Family History Search Software Leaks Users’ Private Data
Recently, WizCase has found a data leak affecting an open & unencrypted ElasticSearch server that belonged to Software MacKiev. The company, which currently maintains the Family Tree Maker software, syncs user data of a widely-known family history search platform, Ancestry. The leak exposed thousands of records with sensitive personal information, such as email addresses and user location. We contacted MacKiev to report the leak and even though we didn’t receive a response, the exposed database has since been secured.
What’s Happening?
Family Tree Maker (frequently referred to as FTM) appears to be the key stakeholder in the leaking database. The genealogy software was initially released in 1989, but it has since been passed from its original developer to Broderbund, The Learning Company, Mattel, and Ancestry.com, before reaching its current owner, Software MacKiev.
Our team of white-hat hackers, led by Avishai Efrat, found an exposed MacKiev server that leaked 25GB of Ancestry user data and MacKiev Software user subscription.
As the leak showed some logs from Ancestry.com, our research proved that there’s a clear link between the two companies. MacKiev was the company who had been responsible for developing the MacOS version of Family Tree Maker since around 2010, and acquired the Windows version of the software from Ancestry in 2016. Family Tree Maker features an Ancestry-inspired design and the ability to sync family trees with accounts and information from the Ancestry website.
We have notified Software MacKiev about the leak as soon as we were able to confirm the server’s owner. The database was closed shortly after, but we did not receive a response to our responsible disclosure.
What Data Has Been Exposed?
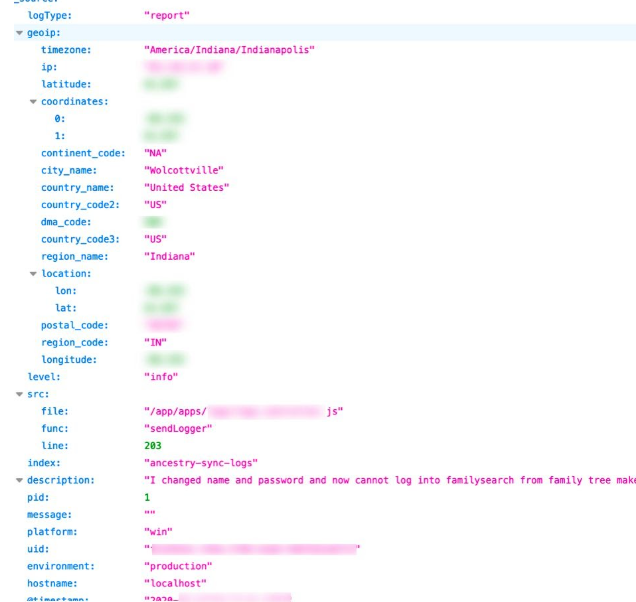
The misconfigured ElasticSearch server exposed information of approximately 60,000 users (including duplicates) and complaints sent to customer support and extremely vulnerable data about their physical location. As the company is based in the US, most of its users could be identified as US residents.
The information exposed in the leak includes:
- Email address
- Internal system user IDs
- Subscription type and its status
- Refunds (if applicable)
- Timestamps
- User location data, including geolocation coordinates and cities
- IP address
- User support messages
- Technical data, such as error logs
What Are the Risks and What Can I Do to Protect Myself?
The leaked data could have given cybercriminals and scammers access to user personal information, putting many people in great risk of having their credentials used against them. These threats include:
- Spam and phishing: Cybercriminals often use leaked personal data to create more believable phishing emails. This readily available private information could assist bad actors in establishing trust and encouraging clicks on phishing links and malware downloads. The more data is exposed, the more trustworthy a phishing email will be able to seem due to increased personalization of it. Unfortunately, by clicking on links or attachments in the email can have catastrophic results, like downloading various types of malware programs or even allowing attackers free access to your accounts.
- Fraud: Any leak that exposes even small parts of personally identifiable data, can assist in successful fraud attempts. As the exposed information revealed various private details, like user locations and email addresses, it could give attackers an opportunity to easily scam their victims. The exposed data could also possibly be correlated with external resources. This means that any information revealed in the MacKiev leak could be linked with data involved in another online leak or different data source. For example, attackers could use the email addresses exposed in this breach to find additional information about their victims and use it against them.
- Technical vulnerabilities: The leak exposed technical details about the system’s backend, which could help attackers leverage multiple cyberattacks on Software MacKiev and its associated companies. That way cybercriminals can steal additional user data, infect the system with malware, or even take complete control over parts of the systems.
- Business espionage: The leaked comments and complaints sent to MacKiev and Ancestry give their competitors an opportunity to target the unhappy users. This is a great chance for other companies to personalize and customize adverts, emails, and mail to encourage Family Tree Maker customers to switch to a different platform.
It’s important to remember that these are only some of the risks that come with leaks of such magnitude. The list is not exhaustive and cybercriminals are constantly creating new ways of attacking anyone on the Internet. Fortunately, regardless of whether your data was involved in the Family Tree Maker leak or not, there are many ways you can protect yourself.
Always be mindful of what details you share online. If possible, provide only the bare minimum when setting up new accounts or making any purchases. Remember, once your data is saved on any website, it’s likely to be involved in a site leak or breach.
Most email programs are now able to recognize and block phishing emails before they even reach you, but some attempts can still land in your inbox or spam folder. Avoid opening any attachments sent from seemingly trustworthy accounts that you weren’t expecting. Phishing emails usually use clever scare tactics to trick you into clicking on a malicious link or downloading malware. If in doubt, check with the company the email seems to be sent from — even a quick phone call can confirm how genuine the message is.
Very often, data leaks expose user IP addresses which can then be traced to find your location. However, not many people realize you can easily mask or change your device’s IP by connecting to a VPN. This will allow you to tunnel your internet connection through a VPN server of your choice. Such a connection will provide your device with the server’s IP address making it impossible for anyone to track your physical location.
Finally, you should consider getting antivirus software to increase your device’s internal security. It could greatly assist in immediately recognizing malicious programs on its system, including viruses, trojans, and spyware. Many antivirus programs come equipped with technology that reads through emails searching for phishing attempts. Oftentimes, you can get great discounts on popular antivirus software or even subscribe to a free provider. Either way, the added security will efficiently protect your data.
Who Is WizCase and Should I Trust It?
One of the leading companies in online security news and VPN reviews, WizCase provides its readers with regular updates on how to stay safe and anonymous online. Our white-hat hackers regularly uncover data leaks and breaches, including vulnerabilities in the hospitality industry and medical leaks, and report them directly to companies involved to ensure they are secured before we publish any information about it. Together, we’re working towards making the internet a more secure space gaining the trust of thousands of our regular readers across the world.
Editor’s Note: Following Ancestry’s reach out, we wanted to clarify some points —
- The Family Tree Maker software can use data that users have downloaded from their Ancestry accounts. But, presently, there is no association or connection between the companies Ancestry and MacKiev.
- There was no evidence of a breach to Ancestry’s own system.




Leave a Comment
Cancel