Data Breach: Billions of Records Exposed in Online Trading Broker Data Leak
Ata Hakcil led the team of white hat hackers from WizCase in identifying a major data leak on online trading broker FBS’ websites. The data from FBS.com and FBS.eu comprised millions of confidential records including names, passwords, email addresses, passport numbers, national IDs, credit cards, financial transactions and more.
Were such detailed personally identifiable information (PII) to fall in the wrong hands, it could have been used in the execution of a wide range of cyber threats. The data leak was unearthed as part of WizCase’s ongoing research project that randomly scans for unsecured servers and seeks to establish who are the owners of these servers. We notified FBS of the breach so they could take appropriate action to secure the data. They got back to us a few days later and secured the server within 30 minutes.
What’s Going On
Forex, a portmanteau of foreign currency and exchange, is the process of converting one currency into another for a wide range of reasons including finance, commerce, trading and tourism. The forex trading market averages more than US$5 trillion in daily trading volume. Forex trading may be dominated by banks and global financial services but, thanks to the Internet, the average person can today dabble directly in forex, securities and commodities trading.
In the rush toward online trading though, users have entrusted terabytes of confidential data to online forex trading platforms. With financial transactions being at the core of forex trading, the nature of user data held in these trading databases is highly sensitive. This has made online trading sites a lucrative target for cybercriminals.
FBS, a major online forex trading site, left an unsecured ElasticSearch server containing almost 20TB of data and over 16 billion records. Despite containing very sensitive financial data, the server was left open without any password protection or encryption. The WizCase team found that the FBS information was accessible to anyone. The breach is a danger to both FBS and its customers. User information on online trading platforms should be well secured to prevent similar data leaks.
Who is FBS
Founded in 2009, FBS is an international online forex broker with more than 400,000 partners and 16 million traders spanning over 190 countries. It is one of the most popular online trading brokers in the world. The FBS app for the Android OS has been downloaded more than one million times on Google Play Store as of January 2021.
So large is the number of traders on FBS that every 20 seconds, an FBS client submits a request to withdraw their profit. An official trading partner of soccer giants FC Barcelona, FBS clients rake in half a billion dollars in profit each year. While FBS operates worldwide through its platforms FBS.com and FBS.eu, the company’s primary offices are in Belize and in Limassol, Cyprus.
FBS’ Comment: “[…] this large amount of logs mostly consists of technical services records and do not include any user-related records. It in no way reflects the number of users. One service generates hundreds of records on every execution and each user calls dozens of services. Thus, total amount of logs and the number of records have no connection to the number of users or user-related records.”
What Was Leaked?
Nearly 20TB of data was leaked comprising more than 16 billion records. According to our estimations, millions of FBS users spread across the world were affected. Leaked information included the following:
PIIs such as
- Names and surnames
- Email addresses
- Phone numbers
- Billing addresses
- Country
- Time zone
- IP addresses
- Coordinates
- Passport numbers
- Mobile device models
- Operating system
- Email sent to FBS users
- Social media IDs including GoogleIDs and FacebookIDs
- Files uploaded by users for verification including personal photos, national ID cards, drivers licenses, birth certificates, bank account statements, utility bills and unredacted credit cards
User ID and Credit Card Photo Uploads


User details such as
- FBS user ID
- FBS account creation date
- Unencrypted passwords encoded in base64
- Password reset links
- Login history
- Loyalty data including loyalty level, level points, prize points, total money deposited, active days, active clients, points earned and points spent
A German User’s Account

An Australian User’s Account
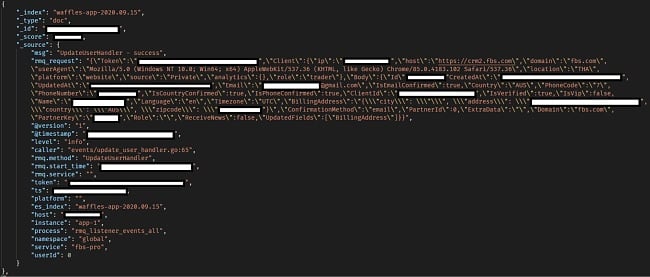
Plain Text (base64) Passwords
Financial details such as
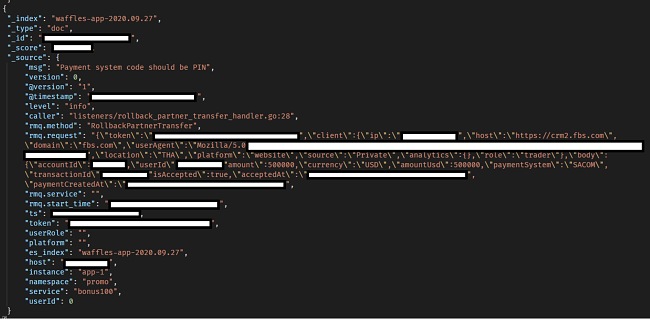
- User transaction details including deposited money, currency, payment system, transaction IDs, account IDs, transaction dates, number of times money was deposited, last deposit amount, last deposit date, total deposit, credit, balance, last month’s balance, interest rate, taxes, equity and margin free. Some of the transactions are really large.
A $500,000 Transaction
Each data set would on its own provide valuable information for an attacker but combining all of them makes the threat much more formidable.
What Does This Mean for FBS and Its Users?
The primary threats for FBS and its users include the following:
1. Identity Theft and Fraud
The personal identifiable information (PII) exposed by the leak could be used in fraudulent authentication across other platforms. The names, email addresses, physical address, passport numbers, driver’s license numbers, national ID numbers, phone numbers, social media IDs, credit cards, photos, financial records, and more could allow bad actors to impersonate the owner.
2. Scams, Phishing and Malware
Leaked contact information may be used to launch scam, phishing and malware attacks against FBS users. The data could be the basis for establishing trust in order to encourage clicks, malware downloads and the availing of more confidential information. Armed with the sensitive authentic data, a cybercriminal will sound more credible when they request for information over the phone or email.
3. Credit Card Fraud
To complete a card payment, FBS asks users to upload a photo of both sides of their credit/debit card. With the images accessible to bad actors, it is not difficult for the information to be used to commit credit card fraud.
4. Blackmailing
With email addresses, physical addresses, social media IDs and financial records accessible, bad actors could target for extortion users who move relatively large amounts.
5. Personal Safety
With cyber criminals having access to not just your financial transactions on FBS but also your physical address and phone number, you or your home could be the target of a robbery or burglary. Your transactions may give criminals a hint of your financial status.
6. Business Espionage
With FBS user email addresses and phone numbers readily accessible, competitors could extract this information and use it to target and lure users to their own online trading platforms. Stolen source code and information on the site’s structure also makes it easier for third parties to clone the FBS website then make minor adjustments in accordance to their needs.
7. Account Takeover
The leak exposed password reset links. With access to such sensitive information, an attacker could easily take over the account of any FBS user as long as they knew the user’s email address. Also, with the plaintext password (encoded in base64) and knowing that many people reuse passwords across platforms, cybercriminals could attempt to use the password on other platforms and take over.
This list does not cover all the risks users and organizations are exposed to from the FBS breach. Cybercriminals are continuously exploring new ways of using confidential information for nefarious ends.
As an FBS User, What Should You Do?
Once you are aware of a breach, it’s vital that you move with speed and do the following.
1. Reach Out to FBS
WizCase discovered the leak on October 1st, 2020 and reached out to FBS on October 2nd. Subsequently, FBS secured the server on October 5th. Nevertheless, reach out to FBS if they have not contacted you about the breach already.
Recovering from the loss of your PII can be time-consuming and expensive. Often, when a company realizes they have suffered a data leak, they will offer assistance to their users and customers so as to minimize the impact of the breach. This may grant you access to services and products that you would otherwise have to pay for or require to go through a lengthy process to get. The services offered may include identity or credit monitoring.
2. Change Passwords and Enable 2FA
The FSB ElasticSearch database stored passwords in plain text encoded in base64. This makes them decipherable using readily accessible tools. You should not only change your FSB password immediately but also make it more complex. By including lowercase, uppercase, numbers and symbols. If you used the same password on other platforms or apps, make sure you change these as well. Avoid reusing passwords.
If the website you are using doesn’t have a 90-day password change rule, make it a habit of manually changing yours every 90 days. Where the platform has the option of two-factor authentication (2FA), opt in. With two factor authentication, bad actors will be unable to log in with your credentials even if they have the password.
3. Check for Fraudulent, Unusual Activity
If you have sent a picture of your card to FBS, notify your bank or card provider immediately that your card details have been compromised. Most cards have a toll-free number on the back. Ensure you speak to a human representative. The card provider or bank will cancel the card right away and, if you want, issue a new card.
Keep an eye on your financial statements for unusual and fraudulent activity. Most card providers and banks have an email or text alert service to inform you when a transaction occurs. However, have your own routine such as checking your statements regularly. Do not just look for large payments or withdrawals. Some criminals will opt for multiple small transactions as these are less likely to raise eyebrows.
Contact credit reporting bureaus and have them place a fraud alert on your name. Sign up for an identity- or credit-monitoring service to monitor usage and changes in your personal or financial information.
4. Do Not Open Suspicious Links or Attachments
With your email address potentially in the hands of criminals, you should brace for a flurry of phishing emails and malware-laced attachments. If you receive an unsolicited email from someone you have not engaged with before, do not click on the links or attachments therein. Opening the link could send you to a fraudulent website that dupes you into sharing even more confidential information with the criminals. And clicking on the email attachments could download malware on your personal device or onto the network of the organization you work for.
5. Do Not Share Confidential Information via Phone or Email
Bad actors could use the data they extract from the FBS leak to send out emails and make phone calls to users. Do not share any personal confidential information you are requested for over email or the phone. If you think the request could be authentic, contact the company first via their official phone numbers.
6. Use VPN
The FBS data leak included user IP addresses. These could be used to track the person’s location. You can mask or change your IP address by using a virtual private network (VPN). This creates an encrypted tunnel between your device or browser on the one hand, and online platforms or apps such as FBS on the other. That way, anyone who does stumble on your IP address saved in the FBS database cannot tell your exact location.
7. Install Antimalware
Install antimalware software to preempt malware attacks as well as clean up any viruses, Trojans and spyware that may have already been downloaded onto your device. Many anti malware applications will also alert you when you are about to open a suspicious link or visit a malware-infected web page. The applications will also scan your emails for signs of phishing. If you already have anti malware installed, make sure it’s the latest version.
8. Personal Safety
Just because the data leak occurred in cyberspace does not mean the risks to you are solely virtual. The FBS data leak included information such as physical address, phone numbers in addition to financial transactions. Criminals could profile users who seem to transact large amounts and target them for burglary or extortion.
Since moving houses would be impractical for most people, install or bolster your home security system. Fit cameras at strategic locations to pick up any suspicious activity that is unfolding around your home in recent times.
9. Beware of What You Share
Beware of what information you share with not just FBS but any other online platform or mobile app. Go for the bare minimum and only provide the information that you need to. Any field on the registration or transaction form that is not marked as mandatory should be left blank. If you are requested to upload photos of your ID, driving license, credit card and other sensitive personal information, redact the information that is not relevant for the company and only expose your full name and limited details that wouldn’t harm you if they were ever leaked.
That way, you will minimize the risks if your profile information is exposed following a data leak. Log into your FBS account and delete any profile information that is not mandatory.
Why Should You Trust WizCase?
WizCase is a widely popular web security platform offering advice and tips for thousands of readers every week. Translated into over 30 languages, our website has gained the trust of a wide number of people worldwide. Our team regularly discovers new data breaches across the internet and contacts them to companies responsible for them prior to publishing any reports. We have found links on websites and in databases relating to news websites, popular dating apps, and the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel