Over a Hundred Thousand People’s Personal Information Exposed in Colombian Real Estate Company Data Breach
WizCase’s security team recently found a major breach affecting the online database of Colombian real estate development firm, Coninsa Ramon. The breach exposed clients’ names, photos, addresses, and more. Our team estimated that the breach affected over a hundred thousand people. There was no need for a password or login credentials to see this information, and the data was not encrypted.
What’s Happening and Who Is Involved?
Our team of ethical cyber researchers, led by Ata Hakcil, found a vulnerability in a database owned by Coninsa Ramon. Coninsa Ramon is a major real estate development firm in Colombia. The company specializes in architecture, engineering, construction, and real estate services and serves both individuals and companies in various sectors in Colombia including: housing, commerce, industry, institutional, and infrastructure. The breach was caused by the misconfiguration of an AWS S3 bucket that contained over 5.5 million files, totalling over 1TB of data. We reached out to the company, but did not receive a reply so far.
What Data Was Exposed?
The misconfigured bucket exposed data from the company, as well as personal identifying information (PII) from an estimate of over 100,000 customers. Most of those customers were individuals but some were companies. The data found in the bucket was mostly invoices, but it also contained income documents, quotes, account statements, and readjustment documents. All the documents were dated between 2014 and 2021.
These documents exposed customer information such as full names, phone numbers, emails, home addresses, amounts paid for estates, and asset values. The misconfigured bucket also contained a database backup that exposed additional details such as profile pictures, usernames, and hashed passwords. However, it does not appear that any credit card or bank information was exposed.
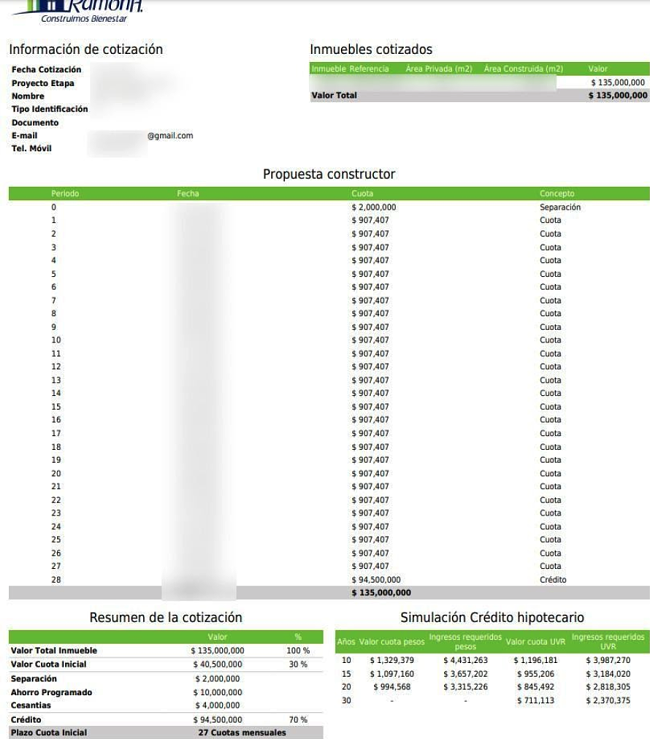


In total, the breach exposed 1.12TB of data, containing over 5.5 million documents.
Based on viewing a sample of the documents, our team estimates that the misconfiguration revealed US$140 billion to US$200 billion in transactions, or an annual transaction history of at least US$46 billion. For perspective, that’s roughly 14% of Colombia’s total economy.
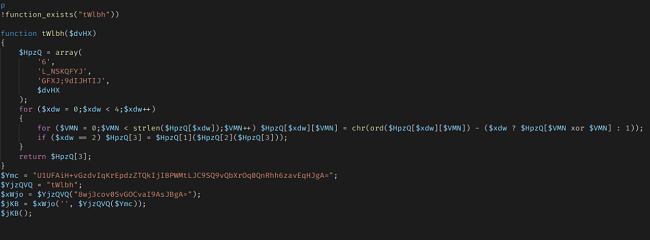
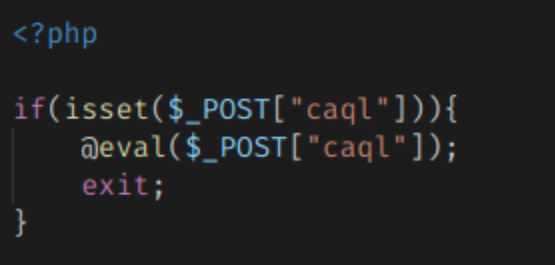
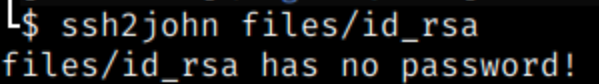
The bucket contained further information regarding the company’s internal services and exposed weaknesses with poor encryption. Additionally, our security team found multiple forms of malicious, backdoor code in Coninsa Ramon’s website. Backdoor files uploaded to the website could give bad actors persistent access to the website’s backend. It could allow them to modify the website and even add their own fraudulent pages to it.
Our security team confirmed the existence of these malicious files in the misconfigured bucket, but we cannot confirm if the files were ever used.
What Are the Risks and How to Protect Yourself?
If discovered by ill-intentioned hackers, this breach could have exposed many of the company’s clients to various forms of scam and fraud. If you have conducted business with Coninsa Ramon between 2014 to 2021, be extra cautious about the following risks.
Phishing: Due to the large amount of personal identifying information (PII) exposed, the company’s clients could be targeted by phishing scams. For example, con artists may try to appear as employees of Coninsa Ramon and contact clients to get money or more information. This may appear especially convincing due to the specific PII concerning location and purchasing data. If you are contacted by someone from Coninsa Ramon, be sure to double-check the contact through someone you already know at the company or by contacting the company through official, known channels.
Fraud & Scams: Using the PII from the breach, bad actors could conduct a variety of fraud or scam acts. For example, bad actors could use the knowledge of past transactions to trick users into making additional payments, or they could change where the payments go. In future practice, be sure to limit personal information you share with companies as much as possible.
Website alterations: As mentioned in the previous section, we uncovered malicious code in the Coninsa Ramon website. This could allow bad actors to modify the website and even add their own pages in order to trick victims into offering more PII or sending payments to the bad actors. Try to first confirm purchases and exchange of PII through confirmed contacts with Coninsa Ramon via phone or email.
Attacks on Coninsa Ramon’s business: The website vulnerabilities also put the company at risk of ransomware attacks which could temporarily harm the company’s operations or website.
For future purposes, we recommend always inputting only the mandatory fields when making a purchase or setting up an online account. The less information hackers have to work with, the less vulnerable you are.
Unfortunately, the above list is not comprehensive, and cybercriminals are always generating new methods to exploit anyone vulnerable on the Internet.
Though most email clients have methods to block spam and phishing attempts, they are not 100% effective. When receiving an unexpected email from a seemingly trustworthy source, do not open any attachments. Phishing emails often use scare tactics to force users to open the attachment. If you are ever unsure about an email from a trustworthy company, give them a call. This will usually let you verify whether the attachment is legitimate or not. A good antivirus program can also aid in protection from malware, trojans, and other dangers.
We recommend users use different passwords for each unique account. This way, security breaches such as this one don’t result in multiple accounts being compromised. It is also good practice to change your password every 90 days.
Why Should I Trust Wizcase?
WizCase is a widely popular web security platform offering advice and tips for thousands of readers every week. Translated into over 30 languages, our website has gained the trust of a wide number of people worldwide. Our team regularly discovers new data breaches across the internet and contacts them to companies responsible for them prior to publishing any reports. We have found breaches affecting many different companies from news websites, popular dating apps, and the medical industry. Together, we’re working hard towards creating a safer online environment for everyone.




Leave a Comment
Cancel