Can My iPhone Be Hacked? Yes! Secure Your iPhone in 2024
Apple’s iOS is very secure, but your iPhone is still vulnerable to being hacked. Unsecured WiFi, shady third-party apps, or zero-day attacks are genuine threats to your iPhone, and to your personal data security.
If you’re concerned, there are some telltale signs that your iPhone has been hacked — it may be hot to the touch with excessive battery drain, contacts may report getting strange messages from you, or you may have been locked out of your Apple ID.
Fortunately, there are some easy ways you can fix a hacked iPhone and improve your security. You should delete apps you don’t recognize, monitor your privacy settings, and add an iOS security app like Norton — it has perfect real-time protection to stop attacks before they reach your sensitive data.
Protect your iPhone with Norton
Quick Guide: How to Fix a Hacked iPhone
- Install security software — I recommend you try Norton for iPhone due to its perfect real-time protection and useful extras like data breach scanner and spam protection.
- Change your Apple ID Password — Regain control of your account by changing to a more secure password and enabling two-factor authentication (2FA)
- Remove configuration files — In “VPN & Device Management” settings, delete profiles that you don’t recognize.
- As a last resort, factory reset your iPhone — Returning your iPhone to its original state removes all malicious software and data.
How Are iPhones Hacked?
Apple’s iOS is designed to stop iPhones from being hacked by malware, viruses, or ransomware, making it very difficult to hack your device. However, it’s possible that hackers can get into your iPhone through vulnerabilities in the system or sophisticated scams that get you to part with your personal information.
Jailbreaking
Jailbreaking bypasses Apple’s restrictions and lets you install unauthorized apps, tweaks, and themes unavailable from the App Store. This creates holes in your iPhone’s security, preventing iOS updates and exposing it to threats. Jailbreaking can also disable application sandboxing, making it easier for malicious software to overtake your device.
Weak Personal Security
Using weak passwords that are short and simple, or that include information that can be easily found online (like your birthday) makes it easier for hackers to attack your iPhone.
Phishing
Phishing attacks trick you into clicking suspicious links and revealing sensitive data, like login info or financial credentials. Hackers may use emails, text messages, or social media messages that appear to be from legitimate organizations.
MDM/Provisioning Profiles
Mobile Device Management (MDM) profiles are legitimate tools organizations use to manage devices like iPhones within their network. Malicious MDM profiles can give attackers remote control over your iPhone, letting them view your data, install apps, track you, or remotely wipe your device.
Unsafe WiFi
Hackers can exploit unencrypted WiFi networks to intercept sensitive data flowing between your iPhone and the internet. Attackers can also create fake WiFi hotspots, luring unsuspecting users to connect. Once connected, they can steal data or redirect you to malicious websites.
Zero-Day Malware Attacks
Zero-day attacks are very rare, but happen when a hacker discovers and exploits a vulnerability before the developers are aware of it. Unfortunately, there’s no way to tell if or when this kind of attack will happen.
Is My iPhone Hacked? 8 Signs Your iPhone Has Been Hacked
If you’ve noticed your iPhone has been behaving a little differently than usual, take a look at the following signs that your device has been hacked:
-
- iPhone runs out of battery quickly or is hotter than usual — Malicious apps consume extra resources, causing your iPhone to overheat or drain the battery faster. Your device could be executing tasks set by the hacker, like cryptocurrency mining or transmitting data.
- You’re locked out of your Apple ID — With a successful phishing attack, a hacker can access your Apple ID and lock you out of your iPhone, compromising your personal information.
- High data usage — An unexpected spike in data use can signal a hacked iPhone, as this could suggest data transfers to an external server or malicious downloads occurring.
- Unknown apps on your home screen — Unknown apps can be silently installed through system vulnerabilities or phishing attacks. Such apps are trojans that create backdoors for attackers to exploit your device, steal your data, or track you.
- Strange messages sent to your contacts — your contacts may report receiving messages or emails you didn’t send, as hackers who have accessed your iPhone may try to spread phishing links, malware, or scams with your network.
- Unauthorized purchases — If your Apple ID is compromised, hackers can buy apps, games, music, or physical goods. Should you notice suspicious financial activities, immediately change your Apple ID password and contact Apple support.
- Dropped performance — Malicious apps can secretly run in the background and consume your iPhone’s resources, causing your device to slow down or apps to crash.
- Camera or microphone light is on — Seeing the camera or mic indicator light on when you’re not using an app that requires visual or audio capture is a sign of unauthorized access. Hackers can use spyware to secretly record conversations or your surroundings for surveillance.
10 Steps: How to Fix a Hacked iPhone
1. Download and Install Security Software
Having iOS antivirus installed on your iPhone is the first step to fixing a hacked device. An app like Norton (one of the top antivirus services in 2024) blocks malicious websites hosting phishing attacks, checks for device and app vulnerabilities, and looks at app behavior to determine if it’s malicious.
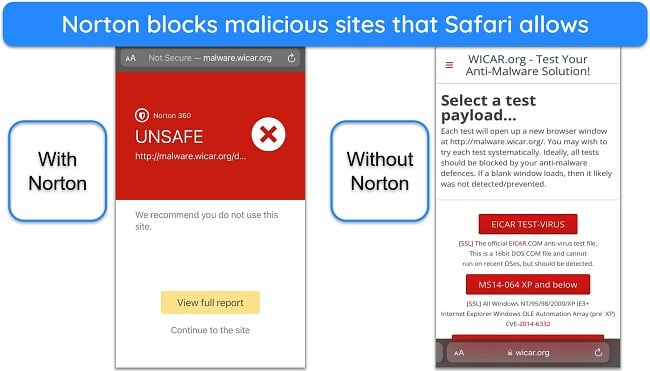
You should note that reputable iOS antivirus software doesn’t work like traditional antivirus. If you see iOS antivirus apps advertising malware scans, avoid them — it’s not possible for one app to scan another on your iPhone due to the way Apple’s OS and apps operate.
2. Change Your Apple ID Password & Enable Two-Factor Authentication
Changing your Apple ID password lets you regain control of your account. You should also enable two-factor authentication (2FA) for your Apple ID to add an extra layer of security. This way, even if someone discovers your password they’d still need access to your trusted device to log in.
3. Remove Any Configuration Profiles
Malicious profiles may have been installed without your knowledge. Go to ‘Settings,’ ‘General,’ and tap ‘VPN & Device Management.’ If you find any profiles that you don’t recognize or remember installing, delete them. Removing these will revoke any unauthorized controls over your device.
4. Update iOS and Apps
Updates include patches for vulnerabilities that hackers could exploit.
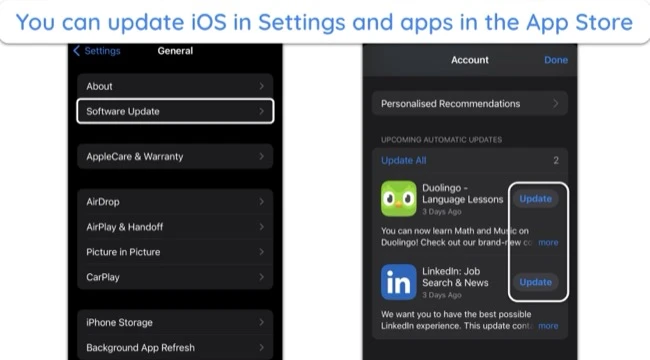
To update iOS, go to ‘Settings,’ ‘General,’ and tap ‘Software Update.’ For apps, open the App Store, tap on your profile icon, and update any apps that aren’t currently running the latest version.
5. Uninstall Unsafe or Suspicious Apps
If you’ve identified suspicious apps you don’t recall downloading, uninstall them immediately. Press and hold the app icon on your home screen and tap ‘Remove App.’ Or, go to ‘Settings,’ tap ‘General,’ and ‘iPhone Storage,’ then tap the suspicious apps and choose ‘Delete App.’
6. Check Your App Privacy Settings and Your Subscriptions
Review the privacy settings for each app and ensure they only have access to necessary information. Go to ‘Settings,’ scroll down to ‘Privacy & Security,’ and adjust permissions for location, contacts, photos, and more.
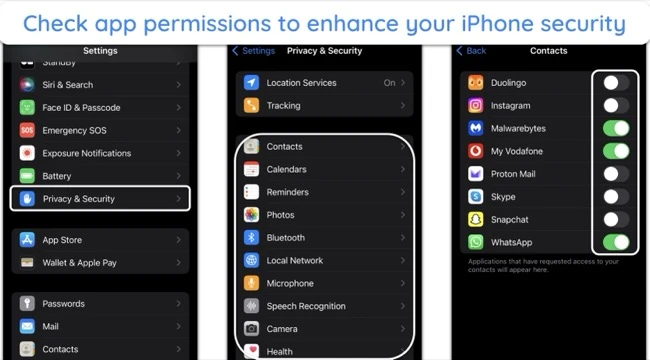
Additionally, check your subscriptions. If you find unauthorized subscriptions, cancel them immediately.
7. Run a Data Breach Scan
A data breach scan compares your email address and other personal details against databases exposed in known breaches. If the scan reveals a compromise, immediately change the passwords for the affected accounts and consider additional security measures like credit monitoring if financial information is involved.
8. Use a VPN (Virtual Private Network)
A VPN encrypts your internet traffic before it leaves your iPhone, scrambling your data into bits of code. Even if hackers intercept your data, they won’t be able to read it. A VPN also masks your original IP address, making it more difficult for hackers to track your online activity. Some antiviruses have a built-in VPN, so you don’t have to buy a standalone VPN.
9. Check Your iOS Calendar for Any Suspicious Events
Hackers can add spam or phishing events to your calendar. Open your Calendar app and look for any events you don’t recognize, especially those with suspicious links or unclear descriptions. You can delete these directly and adjust your calendar settings to prevent unwanted additions in the future.
10. Reset Your iPhone
If you suspect your iPhone is still compromised, perform a factory reset as a last resort. This will erase all data (including malicious software), returning your iPhone to its original state, so make sure you back up important data. To reset, go to ‘Settings,’ General,’ and tap ‘Transfer or Reset iPhone.’ You’ll have to use FaceID or your phone’s unlock code.
Tips to Protect Your iPhone From Getting Hacked
Besides the steps above, you must observe safe practices to prevent malware attacks. Here are a few additional tips to consider:
- Don’t jailbreak your iPhone — not only does this prevent you from updating iOS to patch vulnerabilities, but sideloading apps is a huge security risk as many unvetted applications contain malware.
- Set up a SIM pin lock — this prevents unauthorized use of your data plan if your iPhone is misplaced or stolen by requiring a PIN to access cellular services.
- Disable automatic WiFi connections — stops your iPhone from automatically connecting to WiFi networks, reducing the risk you’ll join a malicious one.
- Enable Find My iPhone — helps you locate your device if lost or stolen, and allows you to erase data remotely, if necessary.
- Switch off Bluetooth when not in use — this prevents malicious devices from connecting to your iPhone and stops your phone from trying to connect to other devices.
The Best Software to Prevent iPhone Hacks — Full Test Results in 2024
1. Norton — Best Overall Antivirus to Prevent iPhone Hacks
Key Features:
- 100% real-time protection score against iOS-specific threats
- Protects you from shady WiFi, spam SMS, and suspicious iOS Calendar invites
- Works on iOS 15 or above — compatible with macOS, Windows, and Android
- Fast customer support via 24/7 live chat, phone, and online resources
- 60-day money-back guarantee
Norton is the top choice for protecting your iPhone, with a range of impressive security and privacy features that detect 100% of malware and block 100% of real-time infections. These include:
- SONAR analysis — using heuristic analysis, checks app behavior and prevents damage if the app acts suspiciously, even if the threat hasn’t been previously identified.
- Firewall — creates rules for each app and blocks connections with attack signatures while maintaining a safelist of trusted apps like Skype.
- WiFi security — scans WiFi networks and lets you know if they’re safe to connect to by examining encryption standards, network configuration, and authentication protocols.
- Spam protection — blocks scam URLs and any malicious links via SMS (iMessage not supported) and prevents annoying calls.
- Secure Calendar — scans and blocks incoming calendar invitations for suspicious characteristics, like vague event details and unusual sender information.
You can get Norton on iOS with its Norton Mobile Security plan, but I’d choose the Deluxe plan at $49.99/year as it covers up to 5 simultaneous connections. It offers a separate plan for US users, with up to 250GB of cloud storage, wallet protection, and Identity Lock.
2. TotalAV — Optimization Tools Improve Your iPhone’s Performance
Key Features:
- 100% detection and 100% real-time protection score
- Includes a built-in VPN, data breach checker, ad blocker, and password manager
- Supports iOS 8 or above — apps for macOS, Windows, and Android
- Customer support channels include live chat, email, phone, and online guides
- 30-day money-back guarantee
TotalAV’s iPhone app improves performance to avoid vulnerabilities compromising your device. Its impressive features include the following:
- Smart Scan — checks for security vulnerabilities and performance issues, like automatic updates, two-factor authentication, and WiFi encryption.
- WebShield — blocks unsafe websites before you can open them (you can also configure it to block crypto-mining URLs and untrustworthy sites).
- Data breach scanner — checks if your email and passwords have been compromised in past data breaches.
- QR code checker — blocks malicious sites hidden behind QR codes to prevent potential phishing attacks.
Although it doesn’t have a firewall or support device scans like Norton, the Smart Scan maintains your iPhone’s health without overburdening it. With TotalAV, my iPhone didn’t slow down even when I browsed the web on multiple Safari tabs.
You can get TotalAV for as low as $19.00, but I recommend the Total Security Plan, which protects up to 6 devices simultaneously.
3. McAfee — Identity Protection Protects Your Personal Data From Hackers
Key Features:
- Real-time protection score of 100%
- Includes identity monitoring, a built-in VPN, web protection, and a WiFi scanner
- Compatible with iOS 13 or above — supports all popular platforms
- Live chat and phone support, plus online knowledgebase
- 30-day refund guarantee
McAfee’s Identity Protection checks if your information has been leaked on the dark web so you can take immediate action. It also has credit monitoring and lost wallet protection to mitigate financial loss, though it’s only available in some countries like the US. McAfee also protects your iPhone with:
- System Scan — checks for outdated software and other vulnerabilities, giving your iPhone an overall protection score and recommendations on how to improve it.
- WiFi Scanner — checks a network’s encryption strength and reputation, alerting you to potentially risky public WiFi before you can connect.
- Secure VPN — encrypts your data and routes it through another location, keeping you anonymous on the web at all times.
The Mobile Security plan protects 1 iPhone. I suggest the $49.99/year plan that supports 10 simultaneous devices.
FAQs on iPhone Hacks Recovery and Protection
Can my iPhone be hacked?
Can someone hack my iPhone remotely, through a website, or with a phone call?
What does a hacked iPhone look like?
My iPhone is hacked – what do I do?
What’s the best way to protect my iPhone from hackers?
Is there free security software for my iPhone?
Are iPhones more secure than Android?
Keep Your iPhone Safe From Hackers With the Best Software
If you don’t know the signs of a hacked iPhone, you could face significant financial losses. Apple’s built-in security alone isn’t enough to prevent modern threats. Besides observing safe browsing practices, using a reliable iOS-focused antivirus is your best chance to protect your iPhone from hackers.
After extensive testing, Norton stands out as the top antivirus for iPhones. It offers perfect real-time protection and extras like phishing, spam link, and WiFi protection. You can try Norton risk-free with its 60-day money-back guarantee.






Leave a Comment
Cancel