Data Breach: Student Data Compromised in Leak Involving Libyan Ministry of Education
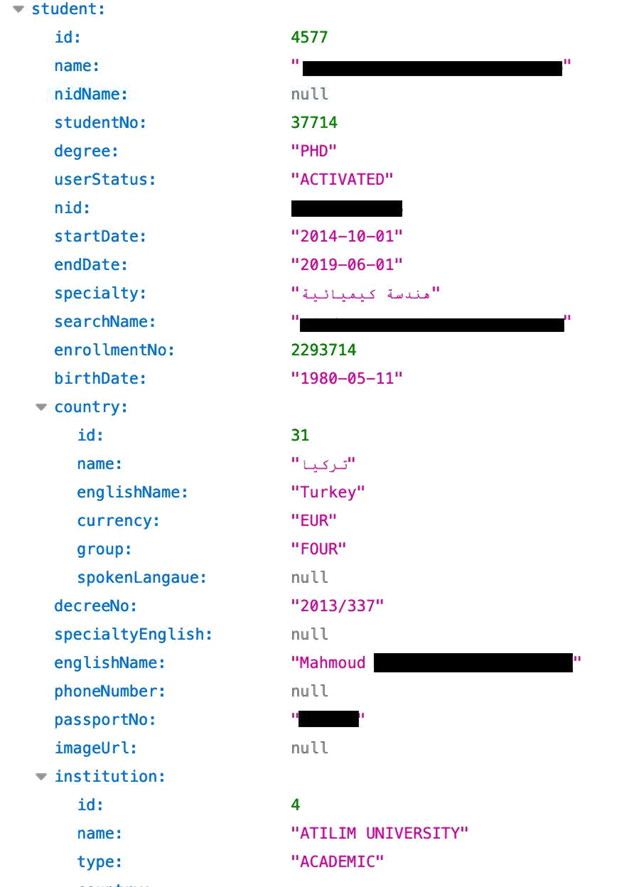
WizCase has recently found an open Elasticsearch database from the Libyan Ministry of Education. The server contained 2GB of data with PIIs, including full names, passport numbers, photos, email addresses, and more from more than 55,000 exchange students from around the world.
What’s Going On?
The WizCase web security team, led by Avishai Efrat, discovered a 2GB data leak originating from the Libyan Ministry of Education. The server, which is hosted in Germany and uses an Elasticsearch engine, contained personal details for over 55,000 exchange students from around the world.
The Libyan Ministry of Education has a program that assists students in finding suitable exchange programs. It’s these students whose data was compromised in the data leak.
The leaked data included:
- Full Name
- Email address
- Passport and ID numbers
- Date of Birth
- Photos
- Degrees
- Country of Origin
- Destination Country
- Marital Status
- Phone Number
- Thesis Details
- Transfer approval decision
- Start and end dates of the educational programs
- Tuition Costs
- Scanned copies of formal letters directed at the students
- Student Information (student number, user status, start & end dates, etc.)
- Employer
Whose Data is Available and What Are the Consequences of Such a Leak?
The students who took part in this program weren’t necessarily going to university in Libya. The Ministry of Education in Libya supports college and university scholarships around the world. The students that were found in this link are presumably part of this program.
The data that we found is connected with students from all over the world. You can see in the list below some of the major countries that were connected with the leak. Based on the data, the students are either originally from these countries or it’s the location of their transfer.
- UK
- Egypt
- Turkey
- USA
- Canada
- France
- South Africa
- Australia
By not securing their Elasticsearch database the Libyan Ministry of Education has opened the students up potentially severe online attacks, not to mention the complete lack of privacy.
Some of the documents that we found included whether a student was accepted or rejected from the program, Letters in Arabic that contained full PIIs of the students, letters that didn’t include any PIIs but discussed the current status of extending or rejecting a Ph.D., tuition costs, and more.
Students who are in the database are susceptible to a variety of both online and real-life attacks. These include, but are not limited to:
- Identity Theft: All the data a scammer or a hacker would need to commit identity theft, such as a passport number, was easily accessible in this leak. One possible scam would be for a hacker to use the student’s name and make a grant request. The grant money would then be routed to the scammer instead of the student.
- Phishing: A scammer could have enough information with the passport number, student ID number, level of education, or whether they were accepted in the program to write a convincing phishing email. This can be used in an attempt to get additional valuable information out of them. This will increase the chances of the victims to follow phishing links in the attacker’s email.
- Catfishing: Once the hacker gets access to all this private data, it would be easy to create a fake identity on a social network and try and gain the trust of others, while posing as a friend or acquaintance.
- Phone Call Scams: Student phone numbers were available in the leak. This gives scammers an easy opportunity to combine that with all the other leaked data and attempt to extort or trick the student into providing sensitive data.
How Did This Happen and What to Do Now?
The website that the Libyan Ministry of Education uses for its student portal had an unsecured Elasticsearch database storing all of the information. By default, Elasticsearch doesn’t automatically activate password authentication when it is installed, and no one at the Ministry of Education adjusted the default settings.
Servers of this sort should also never be exposed like this, with no IP whitelisting and authentication mechanism – they’re originally built to be kept within internal network perimeters. Furthermore, the logging of cleartext private information such as what was in this leak should be reconsidered.
If you’re a student who participated or is participating in this program you should be on the lookout for emails with suspicious links or phone calls asking for account information or other private details. You should also be vigilant in checking your online accounts for any suspicious or unusual activity.
As a general rule, it’s always recommended to use a reputable antivirus program and a VPN to protect your private data, and keep malware, phishing attacks, and other cyber-attacks from successfully attacking your computer. If you’re not sure a VPN is, or how it can help you, check out this VPN beginner’s guide for more details.
Who is WizCase and Why Should We Trust You
WizCase is a leading web security website that is available in 30 languages and reaches millions of readers per year. We have verified this data by randomly email addresses that we found and matching them up with social media accounts or other public resources. The names and details that we were able to see have all matched up.
Libya’s Ministry of Education didn’t respond to our inquiry, and so we contacted Libya’s Computer Emergency Response Team (CERT) which failed to reply as well. The hosting firm was reached out to and clarified that they could solely inform the customer about the situation, without the ability to address the problem directly. Finally, we have been in touch with Africa’s CERT which has reported the leak to the Libyan CERT directly, which in turn has contacted Libya’s Ministry of Education. We received an update on December 2nd from AfricaCERT that the leak is closed, and after testing the database we can confirm that it has been secured.




Leave a Comment
Cancel