Data Breach: Online Culinary Website Exposed Private Information of Thousands of French Users
WizCase has found an open Elasticsearch database from GuyDemarle, an online platform for selling culinary equipment. The platform also works as a social site where people can interact, follow popular users, share recipes, and save them to their account for later use. The server contained personal user data including email addresses, full names, and more from over 85,000 registered users.
What’s going on?
Our team of hacktivists, led by security expert Avishai Efrat, located an unsecured database server used to store GuyDemarle user data. As the server didn’t have accurate security settings turned on, it revealed the private information of over 85,000 active users on the website. The data could be viewed by anyone with access to a simple internet browser due to a lack of server encryption or password protection.
The leaked data exposed a lot of the users’ personal information, such as:
- User’s full name
- Registered IP address
- Email address
- Username
- Profile type chosen at account creation (“classic” or “advisor”)
- Serial numbers of iCooking and beSave products purchased by each user
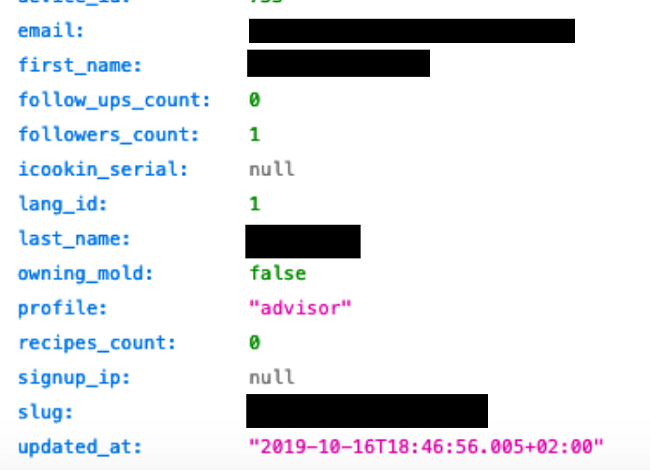
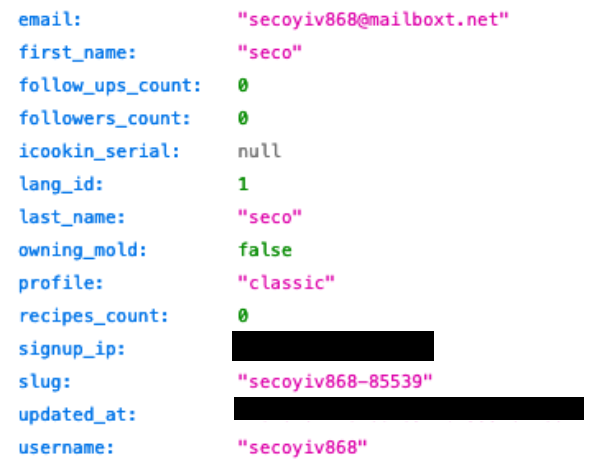
This vulnerability affected both existing users and those who are new to the site. To check what data was visible and if the leak was still active, we registered as a new user through the GuyDemarle website.
As a result, our details appeared immediately on the open server, exposing all of our information. It revealed our email address, full name, number of followers, IP address, and whether we purchased iCooking and beSave products.
Whose Data is Available and What Are the Consequences of Such a Leak?
The data leak put over 85,500 users’ vulnerable information at risk. As the server was used to store live information and not backups or tests, the number of exposed users kept growing during our research. As the GuyDemarle website displays live numbers of existing users, we also noticed that it matched the amount of data in the database at any given time. This shows that the data is synced and the server was used to store live information about the website and not backups or test data.
Additionally, we discovered that many users had their data saved in different locations on the server. This is because their personal information was saved alongside the data about the user’s recipes activity. As the data was stored in all of the recipe entries as well as in user data entries, we could easily correlate users with their online activity on the website.
Luckily for users, it seems that no payment details were stored on the server. Instead, the only purchase information available was the serial numbers of iCooking and beSave products bought by each user. This showed us who bought the smart cooking appliances, such as iCooking robot, or the eco-friendly food containers.
However, this data breach still left GuyDeMarle users vulnerable to online scams and threats, such as:
- Phishing scams: With direct access to specific private information, including usernames, recent purchases, and whether a person has an account on the website, attackers can target users with convincing and seemingly trustworthy phishing emails. This can encourage clickthroughs to malicious links included in the email which in turn allows hackers to steal more vulnerable data or even install malware on users’ devices.
- Fraud and identity theft: Hackers can use leaked PII details in fraudulent activity to disguise themselves as someone else. With personal details including full name and email address, attackers can quickly gain credibility without raising suspicion. While the lost data may not be enough for most identity thieves, it still puts users at risk of having their information stolen.
How Did it Happen and What to Do Now?
As Elasticsearch is designed to be installed on a company’s internal network, by default it doesn’t require any form of authentication before allowing access to the database. If this setting isn’t manually changed after installation, it could allow anyone who accessed the Elasticsearch server to browse through GuyDeMarle’s users’ data. Moreover, the vulnerable server had no security settings, such as whitelisting or firewall, enabled.
If you are a GuyDeMarle user, you should take extra precautions to protect your personal data. Stay vigilant and aware of any unusual activity appearing in your emails or other online accounts as this could indicate identity theft.
On top of that, never provide additional profile information in response to suspicious emails. Remember that no online companies, including GuyDeMarle, would ever request any personal data through an email.
Report any online activity you don’t recognize and, if possible, change your passwords and set up two-point authentication.
Who is WizCase and Why Should I Trust You?
WizCase is a leading cybersecurity website visited regularly by millions of users. Translated into 30 languages, it has gained the trust of people all over the world. Our incredible team of security experts has discovered and exposed a number of data breaches, including dating app leaks and vulnerabilities in many popular webcams. Together we work towards making the online space more secure for everyone.
We always contact the companies involved in data leaks prior to publishing articles. This gives them a chance to secure users’ data and fix their servers. After receiving no response from the GuyDemarle team, we passed the information about the leak to the French Cybersecurity Emergency Response Team (CERT). They then notified the company and helped secure the vulnerable server.



