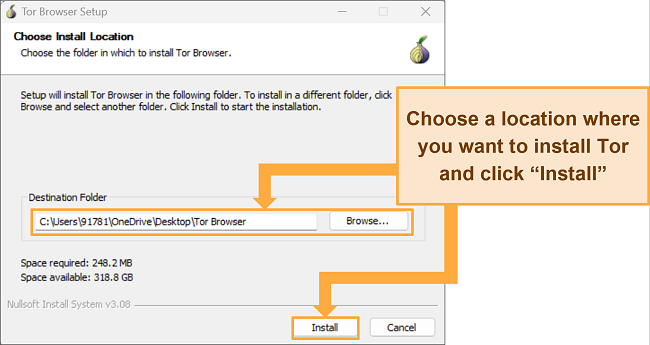
- Choose a location to install Tor. You can install it on a USB drive so data isn’t saved to your computer. When you’re ready, click “Install.”
![Screenshot of choosing Tor installation location on Windows PC]()
- When the installation is complete, press “Finish.”
- You can now launch Tor using the main menu or the shortcut on your desktop.
Mac
- Go to the Tor Project Website. Click “Download for macOS” to download the Tor browser.
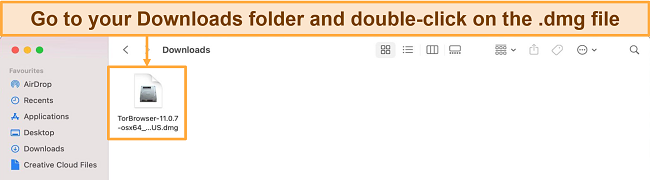
- Go to your downloads and double-click the .dmg file.
![Screenshot of Tor's .dmg file in downloads on macOS]()
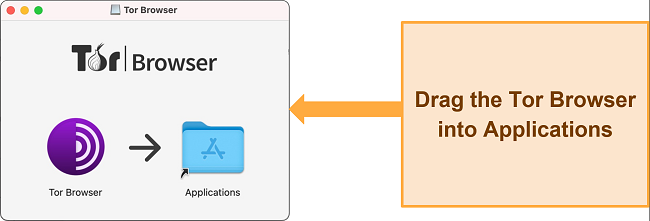
- You’ll see a screen with a Tor icon and the Applications folder. Drag the icon into the Applications folder to install Tor.
![Screenshot of Tor Browser being dragged into Applications]()
- You can now launch Tor using the Launchpad or the shortcut on your toolbar.
![Screenshot of searching Tor on the toolbar before launching]()
- Before you can use Tor, you’ll be prompted to click Connect or Configure your connection depending on your location.
Linux
- Download Tor for Linux from the Tor Project website.
- Right-click on the file and choose “Extract here.” A new folder will be created with the extracted contents.
- Open the new folder. There will be another folder inside you need to access called “Browser”.
- Double-click the Tor icon to launch the browser. You might have to confirm that you trust the downloaded application in order to open it.
Android
- Visit the Tor Project website on your Android.
- Tap “Go to Google Play.”
- Tap “Install”.
- Tap “Connect”.
- Verify connection at check.torproject.org.
iPhone
Tor developers created a reliable and secure app to allow iPhone users to access The Onion Browser, which you can get by following the steps below:
- Open the App Store on your iPhone.
- Search for “Onion Browser.”
- Tap “Get and Install.”
- Launch Onion Browser.
- Tap “Connect.”
Set Up the Tor Browser
When you launch Tor for the first time, you’ll be prompted to configure a few settings. If your connection is censored (i.e. you’re using a work computer or Tor is blocked in your country), choose “Configure.” Otherwise, you can click “Connect” to go directly to Tor’s home page.
I recommend enabling all available add-ons to maximize security. By default, the main add-ons, HTTPS Everywhere, and NoScript are already enabled. Go to the menu in the top right-hand corner and select “Add-ons” for further optimization. HTTPS Everywhere ensures that you always use the HTTPS version. NoScript disables JavaScript on untrusted sites.
Check your security settings by clicking the shield icon on your browser toolbar. There are three levels: Standard, Safer, and Safest. Standard is the default setting and provides secure browsing. While Safer and Safest disable scripts and other content to increase security, both can stop websites from working properly.
Safely Browse the Dark Web With Tor
Now, you can start browsing anonymously. Consider using Dark Web search engines like DuckDuckGo (http://bznjtqphs2lp4xdd.onion/) and Candle (http://gjobqjj7wyczbqie.onion/) to find the sites you’re looking for. If you already know what websites you want to access, simply insert the link in Tor’s webpage bar.
Important! Don’t change the Tor browser screen at any point when you’re using it. Even if you manually resize the browser window, you’re still leaving your digital footprint, which can be used by the authorities or hackers to gather your personal information.
Additional Tips for Safe Browsing on the Dark Web
1. Don’t Reveal Your Real Identity
Here are some measures to take to prevent revealing your true identity:
- Create a dummy email or use an encrypted email service like ProtonMail for any Dark Web communication.
- Turn off your device’s location services to prevent inadvertent disclosure of your whereabouts.
- Cover your camera and microphone to protect against potential unauthorized access and surveillance.
- Opt for cryptocurrency payments; they’re anonymous and make it difficult to trace transactions back to you.
- Be cautious when interacting with other users, as social engineering techniques can be used to extract information about your identity.
- Avoid sharing any personal details, such as your name, age, address, or workplace, in online discussions or private messages.
- Use unique usernames and strong, distinct passwords for each Dark Web site or service you access to prevent cross-referencing and profiling.
2. Use a Different Operating System
Use a privacy-focused operating system like Tails, or a Linux distribution like Whonix. Tails is a security-focused operating system that runs directly from a USB stick or DVD, leaving no trace on the host computer. It comes with pre-installed privacy and security tools, including the Tor Browser, to ensure your online activities remain private.
Whonix or Qubes OS are also solid options. These are Linux-based open-source operating systems that prioritize security and can be configured to work seamlessly with the Tor network. They offer greater control over your privacy settings and often have a more extensive range of security features than mainstream operating systems.
3. Update Your Device and Browser
Keeping your device and browser updated is essential for ensuring security and privacy while browsing the Dark Web. Updates address security vulnerabilities, protecting you from threats like hackers, malware, and data breaches.
4. Disable Javascript
JavaScript is a common scripting language used to create interactive elements on websites. However, it can also be exploited by attackers to reveal your true IP address, bypass VPN and Tor protections, and execute malicious code on your device.
Disabling JavaScript in the Tor Browser minimizes the risks of being de-anonymized. This stops you from falling victim to browser fingerprinting and inadvertently downloading malware. While some websites may lose functionality, taking this precautionary measure significantly improves your security and ensures a more private browsing experience on the Dark Web.
5. Use an Antivirus
Malicious websites on the Darknet can expose you to cyber threats, including malware, ransomware, DDoS attacks, and other harmful programs.
Using an antivirus with real-time protection defends your device against various threats, including viruses, Trojans, and phishing attacks.
6. Open Downloads Offline
By disconnecting from the internet before opening downloaded files, you minimize the risk of malware “phoning home” to the attacker’s server, which could lead to data exfiltration or remote control of your device. This also prevents any potential tracking or tracing back to your online identity.
7. Only Visit Trusted Sites
Visiting unknown sites may pose significant security and privacy risks, such as:
- Exposure to phishing scams that aim to steal sensitive information.
- Downloading malware or ransomware that can compromise your device and data.
- Encountering illegal content that could lead to legal consequences.
- Visiting fraudulent marketplaces or services, which could result in financial loss.
Stick to trusted and well-known websites to minimize the risk of encountering malware, scams, or illegal content. Use reputable directories, search engines, or references from trusted sources to find websites on the Dark Web.
The Best VPNs for Accessing the Dark Web Safely (Tested 2024)
1. ExpressVPN — TrustedServer Technology Ensures None of Your Data Is Stored
Key Features:
- 3,000+ servers in 105 countries to access the Dark Web safely from anywhere
- TrustedServer network uses RAM-based servers which are regularly wiped clean
- Allows 8 simultaneous device connections to access Tor
- Keeps your Tor browsing secure with military-grade AES-256 encryption and advanced leak protection
- Audited no-logs policy ensures none of your private information is being stored
- 30-day money-back guarantee
ExpressVPN uses TrustedServer technology across its network, meaning all servers are RAM-based and wiped at regular reboots. This reduces the risk of your sensitive data falling into the wrong hands when you access the Dark Web. Although its servers use the highest security, ExpressVPN doesn’t compromise your speed.
I checked ExpressVPN’s Network Lock feature by running multiple tests. It effectively prevented my online activity from being exposed to my ISP, even while switching servers. My actual IP address and DNS data were never leaked during these tests.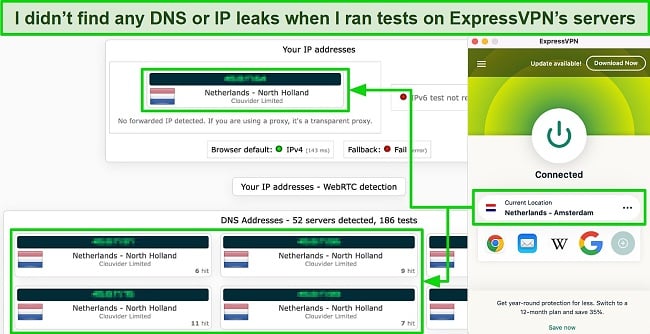
Privacy is essential when you access The Dark Web, and ExpressVPN is based in The British Virgin Islands, which isn’t subject to data retention laws. This, coupled with ExpressVPN’s no-log policy, means that even if a court of law asked for data, there would be none to give. The policy was audited by KPMG and Cure 53 for extra validation.
You need the best security available to combat threats when you use Tor, and ExpressVPN has a range of top-tier features, including:
- “Network Lock” kill switch automatically disconnects your device from the internet if the VPN connection drops, preventing data leaks.
- AES-256 military-grade encryption ensures your data remains secure and unreadable by potential attackers.
- Perfect forward secrecy (PFS) regularly changes encryption keys, protecting encrypted messages from future hacking.
- Obfuscated servers help bypass VPN blocking and censorship by disguising VPN traffic as regular internet traffic.
- DNS/IPv6 leak protection protects your real IP address from being accidentally exposed.
When I looked at how fast the servers are, I found that ExpressVPN’s speeds consistently outperformed other VPNs, making it the best option for accessing the Dark Web. This is crucial as Tor connections are generally slower than standard browsers. My download speeds averaged around 94 Mbps, which is only 6% slower than my baseline speeds.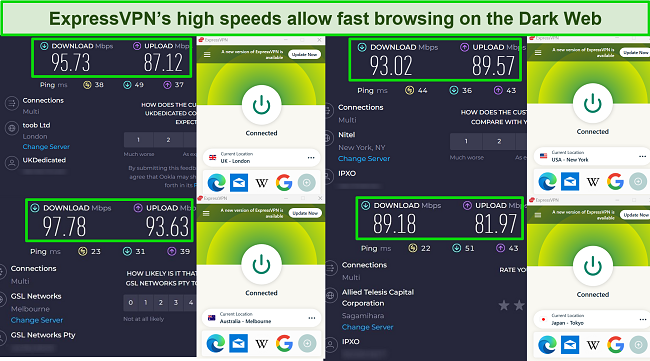
Although ExpressVPN is a bit more expensive than other VPNs listed here, it offers great deals throughout the year. You can save 49% on its 1-year + 3 months plan and get it for just $6.67/month. I recommend making payments via cryptocurrency to stay completely anonymous.
You can get ExpressVPN at zero risk to browse the Dark Web. All its plans come with a reliable 30 money-back guarantee, so if you’re not 100% happy, you can get a full refund. I verified its refund policy through 24/7 live chat. The agent quickly accepted my request without asking any questions, and I got all my money back in just 3 days.
ExpressVPN works with: Windows, macOS, Linux, Chromebook, Android, iOS, and more.
2024 Update! ExpressVPN has dropped prices for a limited time to a crazy $6.67 per month for the 1-year plan + 3 months free (you can save up to 49%)! This is a limited offer so be sure to grab it now before it's gone. See more information on this offer here.
2. CyberGhost — NoSpy Servers Ensure Maximum Security While Browsing the Dark Web
Key Features:
- 11,676+ servers in 100 countries to browse the Dark Web from all over the world
- NoSpy servers offer added protection as no third party can access them
- Content blocker, military-grade encryption, a verified no-logs policy, and an automatic kill switch to boost your safety on the Dark Web
- Secure 7 devices simultaneously for accessing the Dark Web
- Generous 45-day money-back guarantee
CyberGhost’s NoSpy servers ensure maximum privacy and security while browsing the Dark Web. These servers are exclusively managed by the CyberGhost team in Romania, a country not bound by data retention laws and outside the 5/9/14 Eyes alliances. This setup makes it virtually impossible for third parties to access your data.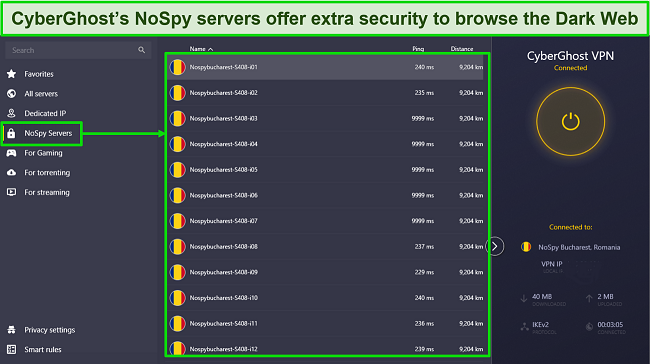
In addition, CyberGhost has plenty of other security features to keep you safe and anonymous on the Dark Web. These include:
- Zero-logs policy, independently verified by Deloitte, ensures no records of your online activities or personal data are kept.
- A kill switch automatically halts your internet if the VPN connection drops to protect your private information from leaking on the Dark Web.
- Split tunneling (available on Windows and Android) allows you to selectively unencrypt certain apps for a faster VPN connection speed to access the Dark Web.
- Built-in adblocker prevents intrusive ads and potentially harmful trackers planted on various Dark Web platforms from reaching your device.
- ID Guard helps generate secure passwords and sends alerts if your personal information has been leaked in Dark Web breaches.
- Perfect forward secrecy (PFS) changes the encryption used so that in the unlikely event a hacker cracked the code, it would soon update and be unreadable again.
- Military-grade encryption scrambles your internet traffic, so your online activity is hidden from your ISP, hackers, and government agencies.
I got speeds of around 78 Mbps with CyberGhost, which is 22% slower than my base connection. Although I had a great result on local servers, my browsing experience with CyberGhost wasn’t as fast as with ExpressVPN. Since Tor is naturally slower than regular browsers, I faced some minor interruptions and slowdowns while browsing the Dark Web.
One downside is that CyberGhost doesn’t work in China and other countries with restrictive internet. So, if you’re planning to access the Dark Web from these countries, you should go for ExpressVPN.
While CyberGhost’s short-term plans are a little expensive, its 2-year + 2 months plan provides the best value. With this plan, you can get CyberGhost for the Dark Web at a 83% discount. It will cost you only $2.19/month.
CyberGhost’s 6-month and 2-year + 2 months plans are backed by a generous 45-day money-back guarantee. When I contacted customer support for a refund, the agent inquired about my reason for cancellation. My request was approved when I explained the reason. The fee was back in my account 4 days later.
CyberGhost works with: Windows, macOS, Linux, Chromebook, Android, iOS, and more.
3. Private Internet Access (PIA) — MACE Feature to Protect You From Malicious Content on The Dark Web
Key Features:
- 35,000+ servers in 91 countries
- Built-in ad, tracker, and malware feature (MACE) protects you from potential online threats
- Access the Dark Web from unlimited devices simultaneously
- Military-grade encryption and no-logs policy keep your Dark Web activity private
- 30-day money-back guarantee
PIA’s MACE feature offers exceptional protection for Dark Web users by effectively blocking ads, trackers, and malware. When I tried it, I barely encountered any ads or malicious content, which made my browsing experience smoother and safer. Also, MACE was more effective than CyberGhost’s ad blocker at preventing ads.
There are multiple security features included with every PIA server to ensure safe and secure access to the Dark Web, including:
- A multi-hop feature, which you can enable to route your traffic through 2 VPN servers for added safety.
- AES-256-bit encryption hides your activity from third parties.
- A no-logs policy (audited by Deloitte) ensures that no logs of your activity are kept.
- A kill switch shuts down your internet if the VPN connection drops accidentally.
- Perfect forward secrecy (PFS) updates the encryption keys regularly, stopping future hacking of your personal data.
- IP/DNS/WebRTC leak protection so your true identity remains hidden.
I performed some IP/DNS leak tests on various PIA servers and it didn’t reveal my actual location. This ensures that your Dark Web activity will remain anonymous and can’t be linked to your true identity.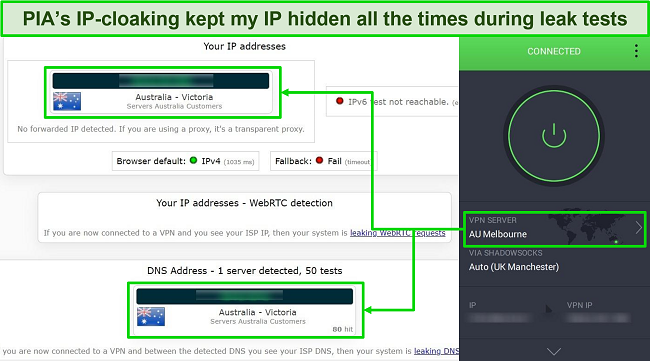
Although PIA’s speeds were excellent on nearby servers, they significantly declined with distant ones. I could browse the Dark Web without interruptions while connected to a US server (near my location). But when I switched to a farther server in Australia, the browsing became significantly slower, and large downloads took way too much time.
You can safely browse the Dark Web on all your devices as PIA offers unlimited simultaneous device connections with a single subscription. This means I can set PIA up on all my devices so I never forget to protect my connection when I log into the Dark Web.
Since PIA is based in the US, it might raise privacy concerns, especially for someone who wants to access the Dark Web. But I wouldn’t worry much because PIA’s verified no-logs policy ensures that it maintains user privacy by not storing any personal data.
Staring at just $2.19/month with its 3-year + 2 months plan, PIA is one of the best monthly VPNs.
You can also use its 30-day money-back guarantee to try PIA completely free. If you’re not satisfied, you can get a full refund. After 2 weeks of testing, I canceled my subscription by talking to an agent over live chat. I received the money back in my account in 5 days.
PIA works with: Windows, macOS, Linux, Android, iOS, and more.
Why You Need a VPN to Be Safe on the Dark Web
While onion routing makes it more difficult for third parties to trace your data back to you, it’s still possible to identify you through the Dark Web browser. Without a VPN, your IP address is exposed to anyone who wants to find it. There are also risks of data breaches if the security of the Tor website you are using is compromised.
For example, in 2014, the FBI caught users involved in illegal activity on the Dark Web because of a security issue with JavaScript. In 2017, the Darknet’s system failure resulted in multiple websites crashing and exposing the IP addresses of many of its users. Though Tor developers tend to fix issues quickly, they can’t always keep up with them.
A VPN encrypts your data before it reaches your ISP. It also hides your IP address by relocating your virtual location. That way, your ISP won’t know you’re browsing on Tor, and your activity will remain private.
VPN Over Tor or Tor Over VPN: Which Is Better?
While using Tor alone provides a certain level of anonymity, it may not be enough to protect you from surveillance, traffic analysis, or malicious exit nodes. To enhance security, you can opt for either a VPN over Tor or Tor over VPN setup.
VPN Over Tor
When you use VPN over Tor, your internet traffic first goes through the Tor network, which hides your identity by bouncing your connection through several different computers around the world. After that, your traffic goes through a VPN, which adds another layer of protection by encrypting your data and hiding your location.
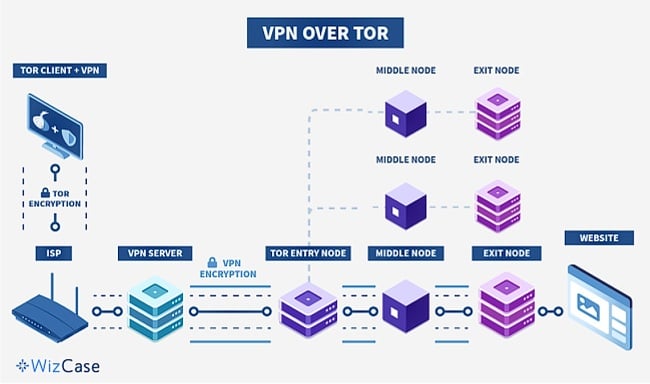
This configuration offers several advantages, including:
- Enhanced privacy through the combination of Tor’s multi-hop routing and VPN encryption.
- The ability to bypass ISP blocks on Tor, enabling access to otherwise restricted websites.
- Protection against malicious exit nodes, as the VPN server, obscures the final destination of your traffic.
One disadvantage of VPN over Tor is that you might get slower connection speeds due to the combined overhead of the Tor network and VPN encryption.
Tor Over VPN
In the Tor over VPN setup, you first connect to a VPN and then use the Tor network. This means your ISP can see that you’re using a VPN, but they won’t know you’re using Tor. It’s easy to set up because many VPN providers have built-in support for Tor over VPN.
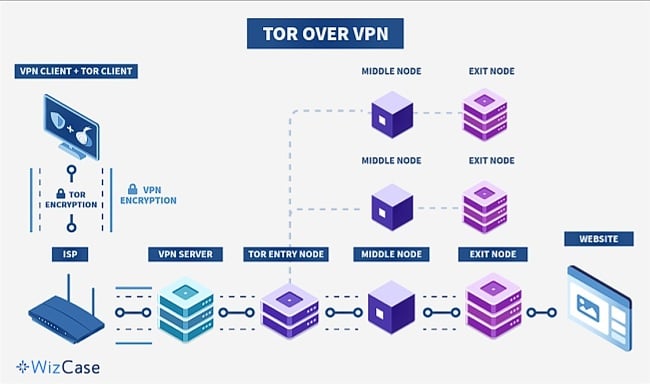
One issue with this method is that you may be vulnerable to malicious exit nodes since your traffic exits the Tor network before being encrypted by the VPN.
Using Tor over VPN is the most secure choice for accessing the Dark Web because it hides your activity and identity from your ISP and other third parties (e.g. government authorities) who might be able to detect your Tor usage.
No matter which setup you choose, be sure to use a top VPN with a strict no-logs policy to maintain your privacy and resist potential government pressure to disclose user data.
Alternatives to the Tor Browser
While Tor is the best option for browsing the Dark Web, there are alternative networks that offer different levels of accessibility and security. It’s crucial to remember that browsing the Dark Web always involves risks, so using a VPN for added security is advisable.
I2P
I2P (Invisible Internet Project) is a separate network from Tor that allows access to its unique sites called “eepsites.” I2P doesn’t provide access to as many sites as Tor and can be more challenging to configure. After downloading and installing I2P, you’ll need to manually configure it through the router, individual applications, or browser proxy settings.
Using I2P is faster and provides better peer-to-peer security than Tor. It uses one-way tunnels to encrypt traffic, which means only inbound or outbound traffic can be intercepted, not both. In addition, I2P employs a distributed network database, making it more resistant to attacks than Tor’s fixed, trusted Directory servers.
Freenet
Freenet only gives access to content uploaded to the Freenet network, not to .onion links. It’s an anonymous platform for peer-to-peer content sharing, offering “darknet mode” for private group sharing and “opennet mode” for random peer connections. Like I2P, Freenet relies on a distributed network database for added protection against cyberattacks.
Setting up Freenet is straightforward; simply download and install the software. Freenet runs automatically in your web browser when opened, so I recommend using a different browser than your regular one to maintain privacy.
FAQs on Accessing the Dark Web Safely
Can I access the Dark Web without Tor?
Yes, you can access the Dark Web without Tor, but I don’t recommend it. There are alternative networks, such as I2P and Freenet, but they have some limitations and might not provide the same level of anonymity and security as Tor. They can leave you vulnerable to security threats and potential exposure of your personal information.
Tor is specifically designed to access the Dark Web and provide a high level of anonymity. It routes your traffic through multiple layers of encryption and across a series of volunteer-operated servers, making it extremely difficult for anyone to trace your online activities.
How can I find websites on the Dark Web?
You can use Dark Web search engines, directories, and forums to find websites on the Dark Web. Don’t forget to use a VPN while browsing the Dark Web even if it seems safe.
Here are some useful websites on the Dark Web:
- Daniel: A Dark Web search engine that indexes hidden services.
- ProPublica: A reputable, independent news organization that publishes investigative journalism and provides a .onion version of its site for privacy-conscious users.
- SecureDrop: A secure platform for whistleblowers to share documents and information with various media organizations without revealing their identity.
- DuckDuckGo: A popular privacy-focused search engine that doesn’t track your search history or data.
- The Hidden Wiki: A directory of .onion links that provides an overview of the websites on the Dark Web, including some safe and legal ones.
- Mail2Tor: A free, anonymous email service that allows you to send and receive emails without revealing your identity or location.
- Hidden Answers: A Dark Web alternative to websites like Quora and Yahoo Answers, where users can ask and answer questions anonymously on a wide range of topics.
- The Imperial Library: A digital library that offers a vast collection of books, articles, and documents. The site is dedicated to preserving and sharing knowledge, and it allows users to access its content anonymously.
Note: While these websites are considered safe, it’s crucial to exercise caution and use a combination of Tor and a reliable VPN when browsing the Dark Web to ensure your privacy and security.
Is there a Dark Web search engine?
Yes, there are many Dark Web search engines, but they don’t work as well as popular search engines like Google. Be careful and use a VPN on the Dark Web, as some sites found through these search engines might be dangerous or made by hackers to steal your data. Always research before visiting any sites and use a reliable VPN to protect your privacy.
In addition, Dark Web search engines are not as accurate as you might think. They have trouble keeping up with the always-changing Dark Web, so they often give unhelpful or repeated results.
I looked up some Dark Web search engines and found these 3 workings efficiently:
- DuckDuckGo: Maintains your privacy and doesn’t track you.
- SearX: Combines results from different sources to give you reliable results.
- Daniel: Helps you find trusted .onion websites.
Is it legal to access the Dark Web?
Yes, it is legal to access the Dark Web in most countries, as long as you don’t commit any unlawful acts. Still, I recommend you use a VPN to maintain anonymity on the Dark Web.
Here are some legitimate reasons to access the Dark Web:
- Secure communication: Encrypted messaging platforms provide a safe way to communicate without fear of surveillance.
- Privacy protection: Users can access information and services while maintaining their anonymity.
- Bypassing censorship: The Dark Web allows users in countries with strict internet censorship to access blocked content.
- Whistleblowing: Protected platforms like SecureDrop enable whistleblowers to anonymously share sensitive information with journalists.
- Research purposes: Academics and researchers may use the Dark Web to study internet privacy and security.
Can I access the Dark Web with a VPN?
Yes, you can access the Dark Web with a VPN, but you still need to use the Tor browser. A VPN helps to enhance your security and privacy while you’re on the Dark Web. When you use a VPN with Tor, it hides your real IP address and encrypts your internet traffic, making it harder for your ISP, hackers, or government agencies to track your activities.
The best way to use a VPN with Tor is the “Tor over VPN” method. In this setup, you first connect to a VPN server, and then launch the Tor browser. This provides a strong layer of protection for your online activities while accessing the Dark Web.
Why isn’t the Dark Web stopped or shut down?
Although you can keep yourself safe by using a top VPN every time you access Tor, many people believe the dangers outweigh the advantages. Even so, it’s unlikely Tor will be shut down for the following reasons:
- Technical complexity: The Dark Web operates on a hidden network that is difficult to track and shut down. The use of VPNs and other technologies makes it hard to trace the source of illegal activities.
- Freedom of speech: Shutting down the Dark Web could be seen as an attack on freedom of speech and could be met with backlash from civil liberties organizations.
- International jurisdiction: The Dark Web operates across multiple jurisdictions and countries, making it difficult to coordinate law enforcement efforts to shut it down.
- Legitimate uses: Although the Dark Web is often associated with illegal activities, it also has legitimate uses, such as allowing activists and journalists to communicate securely.
- Profitability: Illegal activities on the Dark Web, such as drug and weapon sales, generate significant profits for criminal organizations, which motivates them to continue using it.
- Lack of resources: Governments and law enforcement agencies may lack the resources or expertise to effectively monitor and shut down the Dark Web.
- Investigative tool: Law enforcement agencies can use the Dark Web as a tool for investigations, evidence collection, and covert operations.
Despite these challenges, law enforcement agencies worldwide have tried to track down illegal activities on the Dark Web. They have successfully shut down some notorious marketplaces and criminal networks, but the nature of the Dark Web makes it an ongoing battle.
Can my ISP see that I am accessing the Dark Web?
It depends. If you’re using Tor without a VPN, your ISP will know that you’re accessing the Dark Web. Even if you’re using a VPN, you’ll have to use the Tor over VPN setup to hide the fact that you’re accessing the Dark Web from your ISP.
When you use the Tor over VPN method, your ISP cannot see that you’re accessing the Dark Web. In this setup, you first connect to the VPN, which hides your online activities from your ISP. As a result, they can only see that you’re connected to the VPN, not Tor or the Dark Web.
On the other hand, if you use the VPN over Tor method, your ISP can see that you’re using Tor, but they cannot see what you’re doing on the Dark Web. In this case, you connect to Tor first, and then the VPN. While your activities on the Dark Web are encrypted and hidden, your ISP can still detect that you’re using Tor.
Can I be traced, tracked, or hacked if I access the Dark Web?
Yes, it is possible to be traced, tracked, or hacked if you access the Dark Web. Using a VPN with a strict no-logs policy is crucial when accessing the Dark Web, as it adds another layer of security and privacy to your online activity.
Remember that while the Dark Web provides a level of anonymity and privacy for its users, it is not foolproof. Your activities on the Dark Web can be traced or monitored by third parties, such as government agencies, hackers, or cybercriminals.
In addition, the Dark Web is home to a range of illegal activities and content, including drug trafficking, weapon sales, and cybercrime, which can attract the attention of law enforcement agencies and other authorities.
Warning! If you do not take proper precautions, such as using a secure VPN with a Tor browser, your online activity and personal information may be at risk of being hacked or compromised. This can lead to identity theft, financial fraud, and other serious consequences.
Can I access the Dark Web with a free VPN?
You may be able to access the Dark Web with a free VPN, but I don’t recommend it. Always use a VPN with strong security features for browsing the Dark Web. Free VPNs often lack the security protocols necessary to keep your online activity safe and anonymous, leaving you vulnerable to hacking attempts and other security threats on the Dark Web.
Many free VPNs collect and share user data with third parties, compromising your privacy and potentially exposing you to targeted advertising or other unwanted marketing tactics.
Also, free VPNs often have unstable connections and slow speeds, making it difficult to access and browse the Dark Web efficiently. This can result in frustration and longer load times, which may deter you from continuing to use the service. If you still want to use them, these free VPNs offer some protection.
Browse the Dark Web Safely With Tor Over VPN
The Dark Web provides its users with digital freedom and unlimited resources. Despite the Darknet’s negative reputation, there are plenty of positive ways to browse without putting yourself at risk. Though it’s not illegal to access the Dark Web, it’s important to follow precautions to use it safely.
A VPN keeps you safe on the Dark Web by encrypting your internet connection, hiding your IP address, and preventing your ISP and other third parties from tracking your online activities on the Dark Web. I recommend ExpressVPN for accessing the Dark Web. Its exceptional security features and independently audited no-logs policy safeguard you from being exposed to hackers, identity thieves, and government surveillance.
The best part is you can buy ExpressVPN for the Dark Web in confidence. All its plans are backed by a 30-day money-back guarantee. If you decide it’s not for you, you can get a full refund. When I tested the guarantee over the live chat, the agent immediately approved my request and I got my money back in 3 days.








Leave a Comment
Cancel