Universities’ Security Blindspot on Global Free WiFi Network Leaves Faculty and Student Usernames and Passwords Exposed to Hackers
WizCase’s security team, led by Ata Hakçıl has discovered a major security issue affecting the users of WiFi provider eduroam. Eduroam provides free WiFi connections at participating institutions assigning student, researcher, or faculty login credentials. Each institution gives time, manpower, and other resources to help keep eduroam running. Unfortunately, since there is no one person in charge of maintaining the system in each university, a simple misconfiguration could make it the target of hackers who would be able to spoof the network and capture users’ login IDs and passwords — potentially giving them access to confidential or personal information, and more.
What’s Going On?
By the end of 2020, the Wizcase security team was able to chain multiple issues affecting the configuration of the eduroam network. This discovery uncovered the potential for ill-intentioned hackers to capture eduroam WiFi networks’ user credentials, and maybe more.
The team went over various configuration setup guides and set up a test environment with various attack scenarios. Our research showed that in most of the universities with misconfigured networks, it is possible to configure an “evil twin” eduroam network that would be indistinguishable from the real one on certain mobile devices. This could result in these devices automatically sending their stored credentials in order to connect to the evil twin WiFi network for users not using eduroamCAT (eduroam’s catalog application which handles certificate checks).
It is important to note that the exposure isn’t due to a technical vulnerability from eduroam’s services/technology but from wrong configuration instructions given to users by the admins of each university. We contacted eduroam on December 2020 to disclose our findings and received their response the same day:
“Thank you for your additional comments. We are indeed occasionally made aware of eduroam Identity Providers who do not follow the requirements of the eduroam policy, and leave their own users unprotected. We are absolutely in line with your thinking that this is an unacceptable behaviour on their end.”
Following this reply, our team had decided to postpone the publication of their findings, hoping eduroam might have informed their users after our reach out.
How Did This Happen?
Eduroam is a worldwide roaming access service which first started growing in Europe. Eduroam allows students, researchers, faculty and staff members to obtain internet connectivity across different institutions by using their username and password from their own institution, which is useful for users who are participating from different campuses. Eduroam has roaming operators in over 100 countries and works in more than 3000 universities and other institutions around the globe, with hundreds of thousands of users.
Our discovery disclosed that the connectivity to the network includes different stages of authentication which rely on each other, and currently some of them aren’t implemented properly in some universities.
In general, the majority of the WiFi networks that allow users to connect with their credentials instead of a shared key are using a system called “Extensible Authentication Protocol”, or EAP. Eduroam is one of the networks using EAP, which relies on each user having their own username and password to access the WiFi network.
EAP’s authentication works in multiple sequential phases, and each phase relies on the previous one to be implemented or applied correctly in order to be secure. And often, the last stage of this authentication which is called “Inner Authentication” is done via one of the two following methods:
Plain Authentication Protocol (PAP): This method transfers the credentials of the users to the authentication server in plaintext, because it relies on the “Outer Authentication” to completely encrypt the traffic using a “Server Certificate”. We discuss details about encryption certificates below.
Microsoft Challenge Handshake Authentication Protocol v2 (MSCHAPv2): This method recognizes there may be failures in the “Outer Authentication” stage, and transfers the password in a hashed, non-plaintext form.
However, not every operating system implements this certificate check properly, Android being one of those operating systems. When a network with the same WiFi name appears, Android devices will not check whether this certificate is trustworthy or not, and will not even notify the user about the certificate before connecting. When auto connect is enabled for a network using a Server Certificate, Android devices will automatically attempt to connect to this network and send your stored credentials, without ever checking the legitimacy of the certificate, or letting the user know anything might be wrong.
Even when the operating system implements this check properly and asks the users if they want to continue with an untrustworthy certificate, the majority of the users don’t know what certificates do and opt to continue with the connection.
To our knowledge, iOS devices do not allow connections to EAP networks without installing the EAP configuration file which enforces the validity of the server side certificate, and is not vulnerable to this issue. However, this step is neglected in many university guides when connecting from Windows or Android devices, and users are encouraged to connect directly without checking the certificate instead.
What is a Certificate?
For your traffic to be completely secure, both the server and the client must prove their authenticity so that neither party can be impersonated. A certificate is just for that, it is the public key component of the asymmetric cryptography process. It is how a server authenticates its legitimacy to its clients, and it is what clients use to encrypt their traffic so that only the server can decrypt it.
One critical part of this authenticity process is knowing if the certificate you received is really coming from the system you think it is coming from. If a device fails to evaluate the authenticity of the certificate, anyone could send a certificate that they have the key for, and decrypt your messages.
This critical issue above is applicable to websites using HTTPS, VPN servers, pretty much anything that is supposed to be encrypted between clients and servers. Using a VPN will not prevent the attack, but it can help prevent an attacker from going further. Using a VPN would prevent the attacker from being able to snoop through the users’ personal information.
In our case, this is the very oversimplified version of how EAP network communication is done.
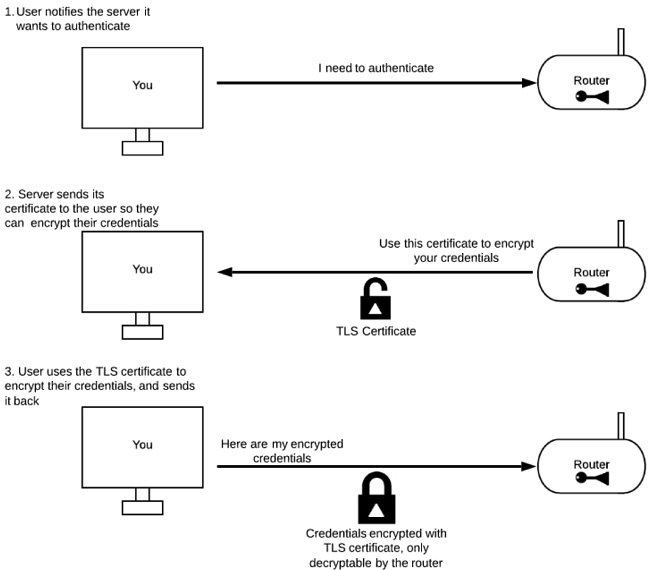
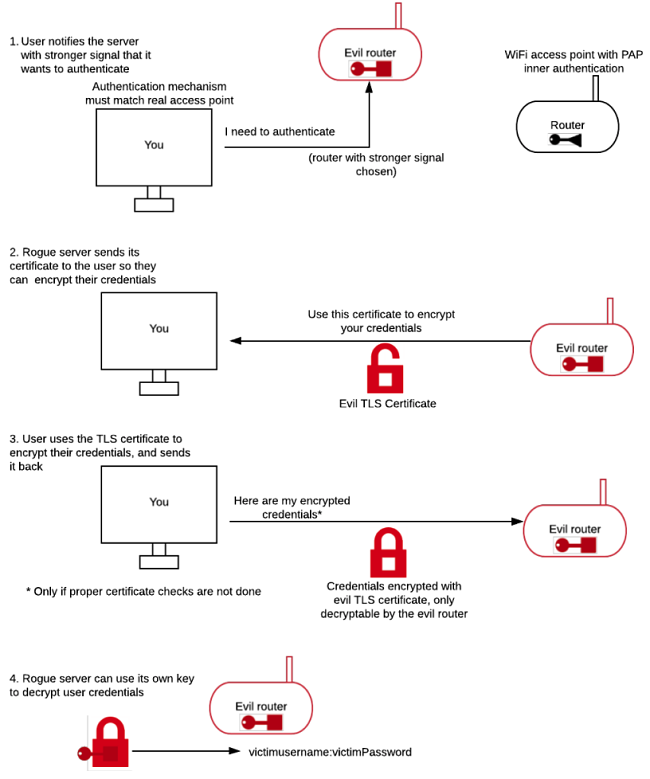
But if users don’t know why the validity of a certificate is important, if they are instructed by guides to accept any certificate, or if in some cases (like Android devices) they are not even warned about certificates and the operating system accepts every certificate, a bad actor can intercept and steal people’s passwords.
Here is how the exact same scenario would be, if MSCHAPv2 was preferred over PAP.
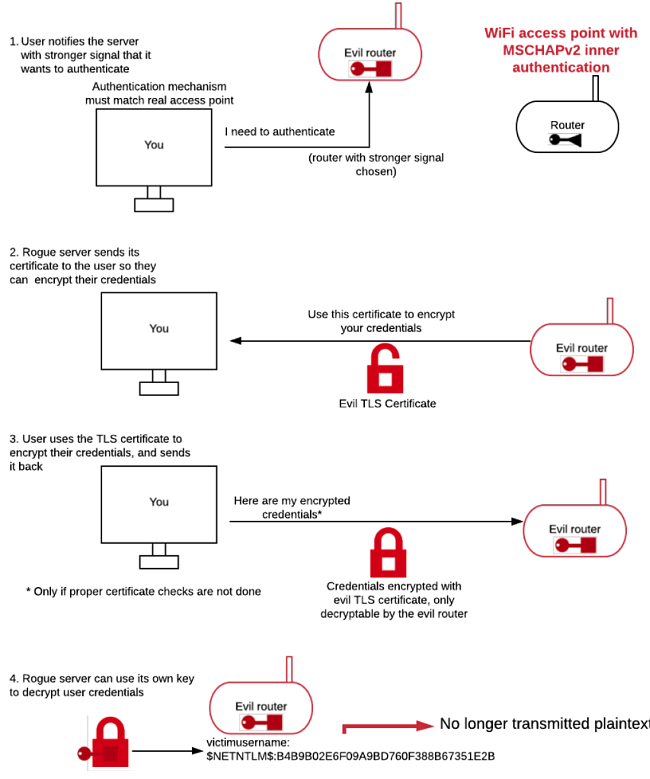
Since the user has set up their network details to match the routers, they have chosen “MSCHAPv2” for the inner authentication phase. They are no longer sending their credentials in plaintext, but they are sending it in hashed format instead. Even though an attacker is able to access these hashed credentials, there is an extra layer of mitigation since the attacker no longer has the plaintext password and has to crack the hashed credentials instead.
Who Is Responsible?
It’s impossible to point fingers or assign blame to any one person, institution, system, or process. The issue has snowballed into such a critical state that it is clear there are multiple companies and organizations who have played a part.
For most of the cases, it’s the University IT departments who make the final decision in the environment’s configuration, and they often pick the PAP method which enables this issue because it is easier to set up and maintain. To the best of our knowledge, Eduroam provides universities with the necessary configuration materials to properly set up the network, but many universities do not realise the significance of certificate validity and don’t reflect it to their setup and their connection guides. Yet, we believe that if these had been mentioned more directly, it might have significantly reduced the number of users affected by this common misconfiguration.
On a different note, executing this attack is not as convenient for computers and iOS devices as it is with Android devices, because they will recognize the invalid certificate of our “evil” network, and display a warning similar to the one below:
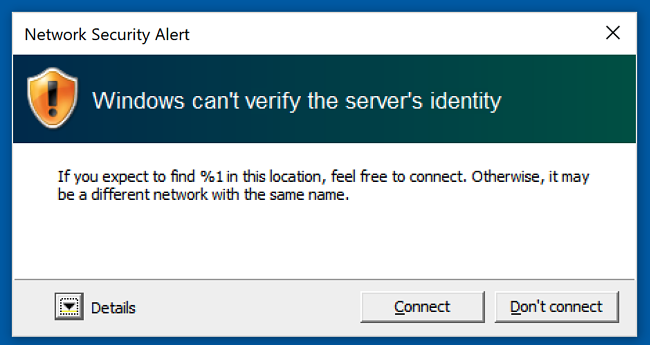
However, during our investigation, we found that lots of universities’ own certificates are invalid, which meant users were getting this exact same error the first time they were connecting to the network.
When universities are using invalid certificates, often their connection guides refer to this step and tell users to just disregard this error and accept the certificate, which could reinforce the idea to “Always accept this error” to users who do not know why it happens.
Who’s at Risk and What Are the Consequences
Any students or faculty members using eduroam or similar EAP based WiFi networks in their faculties with the wrong configuration are at risk. If you are using an Android device and have eduroam WiFi set to auto-connect, malicious people could capture your plaintext username and password by only getting in 20 or so meters in range of you.
Following map shows all of the universities using eduroam, and if their configuration was secure or not before our disclosure to eduroam in late 2020. We’ve used publicly available information to compile the map.
Out of over 3100 university configurations we’ve reviewed, more than 1500 allowed connections with the PAP method, and about 600 of them allowed only the PAP inner method, which could give an attacker plaintext passwords if the certificate setup was misconfigured. Universities not offering the PAP method are marked green, while universities offering PAP with alternatives are marked yellow, and universities only offering the PAP method are marked red.
Phishing Scams and Malware
Since most of the students use a single password for WiFi, their university emails, and anything else related to university, this could give attackers access to your email or the email account of anyone in your university, within your WiFi range. Always be skeptical when viewing email, even if it is from someone who you trust.
Account Takeover
With access to your username and password, attackers could take over your accounts using the same or similar credentials, and it could be a hassle to get those accounts back. If your school email address or any other accounts share the same username and passwords, attackers could easily compromise those accounts to either steal your private stuff, or use your accounts to impersonate you.
Framing & Espionage
After stealing your password, bad actors can login to the eduroam network with your credentials and even copy your MAC address so their traffic is indistinguishable from yours. If they commit any illegal activities, or have any shady traffic that catches the attention of university administration or their upstream ISP, they might trace it back to you and take legal action against you.
What Can I Do to Protect Myself ?
For starters, you could notify your school administration about this issue to get it fixed, and for the time being, you could disable automatically reconnecting to eduroam on your mobile device to mitigate this issue.
After capturing your credentials, attackers could also let you connect so that they can view your traffic, instead of immediately dropping the connection. Using a VPN encrypts your traffic and would make it impossible for attackers to see it.
Also, remember that even if your university has eduroam properly configured, you might be exposed when in exchange with another university which suffers the misconfiguration.To make sure you are safe, you do not have to follow that university’s connection guide – you can find the correct certificate for the university you are roaming to, and enforce it for your device.
As a student/faculty member using Android device
The easiest way to mitigate this issue for yourself is to remove the stored credentials for the eduroam network from your WiFi settings, and install eduroamCAT. This will install the correct EAP profile for your university to your device, and ensure that the certificates match.
If you can’t connect to the network with eduroamCAT, it could indicate that configuration files shared with the eduroam catalog and the actual configurations your university is using might be conflicting. You can contact your university so that they can update the configuration files, and until then, you can use eduroam normally by disabling the ‘auto reconnect’ checkbox which would make it harder for attackers to steal your credentials.
As an IT Employee/Sysadmin
If you are in a position where you have a say in your university’s infrastructure, you should apply to participate in the eduroamCAT program, which requires you to correctly install a certificate and enforce it. You can also consider abandoning the PAP method for the sake of MSCHAPv2, which mitigates the impact of similar issues, and has no significant downsides to the PAP. We also suggest making sure your university reaches out to the users and helps them with the steps mentioned above.
How Can I Know If I Have Been Affected
If someone just captures your credentials and never uses them to login to your accounts, there is no good way of knowing if your credentials were compromised or not. However, if you suspect someone else is using your school account, contact your school’s IT department, and ask them if they can give you the access logs for your email account, which should show all the IP addresses and times you logged in to your account. Regardless, we recommend changing your passwords and use different ones for each account in the future.
Why Should I Trust Wizcase?
WizCase is a widely popular web security platform offering advice and tips for thousands of readers every week. Translated into over 30 languages, our website has gained the trust of a wide number of people worldwide. Our team regularly discovers new data breaches across the internet and contacts them to companies responsible for them prior to publishing any reports. We have found breaches affecting many different companies from learning platforms, news websites, popular dating apps, and the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel