Data Leaks in Online Education: Almost 1 Million Records Exposed
WizCase discovered multiple data leaks affecting numerous e-learning websites around the world. The leaks exposed personal information, such as emails, passwords, and full names, of almost 1 million users, many of which were underage. As the data was stored in misconfigured and unencrypted Amazon S3 buckets and other types of servers, anyone could access it without any form of authentication.
What’s Happening with eLearning Companies?
eLearning websites have been growing in popularity as they provide an entertaining and fun way to learn for children and teenagers. However, as some of these platforms are used predominantly by underage users, it’s important for companies to acknowledge the severity of appropriate data protection.
Children’s data protection should be the utmost priority for every company collecting vulnerable information of users under the age of 18. Unfortunately, it seems that not all businesses understand the seriousness and dangers of mishandling such information.
Our cybersecurity team, led by Avishai Efrat, found 5 breaches from separate companies across the globe. The vulnerable data was stored and managed on 4 Amazon S3 buckets and an ElasticSearch server. Unfortunately, due to certain misconfigurations, they became open to the public and available for anyone to view.
The exposed data included:
- Full names
- Email addresses
- ID numbers
- Phone numbers
- Home addresses
- Date of birth
- Specific course and school information
Whose Data Was Exposed?
WizCase hacktivist team uncovered multiple open servers from 5 popular educational platforms.
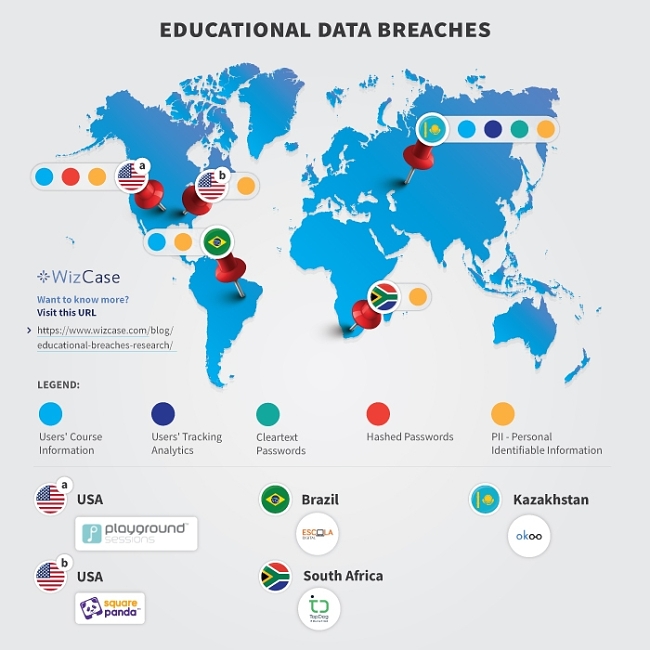
1. Escola Digital — Online Digital Courses
- Location: Brazil
- Database Size: 15MB
- Exposed Records: Around 75,000
- Whose Data Leaked: Students and Teachers
- Server Type: Misconfigured Amazon S3 bucket
Escola Digital is a Brazilian website which offers digital courses. It’s predominantly aimed at children and young people, but can also be used by adults.
The exposed bucket, alongside the specific data, names, and logos stored within the files, showed a clear connection to the Escola Digital website. However, the breach didn’t include the most recent information — the data found consisted of files collected in 2016 and 2017.
The misconfigured bucket contained several CSV files with user’s personal identifiable information (PII), such as full names, email addresses, Brazilian ID numbers, school names, position held (i.e. student or teacher), phone numbers, home addresses, and links to certificates of users who finished Escola Digital courses.
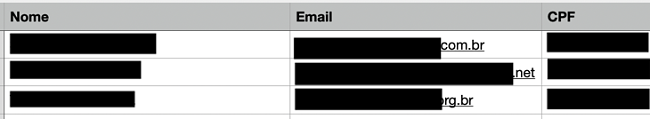
2. MyTopDog — Children-Orientated Study Platform
- Location: South Africa
- Database Size: 40-50MB
- Exposed Records: Over 800,000
- Whose Data Leaked: Students
- Server Type: Misconfigured Amazon S3 Bucket

MyTopDog is an online website with personalized learning courses for school-aged children. It allows each student to study at their own pace while providing multi-sensory lessons, practice tests, and interactive games.
The misconfigured Amazon S3 Bucket contained data linked directly to the platform, as well as documents related to MyTopDog’s official business partner, Vodacom School. According to the folder structure, the data held within the bucket seems to have been saved for email campaigns.
We found 4 types of data exposed:
- 50,000 entries in an Excel file with PII of users who registered in 2016-2017, but are described as inactive on the platform
- 14,000 entries within the same Excel file with data of users who registered in 2016-2017 and are described as active on the platform
- A CSV file with nearly 800,000 user entries with their full names, cell phone numbers, date of birth, gender, and guardian contact details. The file also stored several backups of the exposed information from December 2019 to March 2020.
- A PDF file that seems to be a part of a business agreement between MyTopDog and Vodacom, alongside confidential Vodacom files.
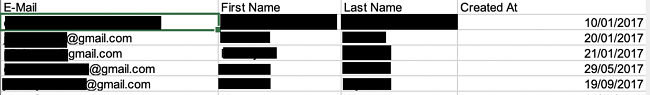
3. Okoo — Online Learning Platform for Children
- Location: Kazakhstan
- Database Size: 418MB
- Exposed Recordss: Almost 1 million entries about users’ activity on the platform and analytics, including 7,200 records that held Personally Identifiable Information
- Whose Data Leaked: Students and Administrative data
- Server Type: Open ElasticSearch server
Okoo provides an e-learning programming platform for students in Kazakhstan. The courses are available in Russian and can be used for both individual learning as well as group classes.
Approximately 7,200 user records exposed in the leak revealed PII, like full names, cleartext passwords, email addresses, completed courses, and quiz scores. However, almost 1,000,000 records found included users’ interaction with the site, such as quiz participation, results, analytic tracking of users, and general course information.
The vulnerability also exposed an entry that seemed to include admin credentials, however those weren’t tested for ethical reasons. This poses multiple threats to the site and its users as attackers could use administrative login details to manipulate Okoo content and easily access extensive user data.
4. Square Panda — Educational Phonics Learning Online System
- Location: USA
- Database Size: 1MB
- Exposed Records: Around 15,000
- Whose Data Leaked: Parents and Teachers
- Server Type: Misconfigured Amazon S3 bucket
Square Panda is a virtual platform launched to help children learn how to read and write through various online games and multisensory kits available for home use. The site provides a cloud-based monitoring system that allows parents and teachers to track everyone’s progress and plan next learning steps.
The information stored on the misconfigured Amazon S3 bucket correlates directly to this American company. Moreover, the bucket also held PDF files with the Square Panda logo on them.
Around 15,000 entries were found in an exposed CSV file stored within the open bucket. The file held a backup of users’ personal data, including full names, email addresses, phone numbers, and their account type (parent or teacher).
5. Playground Sessions — Virtual Piano Lessons for Everyone
- Location: USA
- Database Size: 1.2MB
- Exposed Records: Around 4,100
- Whose Data Leaked: Platform Users
- Server Type: Open Amazon S3 bucket

Playground Sessions Inc. is an American website which offers virtual piano lessons. Endorsed by many celebrities, such as its co-founder Quincy Jones and Harry Connick Jr, the platform provides fun and interactive music experience for users of all ages.
The company’s misconfigured Amazon S3 bucket was used to store files with information that correlates directly to what Playground Sessions does. We found details on the available lessons, practice records, and more. We also discovered another related open bucket used to store various song titles.
The breach exposed users’ private information, including their full names, usernames, emails, hashed passwords, and app scores earned through piano lessons. The CSV file with the leaked data seems to be the platform’s backup from 2011-2013.
What Are the Consequences of These Leaks?
As many users whose data was leaked aren’t active on the sites anymore, they’re less likely to realize these companies still have their information. However, it’s still possible that their data can be used to aid in various types of online crimes. These dangers are even bigger since many of the users affected by the leaks are children and young people.
There are several possible dangers that could arise if an attacker obtained the vulnerable data. These include, but are not limited to:
- Identity theft and fraud: Hackers can easily perform successful identity theft and fraud if equipped with PII leaked from these websites. Such dangers are especially high when databases store vulnerable information, like home address, full name, and ID numbers.
- Phishing and scams: As many users of the sites involved in these breaches are underage, it’s easier to target and trick unsuspecting victims with phishing emails and phone frauds. Many of the exposed details would aid in establishing trust and creating believable scams.
- Stalking: Predatory behavior is a common online threat, but it’s increasingly possible when data leak involves children’s contact details and personal information.
- Blackmail: The leaks exposed educational statuses of thousands of users, alongside their names and email addresses. This provides attackers with sufficient information to aid in blackmail if a user or their guardian wants to keep this information a secret. Many students might also feel insecure about their test results and wouldn’t want this information to be publicly available. Revealing this personal data could damage a student’s reputation and even lower their chances of a prosperous educational future.
It’s clear to see that whenever you decide to share your personal information online, you lose all control over who can access it. Regardless of extensive privacy protection policies and deleting your accounts, that data can still be kept and stored without your knowledge. And if it still exists on the server, it’s always possible it’ll be involved in a data leak.
Here’s How to Protect Your Private Information
You can never be 100% confident your data will be kept safe, no matter how trustworthy a website may seem. Luckily, there are many steps you can take to protect your personal information online and prevent it from accidental server leaks.
1. Regularly Check Account for Unusual Activity
Monitoring your accounts for unusual activity is the best practice to see if your data has been stolen. The changes might be small and almost unnoticeable at first, but pay extra attention even to the slightest details. Should you find something you don’t recognize, report it and, if possible change your password or add two-factor authentication.
To add an extra layer of protection, always use strong passwords and store them in password managers.
2. Avoid Opening Links Attached in Suspicious Emails
Unless you’re fully confident the email was sent by one of the educational platforms, don’t click on any attachments in the message. Very often, they will direct you to malicious sites or will download malware on your device straight away.
If you receive an unexpected email, check for minor variations in the sender address — it may appear genuine at first, but upon further inspection differs from the original. Additionally, contact the company it appears to be from and confirm the source of the email. Only then, you can safely open the links and attachments.
3. Never Share Additional Personal Information Online or on the Phone
Scammers are most likely to contact you in a way that doesn’t require additional form of identification, for example through emails or phone calls. That’s why it’s crucial to refrain from giving any information to someone you don’t know or can’t fully identify. Remember that reputable institutions, like banks or insurance companies, would never request personal details in such unsecure ways.
Should you doubt if the person is genuine, make sure to check with the actual company to verify the nature of the call or email before giving your private data.
Why Should I Trust WizCase?
WizCase is an online cybersecurity leader. We’ve gained trust from readers all over the world through consistently providing top quality tips on improving your internet safety. Our team regularly uncovers data breaches, including previous data security issues in the education sector and medical data leaks.
In order to protect the exposed user data, we always contact the vulnerable companies prior to publishing each report. Unfortunately, despite our efforts, companies often choose to ignore our warnings. In this case, we contacted local Cyber Incident Response Teams (CERT) in each country, which assisted us in securing some of the leaks and reaching out to the companies. We hope that publishing this report will encourage the companies involved to secure the breaches.




Leave a Comment
Cancel