Data Breach: Millions of Dating App Records, Messages, and User Profiles Exposed in Data Leak
WizCase’s security team has recently uncovered breaches in 5 different dating site and app databases. These leaks have compromised user data, including sensitive and confidential information like real names, billing addresses, email addresses, phone numbers, private messages, and more. The total number of leaked entries is in the millions. Every server was easily accessible via the internet and not password protected.
This information was uncovered as part of investigations to help companies keep their data secure. As such, the companies involved and their hosting providers have been contacted so that they could secure their databases and keep user data private. Prior to this discovery, WizCase also uncovered another dating app leak which was promptly closed after the appropriate authority was notified.
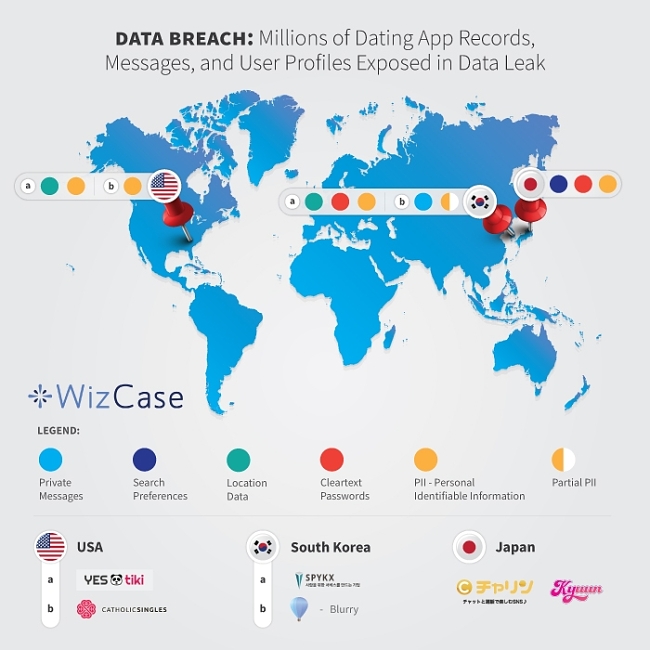
Breaches Found: July 2020
- CatholicSingles.com — USA — 50,000 entries detailing real names, billing addresses, email addresses, and other private user data.
- SPYKX.com — South Korea — Approx. 3.7k user profiles and ~120k GPS data entries.
- YESTIKI.com — USA — Approx. 4.3k entries with user information, activity logs, and more.
- Blurry dating app — USA — Approx. 77k private user messages exposed.
- Charincharin.net and kyuun-kyuun.com — Japan — Approx. 102 million entries including email addresses, mobile device info, and search preferences.
What Data Got Leaked?
Our team found servers for 5 dating sites and apps around the world.
1. CatholicSingles.com — A dating site for Catholic people in the US
- Country: USA
- Database size: 17MB
- Exposed records: 50,000
- Server type: Amazon Bucket
- Data exposed: User’s real names, email addresses, phone numbers, billing addresses, and more.
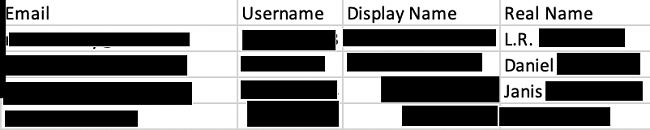
CatholicSingles.com is a dating site for users who are looking to find faith-based partnerships. The site operates exclusively in the US.
The leaked user data included very sensitive information, like real names, email addresses, billing addresses, phone numbers, age, gender, occupation, and education. Also found was data detailing hair and eye color, payment methods, and activity levels (like days since last login). Many user profiles are banned or canceled, but the most recent login discovered was 2019. These users could still be active.
2. SPYKX.com — (Congdaq/Kongdak app) Online dating for users in South Korea
- Country: South Korea
- Database size: ~ 600MB
- Exposed records: ~ 123,000
- Server type: ElasticSearch server
- Data exposed: User emails, phone numbers, cleartext passwords, GPS data, and more.

SPYKX.com is the creator of the Congdaq/Kongdak dating app for individuals in South Korea. It appears that the online dating app is just one service the site has created.
Data on the server included user data like email, cleartext passwords, phone numbers, date of birth, gender, and education. GPS data was also discovered which could potentially be linked to individual users via their internal IDs.
3. YESTIKI.com — Dating app hosted in the USA
- Country: USA
- Database size: 352MB
- Exposed records: ~ 4,300
- Server type: MongoDB server
- Data exposed: User’s names, phone numbers, GPS locations, and more.
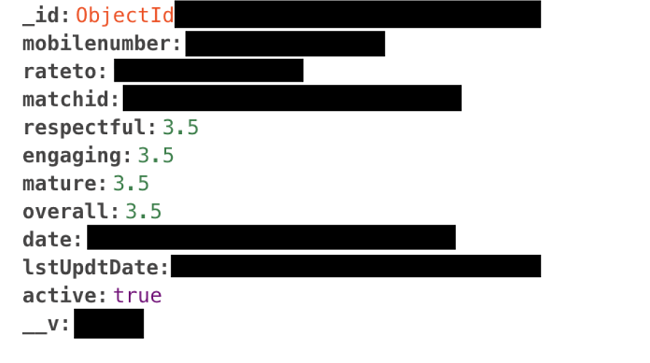
YESTIKI.com is a dating app for users in the US, which appears on the app store as TIKI Interactive. It enables users to meet potential partners through exploring shared interests and activities.
Leaked data from the MongoDB server included phone numbers, names, address and GPS location data of date venues, user ratings, activity logs, Foursquare secret key IDs, and more.
4. Blurry — Dating app from hyperitycorp.com
- Country: South Korea
- Database size: ~ 367MB
- Exposed records: ~ 70,000
- Server type: ElasticSearch server
- Data exposed: Private chat messages that included PIIs, like Instagram usernames and WhatsApp numbers.
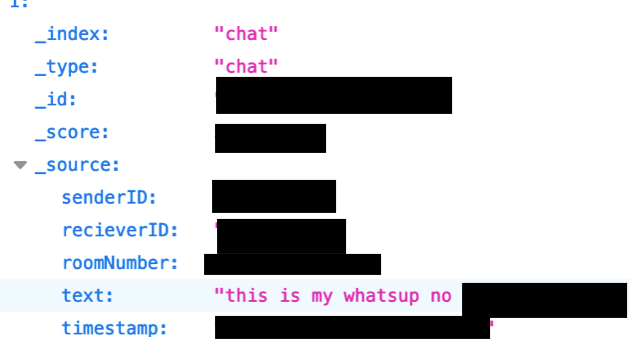
Blurry is a dating app from Korea with users around the world. It has over 50,000 installs on the iTunes app store, so while it’s quite small still, a considerable amount of sensitive user data was breached.
All data recovered from the server involved private messages sent between users on the app. While there are no significant PII’s (Personally Identifying Information), personal information could potentially be correlated with internal IDs. Some messages were discovered containing personal information like Instagram handles and phone numbers.
5. Charin and Kyuun — 2 dating apps for users in Japan
- Country: Japan
- Database size: 57GB
- Exposed records: ~ 102,000,000
- Server type: ElasticServer
- Data exposed: User email addresses, cleartext passwords, user IDs, search preferences, and more.
Charin and Kyuun are two different dating apps from what we suspect is the same company. Both websites are very similar in design and are sitting on the same EC2 Amazon server. Leaked data from both apps was found on the same breached server.
The most notable data found on the server includes email addresses and passwords, both hashed and cleartext. Other data found was user IDs, mobile device information, and search preferences such as distance and age.
Unverified Server Leaks: 6 Additional Servers Without Owners Found With Dating App User Information
During investigations, the WizCase security team found an additional 6 unsecured servers with information from different dating apps and sites, separate from the breaches above. The owner/s of the servers have not yet been identified, making it difficult to know where the data originated from.
This information could’ve been collected through a process known as web scraping, but this could only explain some of the data, as parts of it do not appear to be from internet-facing web pages.
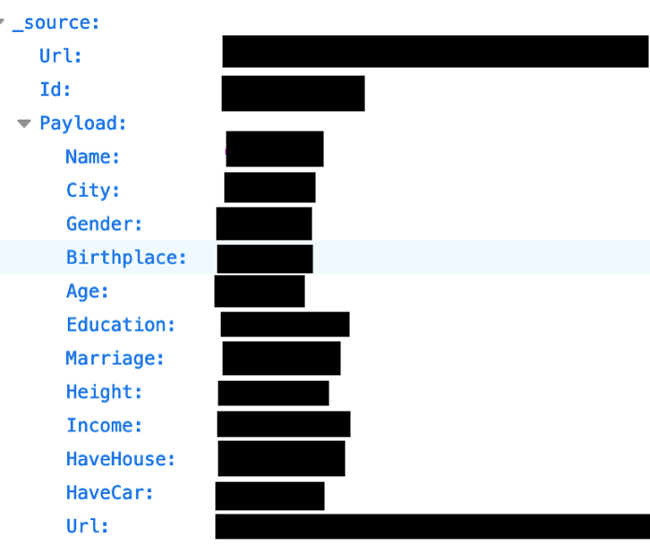
Which Dating Apps or Sites is the Data From?
Data was found relating to several different dating apps and sites: Zhenai, Say Love, Netease, Love Chat, and Companion. While a lot of the information isn’t exposing personal data, there’s a potential for it to be correlated with other information in the future, making it personally identifiable.
What is “Web Scraping”?
Web scraping is an automatic process that allows information on websites to be collected and stored. Web scraping isn’t just for websites though — it can also be used for other protocols and technologies. For the most part, this is a legal process, although it does have some gray areas and can be illegal if used in the context of other illegal activities.
It appears that a lot of the information discovered on these servers could be the result of web scraping. Much of the data is information that can be viewed online without needing password access, or “web-facing data.”
What are the Risks for Users?
Users of dating apps and sites may assume that their information isn’t easily accessible or made public, when in fact it is. Zhenai, for example, allows a lot of user information to be seen without a user logging in. Individual users may not want their dating profiles to be public but have no control over how the site protects its information.
Web scraping is also related to a part of the hacking process (gathering information) and getting all the data from a server may pose security risks to users and to the site or app itself.
What are the Consequences of a Data Leak?
Identity Theft
This is a huge risk with databases that hold complete PII (Personally Identifiable Information) records. If a scammer can get a dating app user’s full name, address, and date of birth, it’s easy for them to steal an identity and use it for fraudulent purposes. If an attacker has your password, they could try it on other platforms (users often reuse the same password across multiple platforms) and gain access to your PII that way. With this information, someone has the ability to create another account on a dating app and harass other users under your name.
Phishing, Phone Scams, and Catfishing
Once a scammer has your contact details, they can use other information discovered in the data leak to convince dating site users to give up more information on the phone or by clicking on a suspicious email link. These scams work because users believe their information is secure and scammers can use the exposed personal information to establish false trust. With your personal details, a scammer could also set up a catfishing account using your information and images — potentially harassing family, friends, and other dating app users.
Blackmail
Users who want to keep their dating preferences a secret could experience blackmail as a result of data leaks. Scammers are aware that they could reveal private information and damage a user’s reputation, potentially costing them their relationships or financial security. Some individuals may be using dating apps while in a relationship or married — a scammer could use information from leaked conversations to threaten to expose users to their families.
Privacy and Stalking
With GPS data showing user locations as well as potential date locations, users are put at risk of stalking and other privacy issues.
Business Espionage
By collecting data on other companies, competing businesses have the potential to use data regarding users, registration levels, and targeting methods to their benefit or to sabotage others in the same field.
What Does This Mean for Data Leak Victims?
Depending on the kind of data leaked from each breach, the victims could be at risk in different ways. Here are examples of one risk per leak, although there can be more.
- Catholic Singles — Leaked email addresses and phone numbers put users at risk of phishing emails and phone scams.
- SPYKX — Exposed cleartext passwords and email addresses could let hackers access personal data kept on the account, leading to identity theft and fraud.
- YESTIKI — GPS data, venue addresses, and match dates and times make users vulnerable to stalkers.
- Blurry — Exposed messages may contain identifiable private data that could be used to blackmail users.
- Charin and Kyuun — Leaked data includes user search preferences and message content that can be used to blackmail victims who want to keep information private.
How Can You Keep Your Data Secure?
It’s always important to be vigilant about your personal data when you’re signing up to dating apps or other sites that ask for sensitive information. If you have an active dating profile on one of the above sites, we recommend that you re-evaluate the personal information you have available there.
We also recommend changing your password for any breached site and any other platform you use the same password on. It’s best not to reuse passwords at all, as this can make online accounts vulnerable in the event of a data breach. In general, try to use complex passwords that you find easy to remember (like four random words) or use completely random passwords and save them in a password vault. The best password is a password you can’t remember.
Take precautions when messaging via the apps and avoid divulging identifiable data such as your full name, social media profiles, phone numbers, or pictures. Once you’ve sent the information, it has the potential to be used for blackmail or other fraudulent purposes.
Be sure to check other sites and services you use online for suspicious activity, too. If a scammer has your personal information, they could use it to access other online accounts. Should you find anything unusual, don’t hesitate to report it.
Who is WizCase?
WizCase is at the forefront of cybersecurity. The cybersecurity team is made up of experts and led by Avishai Efrat, dedicated to ensuring that any leaks found are promptly secured. The security team contacts every company to inform them of data breaches, giving them the opportunity to secure their users’ data.
The team has found leaks in other dating apps and sites, as well as in the medical industry, the hospitality industry, and in popular webcam security.




Leave a Comment
Cancel