Can A VPN Be Hacked? (Easy Guide to Find Safe VPNs in 2024)
I wasn’t fully aware of why it was so important to use a VPN until my name, and personal details were publicly leaked. Since then, I have always used a VPN, but despite offering privacy and security protection — I learned that some VPNs, especially free ones, are particularly susceptible to hacking.
Hackers can intercept your data even when you’re using a VPN if its encryption isn’t strong enough or it keeps data logs. You need a VPN with AES 256-bit encryption, strict no-logs policies, and/or ad and malware blockers to guarantee your data is secure.
To find the safest VPNs that can’t be hacked, I thoroughly tested dozens of VPN services. Of them all, ExpressVPN provided the best security, privacy, and reliability, thanks to its military-grade encryption and proven no-logs policy. You can try it risk-free, too, thanks to its 30-day money-back guarantee. *Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
Protect yourself using ExpressVPN
Quick Guide: 7 Best VPNs to Avoid Hacks and Ensure Security in 2024
- ExpressVPN — TrustedServer technology ensures complete protection from hackers, with RAM-only servers to automatically delete data. Try ExpressVPN risk-free.
- CyberGhost — An integrated ad and malware blocker for additional protection against trackers and hackers. However, long-distance connections can be slightly slow.
- Private Internet Access (PIA) — Its small packets feature boosts your speeds when using WireGuard and OpenVPN. However, it’s located at the heart of the knowledge-sharing network 5/9/14 Eyes Alliance.
- PrivateVPN — Perfect forward secrecy feature for continuously changing your private keys on a regular basis to protect your data from hackers. But, it has the smallest server network on this list.
- NordVPN — Offers strong security and a large server network, but its user interface may not be as intuitive or user-friendly compared to other VPN options.
Surfshark — Strong privacy features, including a strict no-logs policy and an automatic kill switch, but it has a relatively small server network. - IPVanish — Internally operated servers keep your information safe while browsing. However, the lack of a cryptocurrency payment option makes it difficult for you to remain completely anonymous.
Editor’s Note: We value our relationship with our readers, and we strive to earn your trust through transparency and integrity. We are in the same ownership group as some of the industry-leading products reviewed on this site: ExpressVPN, Cyberghost, Private Internet Access, and Intego. However, this does not affect our review process, as we adhere to a strict testing methodology.
How Does a Virtual Private Network (VPN) Get Hacked?
Cheap (or free) VPNs with limited security features are more likely to get hacked than a premium provider. The more reliable the VPN, the more secure it will be against hackers intercepting the VPN’s encryption and stealing valuable data from its users. Before you commit to a VPN subscription, you need to be sure it’s not vulnerable to one of the many ways hackers can access your data:
1. Hackers Can Break A VPN’s Encryption and Steal Personal Data
VPN encryption transforms readable data (plaintext) that travels through the internet into unreadable data (ciphertext), anticipating an unwanted interception. A VPN protocol houses an algorithm or cipher that dictates how the encryption and decryption process occurs. Without these processes, hackers would be able to steal and read your data in seconds. Check out this beginner’s guide to using VPNs to find out more. Types of encryptions can include:
- Protocols. Protocols ensure the security and stability of your internet connection, acting as a set of rules for data transmission and encryption. Examples of protocols include:
- OpenVPN
- Lightway (most secure)
- WireGuard
- IPSec/IKEv2 (less secure)
- Cryptographic Algorithms. The best VPNs allow you to choose between symmetric (one secret key), asymmetric (two secret keys), or hashing (one-way encryption) ciphers, which use cryptographic algorithms to decipher messages.
AES (Advanced Encryption Standard). A symmetric block cipher used by the US government to protect confidential information, AES leverages SPN (Substitution Permutation Network) algorithms to develop multiple rounds of data encryption. Choose between:- 128-bit
- 192-bit
- 256-bit (military-grade encryption)
- Secure Hash Algorithms (SHA). Used to shorten input data into small pieces that bitwise operations, modular additions, and compression functions can’t decipher:
- 160-bit hash digest (SHA-1)
- Between 224-bit and 512-bit hash (SHA-2)
- RSA Encryption (Rivest-Shamir-Adleman Encryption). RSA works with encryption schemes and digital signatures to prove the authenticity of messages, using public and private keys to encrypt and decrypt data. For example, RSA works with:
- OpenSSL
- wolfCrypt
- cryptlib
Although complex and expensive when attempted on a premium VPN, it’s much easier for hackers to break your VPNs encryption if it doesn’t use advanced security measures. For example, AES and RSA encryption will make it almost impossible for hackers to access your data. One of the best VPNs in the world, ExpressVPN, uses these and more to ensure tight encryption so no data leaks out. You can try ExpressVPN to test its security features risk-free for 30-days thanks to its money-back guarantee.
2. Encryption Keys Can Be Stolen and Used To Access A VPN
Encryption keys encode and decode data, which is why hackers focus on stealing keys to bypass your VPN’s encryption and intercept your data. Hackers don’t require advanced software with an encryption key and can see, steal, and even alter your information. Despite encryption keys being unique and unpredictable, hackers are consistently finding new ways to access your data — leaving you with no choice but to protect yourself using a VPN.
3. VPNs That Have IP or DNS Leaks Make It Easy For Hacker To Steal Information
Although not considered a hack, IP and DNS leaks reveal all of your internet history and location and are the most common way for hackers to steal your data. These leaks result from inadequate security protocols and the lack of a simple kill switch, which are often found in top VPNs. However, you must remember that experiencing IP and DNS leaks is due to your VPNs inability to protect your information and happens more often with free VPNs.
4. Hackers Exploit Server and Other General VPN Vulnerabilities
VPNs that hold data within hard drives until deletion are less secure than VPNs using RAM servers. Hackers will often test VPNs as I would, searching for vulnerabilities they can exploit. However, it’s not only a lack of security that hackers leverage to access your data. For example, a VPN utilizing server networks owned by third parties is more likely to experience cyber attacks as hackers exploit weaknesses that VPNs ignore. ExpressVPN’s RAM-only servers automatically delete your data to save your personal information from prying eyes.
5. Hackers Steal User Logs
Due to generating over 2.5 quintillion bytes of data each day, hackers can easily commit fraud and identity theft, access your social media accounts, and even blackmail you for further gains. To overcome this, VPNs have introduced no-logs policies that ensure you remain anonymous and protected. However, while reviewing a variety of VPNs, I’ve noticed that some no-logs policies aren’t accurate and are often a way for VPNs to portray security rather than provide it — especially with free VPNs.
How to Choose a Secure VPN That’s Near Impossible to Hack
I’ve listed the essential features you need to know before choosing a VPN. Without these features, you may be susceptible to hacks and select an unsuitable VPN to protect your privacy. When purchasing a VPN subscription, you must:
1. Select a VPN With AES 256-bit Encryption
When searching for a VPN to protect your privacy, you must consider whether it offers AES 256-bit Encryption. 256-bit encryption is the best you can get in terms of security, offering complex and uniquely lengthy encryption keys that instantly deter hackers. I feel safe and protected when using ExpressVPN which provides AES 256-bit encryption as it has never been hacked and endorsed by the US government to protect sensitive information.
2. Find a VPN With OpenVPN/IKEv2 Protocols
When searching for the best VPN to protect your data and ensure anonymity, you must check whether it offers OpenVPN or IKEv2 protocols. Experts believe that OpenVPN is the most popular and recommended VPN protocol due to its open-source nature that is constantly updated and maintained. Whereas IKEv2 is considered super-fast, stable, and works on many more platforms than OpenVPN, which requires third-party software installation.
3. Choose a VPN With SHA-2 Authentication
SHA-2 is the latest and most secure authentication available today, allowing you to receive information free of trackers and malware. Many VPNs utilize SHA-2 authentication to keep you safe when sending and receiving data. However, there are variations of SHA authentication I wouldn’t recommend due to being hacked a plethora of times in the past — SHA-1.
4. Check the VPNs Server Network Management Policies
Checking and understanding a VPNs server network management policies is essential when looking for a safe and secure VPN provider — as not all VPN server networks are designed for total security and can leave you vulnerable to cyberattacks. For example, if the VPN doesn’t own its network, you must be sure that the VPN provides military-grade encryption that covers any third-party servers.
Interestingly, VPN providers have shifted from regular hard-drive servers to more secure RAM servers that protect your data from hackers without maintenance. RAM servers allow the VPN to erase all collected data after every reboot, leaving no data at risk of being stolen by hackers. If you’re looking for the safest and most secure VPN, be sure that they own their network of RAM servers like ExpressVPN to ensure your anonymity and safety.
5. Test the VPNs IP Address and DNS Leak Protection
IP address and DNS leaks are major threats when considering your safety and security, allowing hackers to steal identifiable information such as your address. With leak protection, you remove the chances of hackers stealing your IP address, location, or identity. Finding out that hackers can steal my address motivated me to find a VPN with leak protection and should be one of your priorities when considering online safety.
If you want to make sure you are safe from IP address and DNS leaks, check out the IP address tool and DNS leak test to see for yourself. Conducting these tests assured me that each VPN on this list truly protects you from data leakage, which is one of the easiest ways hackers can access your information.
6. Investigate and Select a VPN With a No-Logs Policy
A no-logs policy assures you that your VPN provider doesn’t collect or hold any information transmitted through its network. Without this feature, there is always a chance of your data falling into the wrong hands. However, you must be aware that some VPNs only promote no-logs policies to seem more secure to potential customers. I was shocked that VPN providers require an external audit to prove its validity, which many haven’t done.
Before committing to a VPN subscription, you need to investigate its no-logs policy and ensure it’s true. Luckily, every VPN on this list has a proven no-logs policy that will protect you even when your VPN is suddenly disconnected.
7. Check for Advanced Features That Block Malware and Ads
Ad and malware blockers allow VPNs to prevent third parties from installing trackers onto your device through advertisements and malicious links. Trackers install malicious malware onto your device that tricks you into providing personal data. But not only that, multiple viruses infect your device and ultimately slow it down until you require a factory reset or premium anti-virus software.
Hackers are getting better at imitating legitimate websites, tricking you into providing data to steal your information. I have accidentally clicked ads that installed viruses onto my device, which made me reconsider my protection. With a premium VPN like CyberGhost, you get ad and malware protection that minimizes the risk of common threats, including:
- Adware – Malicious and irritating advertisements that significantly reduce your operating power and increase the chances of you installing more malware onto your device.
- Fileless malware – Unlike traditional malware that uses executable files to infect your device, fileless malware uses non-file objects within your device to secretly steal data without being detected.
- Worms – Able to spread from one device to another, worms leverage existing weaknesses to modify and delete important information while infecting your devices with more malware.
- Trojans – A malicious program often seen on websites and in emails that trick you into spreading it onto multiple devices by seeming legitimate.
- Bots – Software programs that perform automated tasks without permission to gain access and control multiple devices to create a botnet (a network of compromised devices used to launch massive cyberattacks).
- Ransomware – Information is stolen by hackers and held at ransom through threats until payment is received.
- Spyware – Used by hackers to monitor the activities of their victims using keystrokes to steal usernames, passwords, and personal data.
The Best VPNs for Safety and Security in 2024
1. ExpressVPN — Protect Yourself From Hackers With TrustedServer Technology
- AES 256-bit military-grade encryption, DNS and IP address leak protection, and an automatic kill switch protects your data from international agreements like the DMCA
- Over 3,000 servers in 105+ countries with RAM-only TrustedServer technology
- OpenVPN (UDP & TCP), IKEv2, L2TP/IPSec protocols, and its own Lightway protocol
- Protect up to 8 devices simultaneously including Android and iOS
- 30-day money-back guarantee to enhance your security with confidence
ExpressVPN’s RAM-only TrustedServer technology reduces the risk of getting hacked by deleting your data during every reboot without requiring maintenance. Throughout the testing process, I felt very secure knowing that its servers routinely deleted my data and that no other VPN had implemented such technology. You can try out ExpressVPN risk-free to reduce the risk of getting hacked.
Unlike many VPNs I’ve tested, ExpressVPN allows you to choose your desired protocol depending on the level of security you want and your network settings. For example, I quickly switched between OpenVPN, IKEv2, and L2TP/ IPSec — the fastest and most secure VPN protocols available today. However, while testing ExpressVPN, I found that it developed its Lightway protocol which is much quicker and more secure than OpenVPN.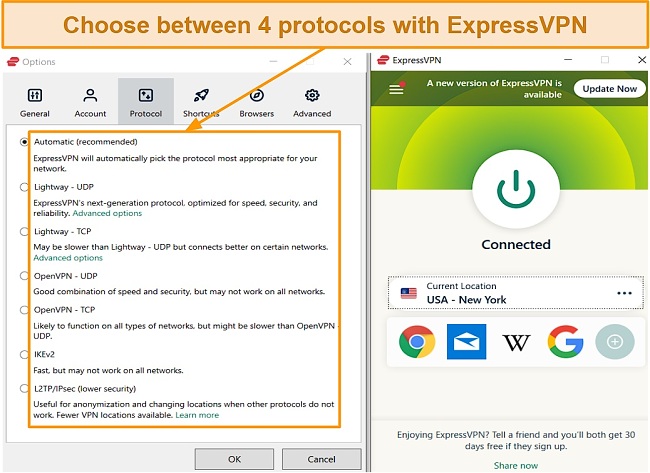
ExpressVPN currently operates within the British Virgin Islands (BVI), allowing it to implement a strict no-logs policy that international agreements can’t govern. Throughout the testing process, I learned that operating in the BVI enables ExpressVPN to avoid data retention laws in and around Europe and mass surveillance programs as seen in the UK and the US — including the 5/9/14 Eyes Alliance.
Despite offering impressive DNS and IP address leak protection, the only minor con I found while testing ExpressVPN was that it doesn’t currently support IPv6 on its general server network. However, ExpressVPN will consider IPv6 support once it becomes more popular and has developed its own in-app IPv6 leak protection feature to ensure your security.
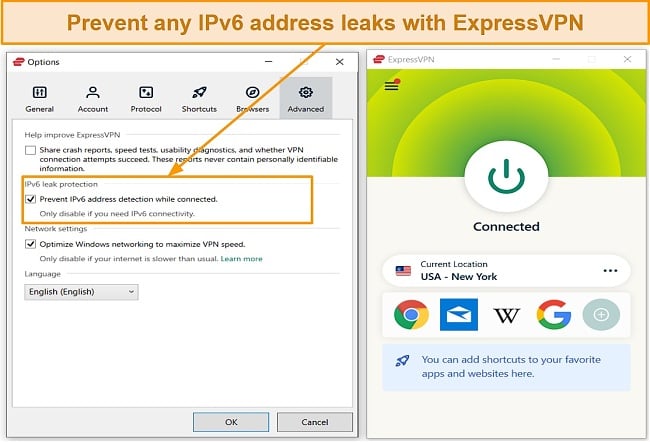
To make sure you can get your money back, I tested ExpressVPN’s money-back guarantee by sending a direct message to its customer service team through its 24/7 live chat. Surprisingly, my refund was processed almost immediately. Download ExpressVPN risk-free with its 30-day money-back guarantee and test its security yourself. If you aren’t satisfied, you can get a full refund just like me within 5 days.
*Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as ExpressVPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
ExpressVPN works with: Windows, Android, macOS, iOS, Linux, routers, Chrome, Kindle, Firefox, PlayStation, Xbox, Nintendo Switch, Apple TV, Amazon Fire TV, and Smart TVs.
ExpressVPN unblocks: Netflix, Disney+, Hulu, Amazon Prime Video, BBC iPlayer, HBO Max, YouTube TV, ESPN, and more.
2024 Update! ExpressVPN has dropped prices for a limited time to a crazy $6.67 per month for the 1-year plan + 3 months free (you can save up to 49%)! This is a limited offer so be sure to grab it now before it's gone. See more information on this offer here.
2. CyberGhost — Integrated Ad and Malware Blockers To Eliminate Hacks From Adware, Worms, and Trojans
- 3 separate blockers against ads, malicious websites, and trackers, AES 256-bit military-grade encryption, and additional WiFi protection to reduce the risk of hacks
- Over 11,676 servers in 100+ countries with NoSpy servers available on its annual subscription
- Choose between OpenVPN, IKEv2, and WireGuard protocols depending on the level of security you want
- Protect up to 7 devices from hackers simultaneously
- A 45-day money-back guarantee to enhance your protection risk-free
CyberGhost’s integrated ad and malware blocker is an excellent feature that reduces the risk of clicking on malicious ads and being infected with viruses. During my thorough tests of CyberGhost, I blocked malware, trackers, pop-ups, video ads, and even banners on my Windows and Android devices — making me feel much more secure while browsing the web.
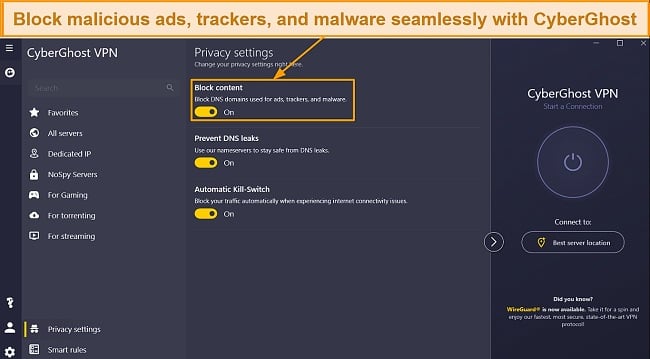
CyberGhost leverages AES 256-bit military-grade encryption and WiFi protection to secure all of your devices, avoiding standard encryption methods used by other VPNs that are more susceptible to hacking — including DES, Blowfish, and Twofish. I found its WiFi protection and military-grade encryption extremely useful while I traveled for work and needed to connect to multiple public WiFi providers.
During my tests, I found that CyberGhost allows you to choose between OpenVPN, IKEv2, and WireGuard protocols. WireGuard is the newest VPN protocol with no known vulnerabilities, offering the right balance of security and speed — which doesn’t happen when using IKEv2. While using CyberGhost, I felt very safe knowing that I could choose the most secure protocols to minimize the threat of cyberattacks.
The only minor con I identified throughout the testing process was that CyberGhost’s iOS app doesn’t support its integrated ad and malware blocker or WireGuard protocols. However, as iOS devices become more popular, it seems inevitable that CyberGhost will implement these measures to protect a large majority of its user’s safety.
I tested CyberGhost’s money-back guarantee to make sure you can get your money back quickly and easily. I messaged its customer service team and requested a refund, which was processed within 2 hours. Download CyberGhost risk-free using its 45-day money-back guarantee. If you aren’t satisfied, you can get a full refund as I did within 7 days.
*Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as CyberGhost VPN. However, this does not affect our review process, as we adhere to a strict testing methodology.
CyberGhost works with: Windows, Mac, Android, iPhone, Chrome, Firefox, Linux, Amazon Fire TV, Amazon Fire Stick, Android TV.
CyberGhost unblocks: Netflix, Disney+, Hulu, Amazon Prime Video, HBO Max, BBC iPlayer, ESPN, Crunchyroll, and Yie.
2024 Update! You can subscribe to CyberGhost for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 84%)! This is a limited offer so grab it now before it's gone. See more information on this offer here.
3. Private Internet Access (PIA) — Dedicated IP Address and Split Tunneling Features Provide Unlimited Flexibility and Security
- AES 256-bit military-grade encryption, split tunneling, an automatic kill switch, and a dedicated IP address enhance your safety and security
- Over 35,000 servers in 91+ countries, the largest network on this list
- Choose between two of the best security protocols, OpenVPN and WireGuard
- Protect up to unlimited devices from hackers simultaneously
- 30-day money-back guarantee
PIA provides a split tunneling feature and a dedicated IP address to ensure your anonymity, allowing you to choose which apps use your VPN and its encryption. Throughout the testing process of PIA, I accessed my social networks on Google Chrome while simultaneously streaming HD content on my US Netflix account — without experiencing error messages or sacrificing my privacy.
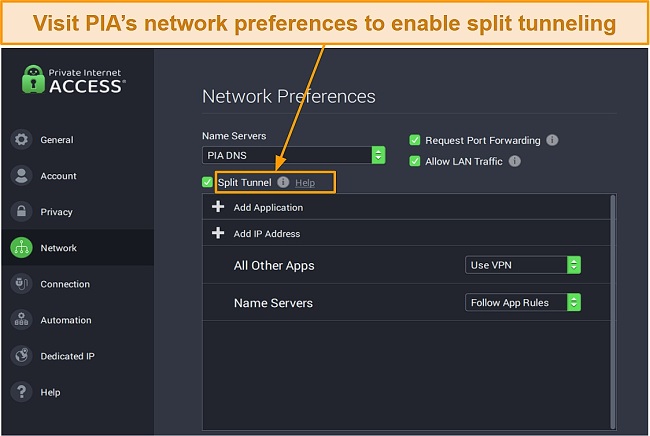
With over 35,000 servers in 91+ countries, PIA has the largest server network on this list that ensures your privacy and protection from anywhere. While testing PIA, I felt highly secure knowing that I could protect myself while traveling abroad for work and using unsecured public WiFi.
You can protect up to unlimited devices simultaneously with PIA — the most out of any VPN on this list. While testing PIA, I hid my location and the IP address associated with my Android phone, Windows laptop, smart TV, and PlayStation 5. I felt extremely safe using PIA to protect my devices as I knew that I had the option to connect more if needed.
The only minor con I identified throughout the testing process was that PIA is currently headquartered within the US and must abide by regulations enforced by the DMCA and the 5, 9, and 14 “Eyes” intelligence-sharing network. However, PIA has a strict no-logs policy that removes all data and cannot share it with the authorities.
During my tests of PIA, I requested a refund through its 24/7 live chat to make sure you could get your money back. Within minutes PIA’s team had responded, processing my refund almost immediately. Download PIA risk-free using its 30-day money-back guarantee. If you’re not satisfied, you can get a full refund as I did within 7 days back into your bank account.
*Editor’s Note: Transparency is one of our core values at WizCase, so you should know we are in the same ownership group as Private Internet Access. However, this does not affect our review process, as we adhere to a strict testing methodology.
Private Internet Access works with: Windows, Mac, Android, Linux, iOS, Chrome, Firefox, and Amazon Fire Stick
Private Internet Access unblocks: Netflix, HBO Max, Disney+, Amazon Prime Video.
2024 Update! You can subscribe to PIA for as low as $2.03 per month + get an extra 4 months free with the 2-year plan (save up to 83%)! This is a limited offer, so grab it now before it's gone! See more information on this offer here!
4. NordVPN — Premium VPN With Cheap Prices on Long-Term Plans
Key Features:
- Short and long-term subscriptions available
- 30-day money-back guarantee
- 6,300+ global servers in 111 countries
- Unlimited bandwidth
- Protect up to 10 devices at once
NordVPN is one of the best VPNs on the market — and you can get super cheap prices when you sign up for a long-term subscription. One thing to note, however, is that when it’s time to renew your subscription, prices do increase quite significantly.
I was particularly impressed with the high performance of every server I tested. Just because a VPN has thousands of servers doesn’t mean they all work. Servers can still struggle to work — and some can even fail to connect completely. However, NordVPN’s servers work with Netflix for smooth, buffer-free streaming.
I did, however, have issues with using NordVPN’s native Fire TV app. Although it mostly worked with Netflix, it sometimes had issues and kept crashing. I also found that NordVPN’s user interface for desktop devices was less user-friendly than ExpressVPN and CyberGhost.
NordVPN has the following security and privacy features:
- AES 256-bit encryption
- kill switch that cuts your internet access if your connection to a VPN server drops suddenly
- built-in ad and malware blocker, so you don’t need a third-party ad blocker
- fully audited no-logs policy (audited by PwC) – NordVPN doesn’t store any personal or identifying data while you’re connected to the VPN
In addition, NordVPN includes Threat Protection that protects you from viruses, infected websites, and trackers – and it works whenever you have the NordVPN app open, even if you’re not connected to a VPN server.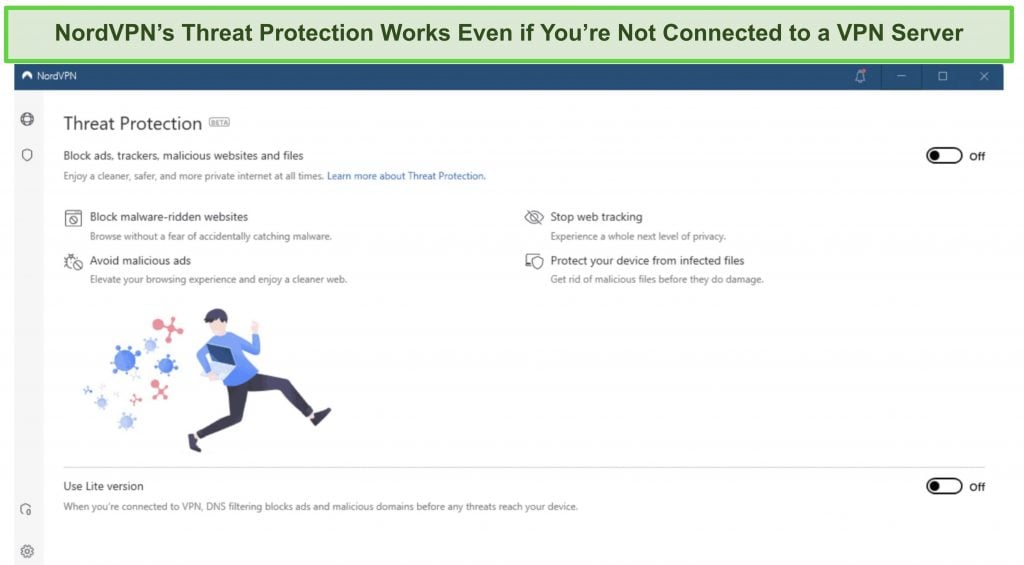
With plans that cost as little as $3.39 per month, it's easy to find a NordVPN subscription plan that suits your needs. You can also stream, torrent, and browse for free for up to 30 days with its money-back guarantee. I tested this to ensure that you’ll really get your money back. At first, the support team tried to give me an extended trial period — but they initiated my refund right away after I told them I wasn’t interested in the extension. I got my money back in 6 business days.
NordVPN works with: Netflix, Amazon Prime Video, BBC iPlayer, Hulu, Disney+, SkyTV, HBO Max, SHOWTIME, DAZN, ESPN, YouTube TV, and more
NordVPN works on: Windows, Mac OS, Android, iOS, Windows Phone, Chromebook, Linux, Chrome, Firefox, Fire Stick, and Android TV
5. Surfshark — Best Value for Money with Unlimited Device Connections and Fast Speeds
Key Features:
- Short and long-term plans available
- 30-day money-back guarantee
- 3,200+ global servers in 100 countries
- No bandwidth restrictions
- Connect unlimited devices at once
Surfshark offers the best value for money out of every premium VPN on the market. You can connect an unlimited number of devices with a single subscription, which means you can use Surfshark on all your devices without getting logged out.
I tested Surfshark’s simultaneous connections on 2 PCs, 2 phones, a Fire Stick 4K, and an iPad. My connection remained reliable on all 6 devices. Even while I was actively streaming on all my devices, my average speed was 112 Mbps — fast enough for UHD quality.
When I saw the price of this service, I thought it couldn’t possibly have top-grade security features for such a low price, but I was pleasantly surprised.
Surfshark has the following security and privacy features:
- AES 256-bit encryption on all devices, with ChaCha encryption available for Android users
- Wireguard VPN protocol enabled by default
- diskless, RAM-only servers to protect your privacy (no data can be physically extracted from any servers)
- kill switch (although this isn’t enabled by default)
- IP and DNS leak protection
Surfshark offers two-factor authentication (2FA) on your account. This feature requires you to enter an extra code before you can log in to ensure that only you can access your account.
While Surfshark does have slightly fewer global servers than rivals such as CyberGhost and PIA, I didn’t experience any issues during my tests. I easily connected fast working servers every time, and I had excellent speeds for streaming, downloading torrents, and browsing the internet.
You can try Surfshark for yourself with the 30-day money-back guarantee. It has plans that cost as little as $2.19. Requesting a refund is easy with Surfshark’s live chat feature. Although the support team asked why I wanted to cancel my subscription, I had no problem getting my money back (and it only took 4 days!).
Surfshark works with: Netflix, Amazon Prime Video, Disney+, BBC iPlayer, Sling TV, Hotstar, HBO Max, DAZN, and more
Surfshark works on: Windows, Mac OS, Android, iOS, Linux, Fire Stick, Samsung Smart TVs, LG Smart TVs, Android TV, Kodi, and selected routers
6. PrivateVPN — Perfect Forward Secrecy Ensures Your Protection By Regularly Changing Your Private Key
- AES 256-bit military-grade encryption and perfect forward secrecy change your private keys to reduce the chances of your data being intercepted
- A reasonably small network with over 200 servers in 63+ countries
- Choose between OpenVPN, L2TP, IPsec, PPTP, and IKEv2
- Protect up to 10 devices from hackers simultaneously
- 30-day money-back guarantee to protect yourself risk-free
PrivateVPN uses AES 256-bit military-grade encryption and perfect forward secrecy to protect you from hackers. Perfect forward secrecy works by continuously changing your private keys on a regular basis, making it difficult for hackers to access and steal your data.
With PrivateVPN, you can choose between multiple security protocols, including OpenVPN, L2TP, and PPTP. During my tests of PrivateVPN, I could select a protocol depending on the speed and security I wanted during the session meaning you’ll be able to maximize your internet speed and security while using PrivateVPN.
Public Wifi protection from PrivateVPN allows you to avoid data theft and prying eyes when using unsecured networks. Public Wifi protection is particularly important while traveling abroad, where scammers and the lack of passwords make your devices susceptible to hacks.
Despite this, PrivateVPN has the smallest server network on this list with over 200 servers in 63 countries. However, the servers it does have are extremely effective at accessing geo-blocked websites, protecting your data from potential hackers, and overcoming online censorship while traveling abroad. But if you’re looking for a larger server network with better coverage, you can try out PIA with over 35,000 servers worldwide.
To make sure you could get your money back, I tested PrivateVPN’s money-back guarantee by messaging its customer service team through its 24/7 live chat feature. I received a quick response and my refund was processed in less than 24 hours. Download PrivateVPN risk-free using its 30-day money-back guarantee. If you’re not satisfied with your subscription, you can request a refund as I did and receive the money into your bank account within 7 days.
PrivateVPN works with: Windows, Mac, Android, Linux, iOS, Chrome, Firefox, and Amazon Fire Stick.
PrivateVPN unblocks: Netflix, Disney+, HBO Max, BBC iPlayer, Hulu, and Amazon Prime Video.
2024 Update! PrivateVPN has dropped prices for a limited time to a crazy $2.00 per month with the 3-year plan (you can save up to 85%)! This is a limited offer so be sure to grab it now before it’s gone. See more information on this offer here.
7. IPVanish — Internally Operated Servers Provide the Best Privacy and Protection From Hackers
- AES 256-bit military-grade encryption, an automatic kill switch, and a zero-logs policy keep your data hidden and protected from third parties
- Over 2,400 internally operated servers in 55+ countries
- Choose between IKEv2, IPsec, OpenVPN, and L2TP
- Protect unlimited devices simultaneously
- 30-day money-back guarantee
IPVanish is one of the only VPNs that have over 2,400 internally operated servers in 55+ countries, allowing you to stay safe while connected and browsing the internet. The lack of outsourced servers ensures that you have full control of your privacy and don’t have to worry about the reliability and security of intermediaries.
Military-grade encryption, an automatic kill switch, a strict no-logs policy, and DNS leak protection allow you to use the internet without risk by holding zero personal data and cutting your connection if the VPN malfunctions. Accordingly, it is difficult for hackers to intercept your internet history or target you while unprotected.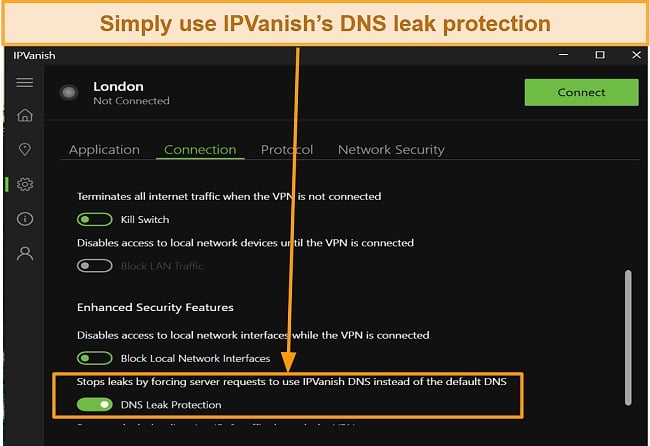
With IPVanish, you can protect unlimited devices simultaneously using a variety of dedicated apps that you can download on your iOS, Android, Mac, and Windows devices. In addition to this, IPVanish allows you to protect your Amazon Firestick, Roku, and tablet.
Unfortunately, IPVanish doesn’t accept cryptocurrency payments making it difficult for you to remain anonymous while purchasing its subscription. However, you can purchase IPVanish with your debit card, credit card, and PayPal account while using two-factor authentication to protect yourself from prying eyes and hackers. For complete anonymity, try out ExpressVPN which accepts cryptocurrency payments to keep your payment details anonymous.
I tested IPVanish’s money-back guarantee to make sure you could get your money back easily by sending its customer service team a message through its 24/7 live chat. Despite taking a few hours to respond, my refund was processed quickly and efficiently no questions asked. Install IPVanish using its 30-day money-back guarantee. If you’re unhappy with IPVanish, you can get a full refund as I did within 7 days.
IPVanish works with: Windows, Mac, Android, Linux, iOS, Chrome, Firefox, and Amazon Fire Stick.
IPVanish unblocks: Netflix, HBO Max, ESPN, Spotify, Vudu, and Kodi.
The Biggest Risks Associated With Your VPN Getting Hacked
Without military-grade encryption and no-logs policies to protect your privacy, there are a variety of risks you should consider when using free VPNs or no VPN at all, including:
- Hackers restricting your access to your mobile devices – Almost impossible to overcome once implemented, hackers can block access to your mobile devices until a ransom is paid.
- Hackers gaining access to your usernames and passwords – If your VPN gets hacked, hackers can steal information from your social media profiles and blackmail you into giving them money.
- Hackers getting credit cards or opening bank accounts in your name – While it might not be readily apparent, hackers possess the capability to establish bank accounts and participate in deceitful actions without getting noticed.
- Hackers ruining your credit – In the event of a hacker gaining access to your personal information, they might utilize your strong credit score to apply for loans and credit cards, with no intention of repaying them.
- Hackers making purchases in your name – If your VPN fails to protect you from cyberattacks, hackers can use your name and bank details to purchase goods online.
- Hackers adding themselves as authorized users on your accounts – Despite being easy to spot, hackers can add themselves onto your accounts to steal information and make purchases without your permission.
- Hackers using your social security number – With your social security number, hackers can gather more information about you to commit identity theft and fraud.
- Hackers controlling your smart home devices – If hackers bypass your VPN’s security protocols, they can access your smart home devices and enter your home at any time.
- Hackers destroying your privacy – Without a secure VPN connection, you are susceptible to government surveillance in countries like the US.
How To Minimize the Risk of Your VPN Being Hacked
The best way to minimize the risk of your VPN getting hacked is to commit to a reputable VPN provider outside the US. With a secure VPN like ExpressVPN, hackers will find its military-grade encryption and TrustedServer technology a deterrent — aiding you in your search for online protection.
Similarly, you can create a VPN chain — multiple VPNs connected at once to tunnel your internet connection through numerous intermediary servers. However, this is an expensive solution as you must purchase more than one VPN subscription.
You can implement the following steps to minimize the risk of cyber threats and ensure that any breaches to your VPN don’t affect your overall security:
- Consistently update your operating systems and mobile applications – Each update provides additional security features that help protect you and prevent malicious activities. You can do this by selecting “automatic update” on all of your devices.
- Monitor your online and offline activities – Configuring notifications to alert you about any account access from a new device or IP address stands as the most efficient way to promptly identify any questionable activity. This method empowers you to establish personalized alerts that will promptly notify you once such access takes place.
- Disconnect old devices and wipe all unused data – Hackers leverage unused accounts to steal information in secret and can even find information on old devices that have been sold. You can reduce this risk by erasing all data using your mobile device’s “factory reset” button.
- Develop passphrases and encourage complexity – Passwords are often easy for hackers to find, leaving you unprotected on all of your devices. You can do this by using special characters (@) and changing your passwords every 3 months.
- Use multi-factor or two-factor authentication – A simple code sent to you by text message in addition to a complex password makes your accounts almost impossible to access without your consent. You can turn on two-factor authentication on most modern social media platforms and use an authenticator app for optimum security.
- Encrypt everything – Encrypting your messages and emails presents an ideal method to lower the risk of hacking. Services like WhatsApp employ automatic encryption for messages, videos, and voice messages, safeguarding them from unauthorized access. It’s advisable to utilize such platforms whenever feasible.
FAQs on Protecting Yourself From Hackers Using a VPN
Does using a VPN make me anonymous?
What to do if your VPN is hacked?
Can my phone get hacked remotely when using a VPN?
Which VPNs have been hacked?
Can I remain safe and secure using a free VPN?
Having tested many free and freemium VPNs in the past, I have found that, unlike the freemium VPNs, the security features provided by the free VPNs are not up to industry standards — making it much more likely for cyber-attacks to occur.
Protect Your Data From Potential Hackers With a 256-Bit Encrypted VPN
If you’re looking to stay safe online, you need a forward-thinking VPN that uses military-grade encryption to deter hackers. AES 256-bit encryption significantly reduces the chances of hacks by using almost uncrackable and uniquely long encryption keys. However, you must consider additional security features to optimize your security, including RAM servers, automatic kill switches, and DNS leak protection.
To avoid hackers and keep your data secure, you need a premium VPN like ExpressVPN to combine features, security, and efficiency. If you want to stay safe and secure while using the internet, download ExpressVPN risk-free with its 30-day money-back guarantee. If you aren’t satisfied, you can get a full refund as I did in less than 5 working days.













Leave a Comment
Cancel