How HR Leaders Can Remotely Secure Their Mobile Workforce
Remote work is here to stay. Telecommuting, flex jobs, working from home, virtual office teams. Whatever people call it, we know that flexible work is in higher demand than ever.
That’s why it’s so important for HR managers to prepare themselves with the best practices in managing the host of new considerations that come with remote work. You need to keep your remote workforce productivity high, while still protecting the security and privacy of the company. That includes anyone who could be susceptible to a data breach; executives, workers, clients, and customers.
Remote work presents new opportunities, but also new challenges. It’s a balance that your company may not have much experience offering. If your colleagues are reluctant to set up and maintain a remote work option, keep reading.

Isn’t Cybersecurity a Job for IT Managers?
In the case of remote work security, not entirely.
People tend to think of telecommuting is a job for IT professionals. It’s about wireless networks and cloud-based productivity services, antivirus software, and screen-sharing capabilities.
What’s in a Name?
As an HR professional, you give employees the tools needed to advance and succeed.
You serve as a gatekeeper for personal information, and enforce compliance with company policies and organize training. HR specialists know about employment law and have an excellent grasp on company security policies, data retention regulations, and several other factors that IT professionals may overlook. This is the expertise needed for a remote work environment to succeed.
Remote-work companies across the globe are discovering how important it is to partner their IT efforts with HR expertise.
When remote work programs have failed in the past, it has been mainly due to human errors. Factors like improper personnel training and management of employee personalities played the largest role. The lack of communication and collaboration between HR, IT, and individuals can spell disaster.
In other words; without HR, remote work doesn’t work.
Is Remote Work Necessary or Just Another Headache for HR Managers?
Conventional wisdom suggests that companies willing to adapt and grow with technological change will outpace competitors who are stuck in the past.
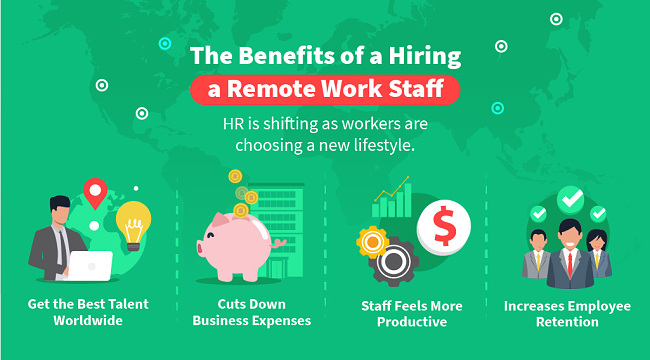
Exploring the Benefits
Maybe your local workers want the flexibility to work from home part-time? Or perhaps you’re looking to include out-of-state professionals who don’t need a brick-and-mortar home to be part of your team.
Many HR professionals are tasked with helping save the company money on operational costs, which can be achieved in part through telecommuting. Maybe you’re worried about talent retention because of competitors who offer more attractive work options?
Whatever the motivation, remote work is one of the most cost-effective ways to leverage a diverse talent base while keeping employees more productive and happier.
Managing Personalities, Behaviors and Emotions
Human Resources professionals understand workplace psychology.
Remote work involves plenty of personality-based and behavioral components. For example, because research shows remote workers are happier, you can assume happier employees are committed to their jobs, which means remote workers should have a strong desire to protect the benefits of working from home by protecting their employer’s data.
Remote workers are grateful for the opportunity to save time and money working from home, so they are innately more compelled to abide by HR and IT guidelines for cybersecurity. Take advantage of that worker gratitude and use it to enforce careful remote work guidelines for your company.
Of course, there are other psychological considerations. Many HR professionals find they need to help their workers understand the necessity and value of securing records. Employees often take for granted that the company will protect its interests, so workers are not devoting much time to thinking about building security or fire suppression or cybersecurity.
Likewise, while working remotely, workers are in the comfort of their homes and may have reminders of their connection to the company. Studies show that while remote workers have less work-related stress, they may need more motivation to reinforce the shared responsibility to safeguard the data and equipment owned by the company.
Remote Work Data Breaches – Cautionary Tales to Learn From
Remote working has been around, to varying degrees, since IBM started experimenting with it in the late 1970s. That means there’s plenty of data about best practices and some severe complications you could run into if your remote work policy isn’t robustly enforced.
The University of California, Santa Cruz, cataloged several security breach examples – from stolen laptops taken from an at-home Veterans Affairs worker to virtual data theft from remote workers who lacked the proper VPN and antivirus infrastructure.
By the way, the VA employee whose laptop was stolen resulted in 26.5 million confidential records being compromised. That’s the impact one mistake can have.
Security experts report that fully one-third of American and European companies have suffered data breaches, mainly due to lackluster cybersecurity protocols and training for remote workers.
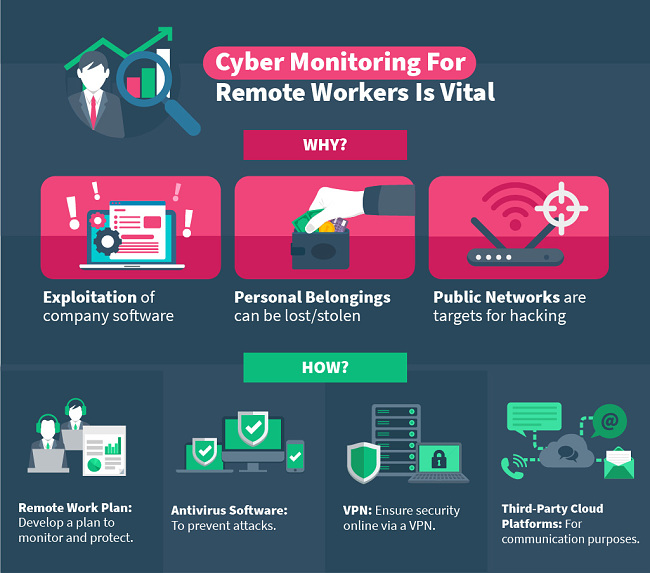
The Potential Risks
- Public networks – more vulnerable to attacks
- Personal devices – corruptible, and can be lost or stolen
- Malware, phishing, etc. – without a single dedicated network, exploitation is more achievable
Fortunately, for any digital problem, there is a digital solution.
Develop a Remote Work Plan and Enforce It
It can be difficult enough for HR directors to manage onsite employees, never mind those working remotely.
However, when employees have escaped the watchful eye of in-house firewalls, hardware, and software, how can a business ensure its data and its communications are safe and secure? The answer lies in a combination of traditional personnel technology policies and using reliable tools that simplify security and privacy.

1 Analyze and Categorize Your Company’s Remote Work Needs
- Do your workers need to bring in physical backups of data, or can it all be cloud-based?
- Are your workers mobile all week, or part-time?
- Will you provide workers with all devices (laptops, phones, tablets)? If not, do you have an agreement to install VPN and other software on personal devices?
- Will you outline how to run the office and the tools that should be used to ensure security?
- How will you comply with OSHA safety requirements and worker’s compensation incidents, whether for physical harm or damage to personal equipment used for work?
2 Identify the Eligible Workers
Not every type of employee role can operate remotely. Think carefully about who should be allowed to work virtually and establish clear criteria, so employees know their options.
3 Train and Retrain
Cybersecurity evolves frequently. With the ever-changing risks to digital safety, your employees need to be appropriately trained and updated regularly to stay ahead of the latest privacy and safety concerns.
4 Manage Equipment Use
Decide how much equipment, tech devices, software licenses, and office furniture your company is willing to provide offsite workers.
- Will you institute a Bring Your Device (BYOD) Policy? If so, consider the pros and cons.
- Will you require remote workers to purchase their equipment insurance or cover it under your company’s policies?
- What about antivirus software?
- Will your company contribute toward their home electric or Internet bill?
5 Cybersecurity Tools
By collaborating with your IT department, you’ll be able to determine the best tech-based tools to keep your company’s and employees’ data secure and private.
- VPNs

VPNs establish an encrypted connection between your worker’s devices and your company’s private servers. A VPN is vital for protecting confidential and proprietary information. It is your best tool for preventing unauthorized users from looking at company data and transactions.
- Antivirus Software
A fundamental tool. Preventing data theft, browser hijacking, ransomware takeovers, and all manners of cybersecurity threats is vital.
- Third-Party Cloud Platforms
Communication and productivity tools are vital. To streamline project management and remain connected for any communication needs, it’s essential to offer the appliances and protocols for regularly connecting with remote workers.
Work with your IT department to take advantage of custom security settings on productivity apps and websites that remote workers may use. Educate employees about the dos and don’ts of online safety.
Platform Examples:
- Microsoft Office 365
- Google Suite
- Slack
- Skype
- Asana
- Trello
- Basecamp
- VNC desktop-sharing software
Enforcing Your Comprehensive Remote Work Policy:
Communicate the Rules
A well-designed and executed remote work plan will mitigate any risks while maximizing benefits. When developing a remote work/telecommuting policy, keep in mind that these guidelines should be considered in addition to existing employee contract and hiring agreements.
You don’t have to overhaul current work policies and procedures completely, but if any dimensions of remote work appear to violate your standard work agreements, compromises and exceptions need to be explained explicitly.
Plan for worst-case scenarios. Make sure employees have guides for standard operating procedures of day-to-day considerations, and provide them with an emergency plan and contact list in the event of a breach.
Include the following in your remote work policy:
- Secure password requirements
- Communication etiquette
- Mandatory VPN use on all devices
- Confidential information handling procedures
- Required browser updates
- Company-approved or provided antivirus software
- Frequent and compulsory conferencing with the office to report progress or security concerns
- Prohibit the use of public Wifi. Mobile workers who use cafes and other hotspots are more vulnerable to the unsecured nature of public internet signals
- Require firewalls to prevent access to risky or time-wasting content like social media or streaming sites
- Use encrypted email services
- Install encrypted disc drives
- Establish policies for hard-copy document shredding
- Require employees to have adequate home security and items like safes and locked drawers
- Remind employees to be aware of not leaving devices unattended in public places
- Install GPS tracking software and remote locking abilities on mobile devices
Final Thoughts
Companies offering remote work options have, by definition, decentralized many of their operations. To take back some of the control lost to virtual work environments, it’s important to standardize remote worker behavior to comply with company policies by properly training and equipping them to protect your company.
Implementing a system of virtual teams consisting of remote workers has proven beneficial for both companies and their employees. However, the proper management of a remote work policy requires careful consideration and ongoing effort. It is not a process that can be simply established and then ignored.
Don’t rush developing your remote work plan. Treat it like any cybersecurity protocol or any other workflow of your company’s business model. Careful planning takes time.



